Method and mobile terminal for securely transmitting a mobile subscriber identifier
A mobile user identification, mobile terminal technology, applied in security devices, radio/induction link selection arrangements, electrical components, etc., can solve problems such as theft
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
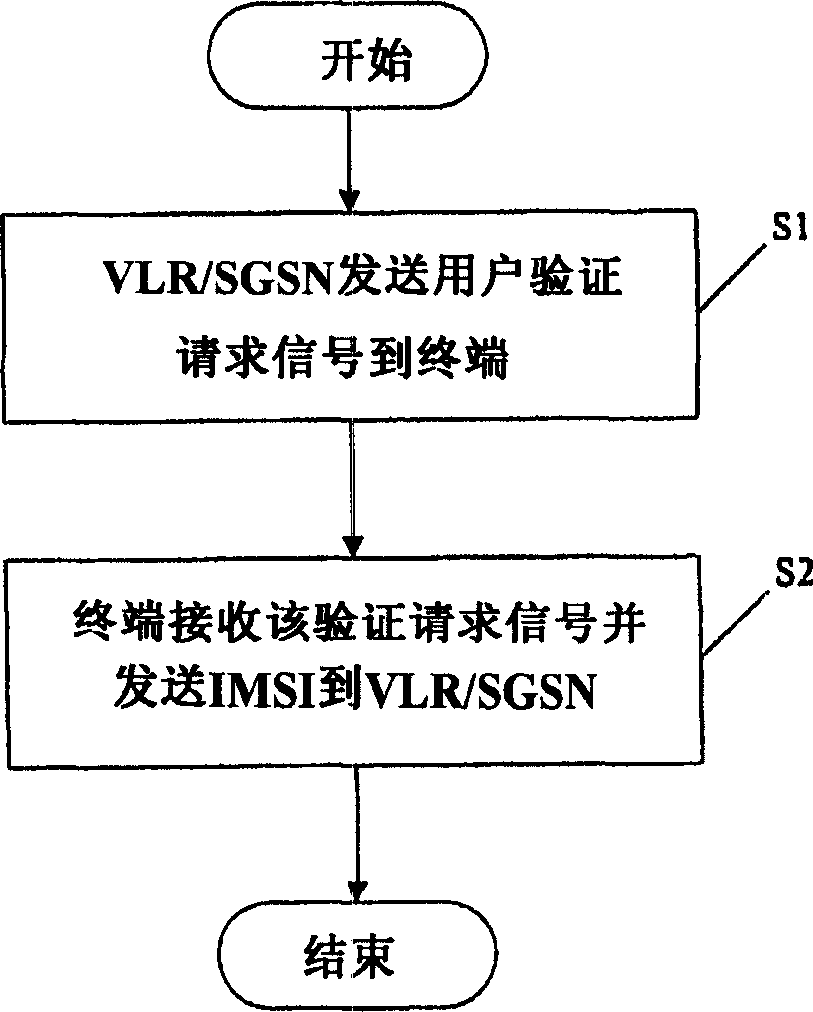
[0027] The inventors herein disclose a method of transmitting a mobile subscriber identifier with improved security using a combination of a public key and a secret key (or private key).
