Security element comprising a support
A technology of security elements and security files, applied in the field of security arrangement, can solve problems such as time-consuming, troublesome, and non-protective security features for users, and achieve the effect of simple and fast authenticity verification
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
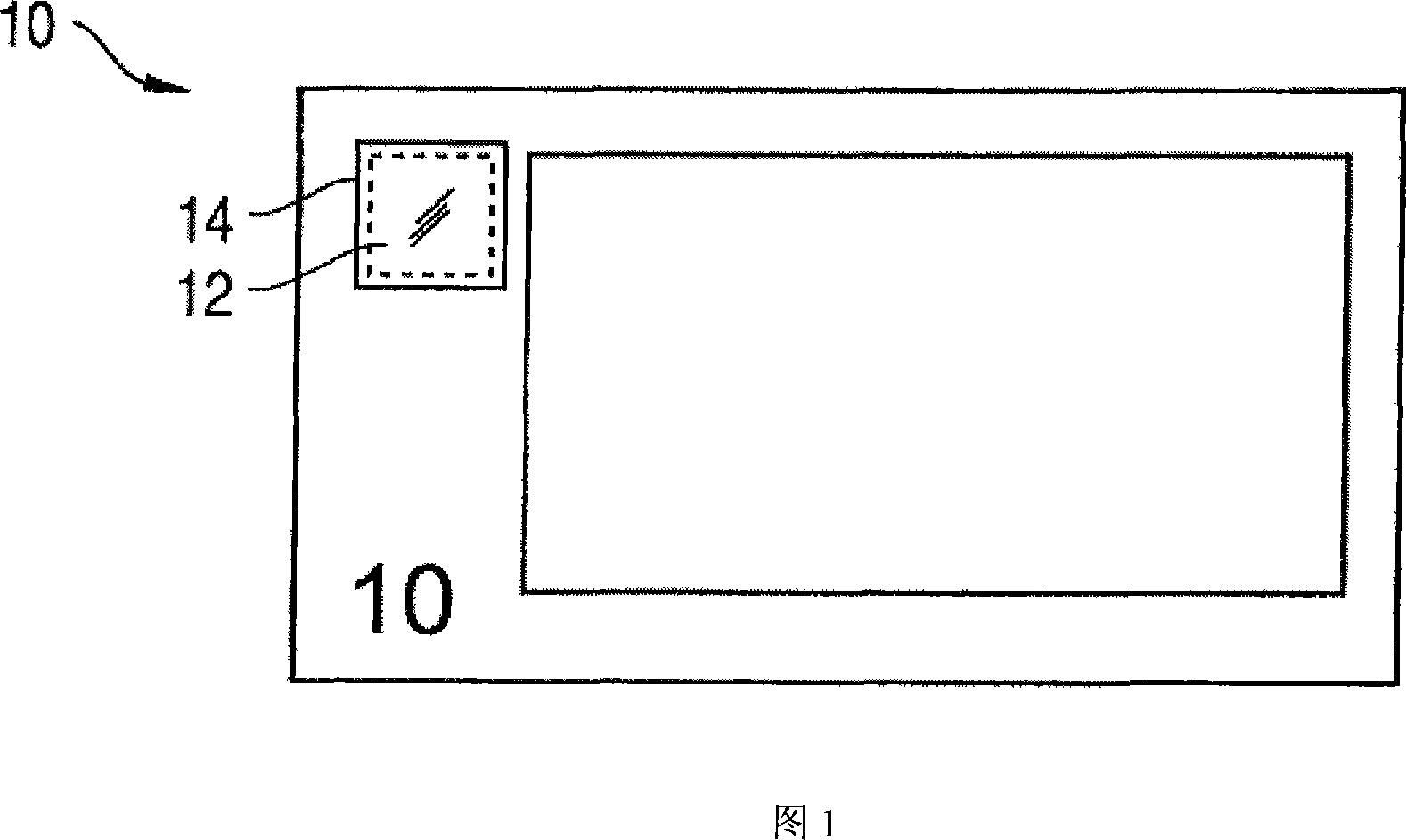
[0043] FIG. 1 is a schematic illustration of a banknote 10 , wherein the see-through region 12 is located in a subregion of the side of the banknote 10 . The see-through area 12 can be located, for example, in a through-slot or a transparent sub-area of the banknote 10 . According to the invention, a transparent security element 14 is arranged in or beyond the see-through region 12 .
[0044] In an exemplary embodiment, the security element 14 in the banknote 10 exhibits a first visible image on its non-patterned and completely colorless transparent surface when illuminated by transmitted light. In other embodiments, the security element can also be designed with a specific, light-toned, always-present color image when illuminated with transmitted light.
[0045] If the security element 14 in the banknote 10 is against a predetermined background, a second visible image will appear on the security element 14 which is substantially different from the first image. This appare...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com