System, apparatus and method for authentication
An authentication and algorithm technology, applied in the field of authentication systems, can solve problems such as potential safety hazards and attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0140] The invention provides a system, device and method for authentication. A detailed description will be given below in conjunction with the accompanying drawings.
[0141] As shown in FIG. 6 , it is a flow chart of the first embodiment of the authentication method of the present invention.
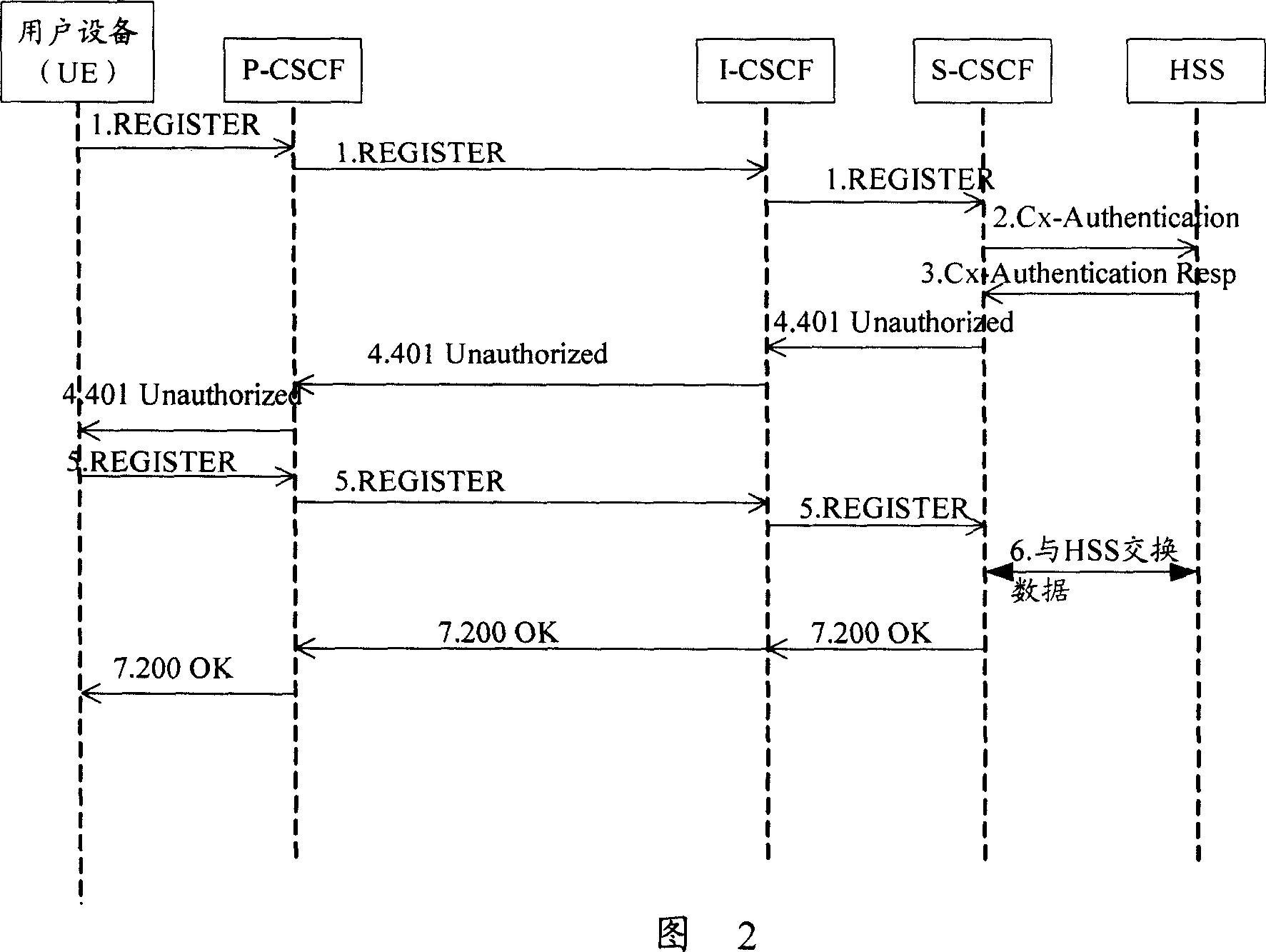
[0142] Step 1: the user terminal (UE) sends a registration request to the call session control function (CSCF), requesting to register to the IMS network;
[0143] Step 2: CSCF requests authentication data from Home Subscriber Server (HSS);
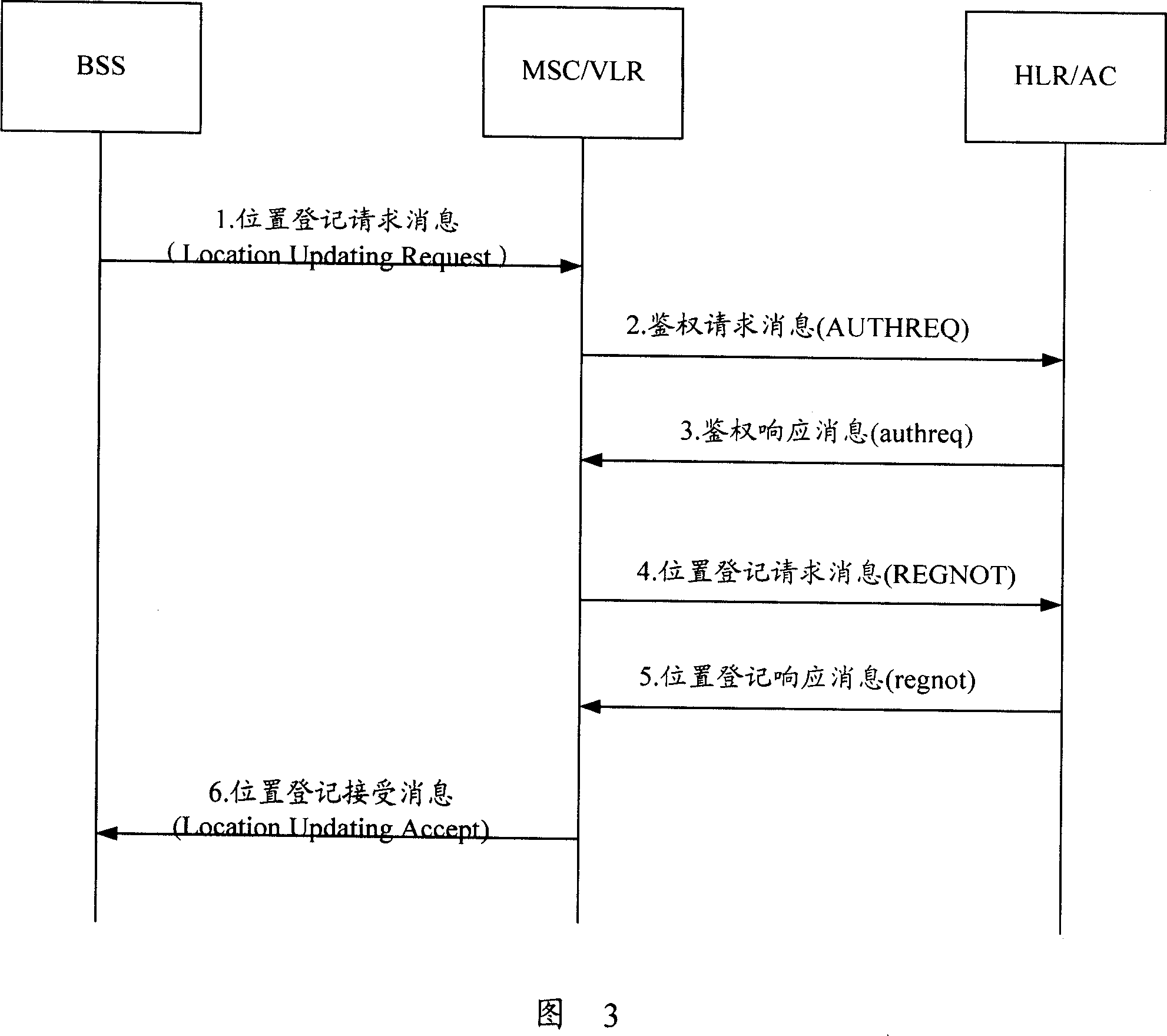
[0144] Step 3: HSS requests authentication data from the Home Location Register (HLR);
