Chaotic-hash structuring method based composite non-linear digital wave-filter
A digital filter and construction method technology, applied in the field of information security, can solve the problems of destroying the global uniform distribution characteristics of PWL, the hash results are not evenly distributed, and it is difficult to resist statistical attacks, etc. It is easy to expand, realize software and hardware, and realize simple Effects of fast, resistant linear analysis
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
[0025] The general method of the chaotic hash construction method based on the composite nonlinear digital filter of the present invention is:
[0026] 1) Initialization:
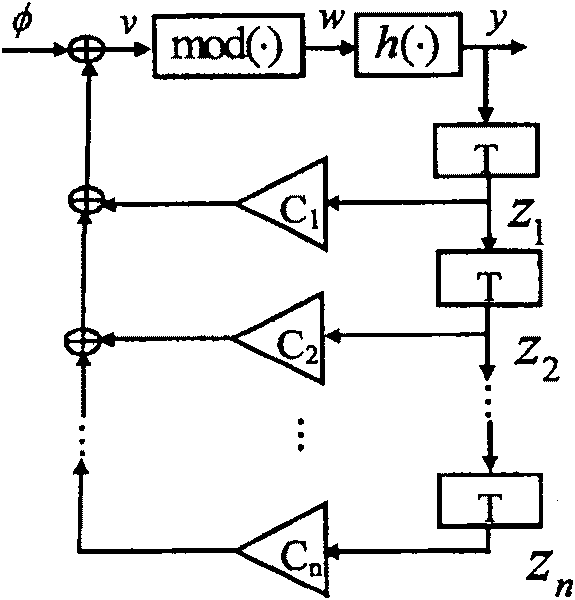
[0027] figure 1 Show: an n-dimensional nonlinear autoregressive digital filter can be expressed as Where φ∈(-1,1) is the initial input signal of the filter, {z 1 ,z 2 ,…z n }∈(-1, 1) is the initial state of the filter, {c 1 , C 2 ,...C n } Is the filter coefficient, T is the unit delay, h(·) is the nonlinear transfer function, mod(·) is the hardware overflow function, y is the output of the filter. When the filter satisfies the Kelber condition, that is, it satisfies the following three conditions: ①Coefficient |cn|>1, ②The absolute value of the characteristic root of the filter is not 1; ③The nonlinear transformation h(·) has uniform distribution characteristics; the output y of the filter is ergodic and maintains an n-dimensional uniform distribution, and the filter becomes a n Dimensional chaotic system....
Embodiment 1
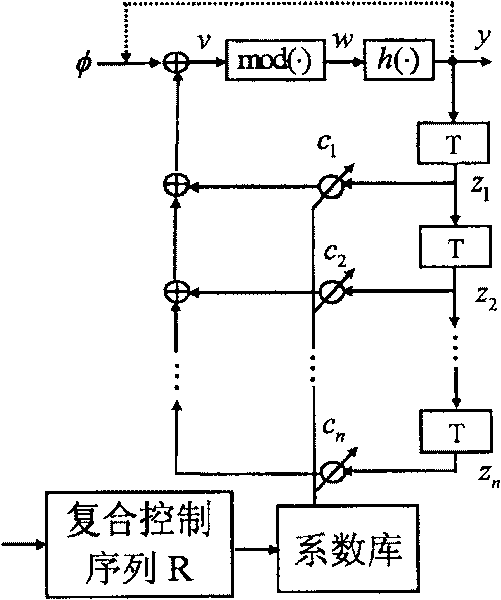
[0035] n=2-dimensional nonlinear digital filter, k=2 sets of coefficients pre-stored in the coefficient library, and a chaotic hash construction method when the hash length L=128.
[0036] 1) Initialization:
[0037] n-dimensional autoregressive nonlinear digital filter, n=2, p=1, parameter library pre-stored k=2 p =2 sets of coefficients {c 0 =[3.57, 4], c 1 =[5.7,7]}, the hash length L=128 bits, the initial value of the filter is the key SK={φ 0 ,z 1 ,z 2 }={φ 0 = 0.5648, z 1 = -0.564, z 2 =0.679}, the initial hash value Nonlinear mapping Hardware overflow function Quantization function of filter output To simplify the length, take the plaintext M′ to be hashed = {0101110101}, and the length of the plaintext M filled with zeros is That is, s=2, and the filled content is Group M according to the length of 128 and mark it as M=(M 1 , M 2 ),
[0038] 2) Hash value generation:
[0039] ①The first paragraph of plaintext M 1 The hash value generation: will With M 1 XOR, get compou...
Embodiment 2
[0050] n=3-dimensional nonlinear digital filter, k=4 sets of coefficients pre-stored in the coefficient library, and a chaotic hash construction method under the condition that the hash length L=256.
[0051] 1) Initialization:
[0052] n-dimensional autoregressive nonlinear digital filter, n=3, p=2, parameter library pre-stored k=2 p =4 sets of coefficients {c 0 =[2.53, -0.63, 2], c 1 =[5.1, 1.2, 5], c 2 =[-3.64, 4.23, 3], c 3 =[0.75, 3.24, 4]}, the hash length L = 256 bits, the initial value of the filter is the key SK = {φ0, z 1 ,z 2 ,z 3 }={φ 0 = 0.5648, z 1 = -0.564, z 2 = 0.679, z 3 =0.132}, the initial hash value The nonlinear mapping h(w), the quantization function T(x) output by the filter, and the hardware overflow function mod(.) are all the same as in the first embodiment. To simplify the length, we also take the plaintext M'to be hashed = {0101110101}, and the length of the plaintext M filled with 0 is That is, s=2, and the filled content is Group M according to leng...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com