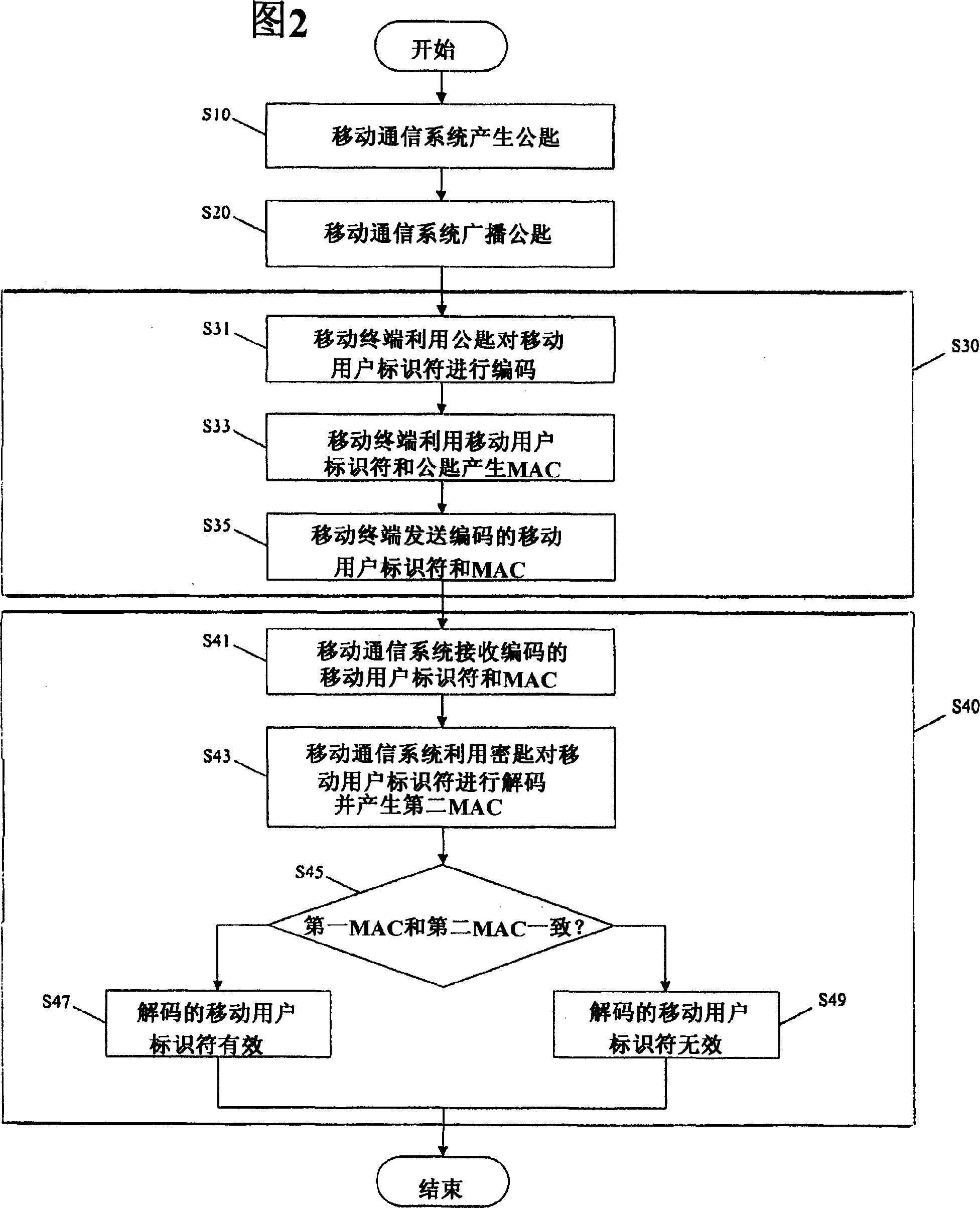
[0028] The method for securely sending a mobile user identifier according to an embodiment of the present invention is described below with reference to FIG. 2 .
[0029] The method shown in FIG. 2 is roughly divided into two parts: an encoding / transmission part (step S30) and a reception / decoding part (step S40). More specifically, the method shown in FIG. 2 includes encoding the mobile user identifier by the mobile terminal and sending the mobile user identifier to the mobile communication system (step S30), and decoding the mobile user identifier by the mobile communication system and Its validity is determined (step S40).