[0145] Step 4: HLR generates random number Randr, and uses CAVE algorithm to generate authentication data Authr according to the random number Randr, and feeds back the authentication data Authr to HSS;
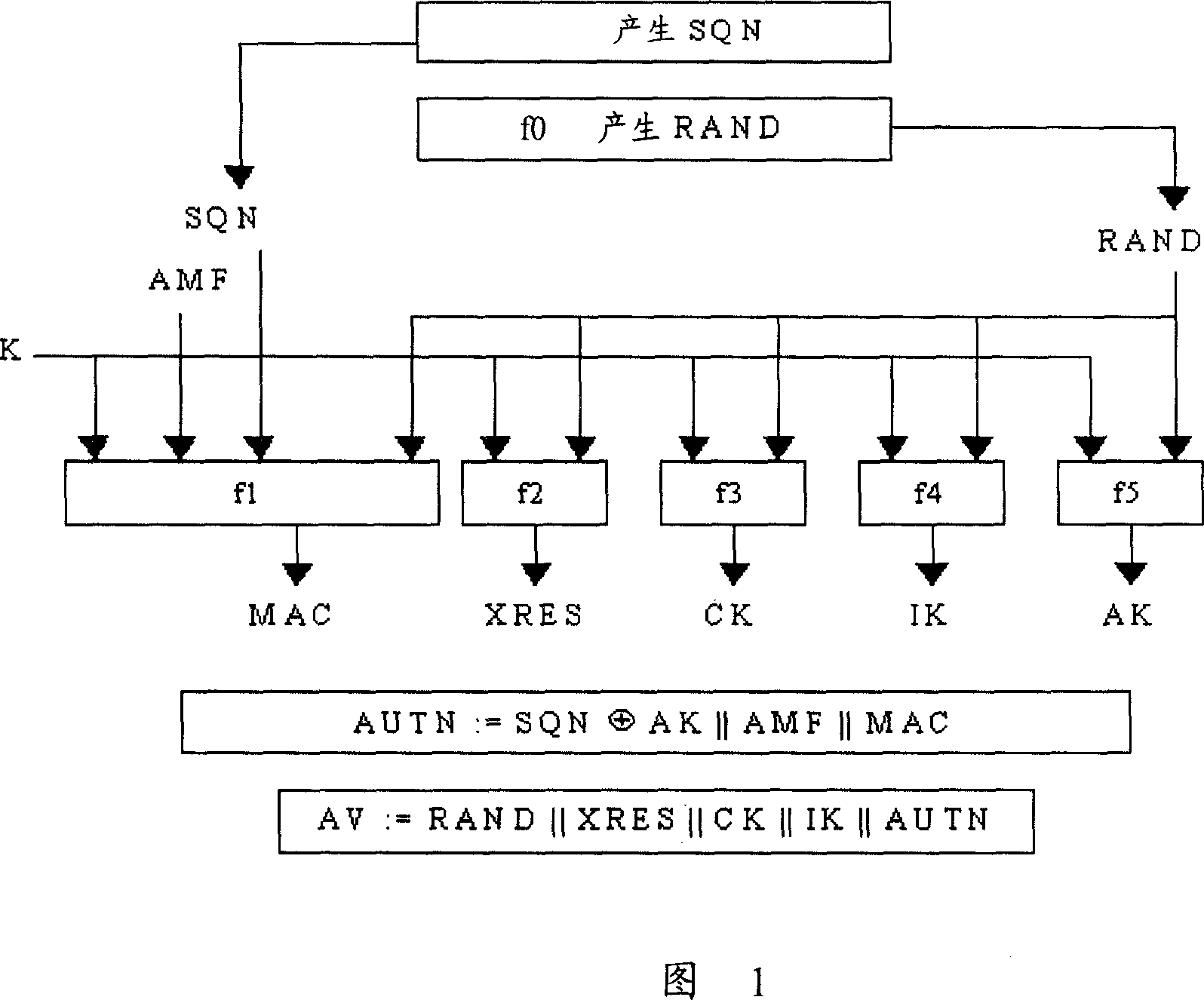
[0146] Step 5: HSS uses Authr to generate a key and Randr to generate Rand, and uses the AKA algorithm to calculate the 5-tuple authentication vector AV ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com