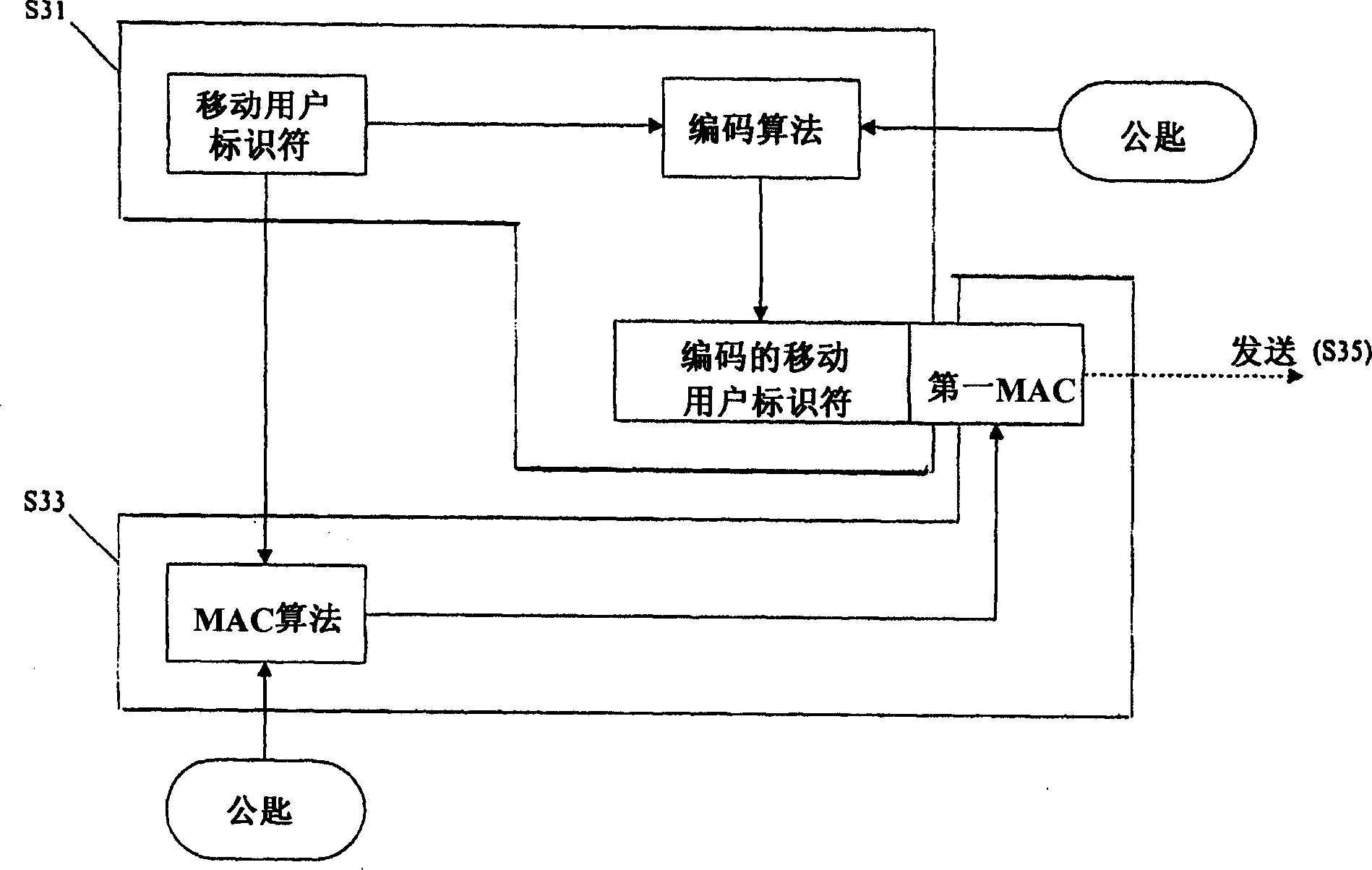
[0030] image 3 The encoding and sending process of step S30 is shown in more detail, and Figure 4 The decoding and validity determination process of step S40 is ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com