An unconditional security authentication method based on lfsr hash
A technology of security authentication and hashing, which is applied in the field of information security, can solve the problems of violating security proof assumptions, low randomness of irreducible polynomials, and accelerated calculation speed, so as to reduce the probability of security failure and tighten the probability of security failure Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
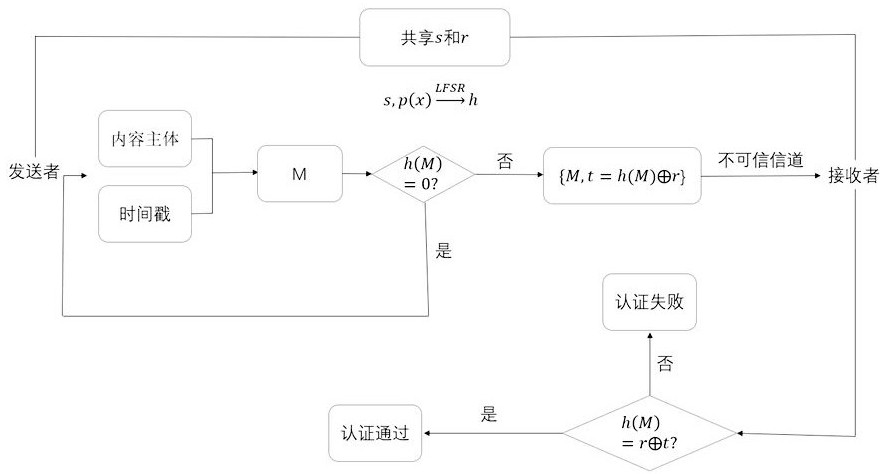
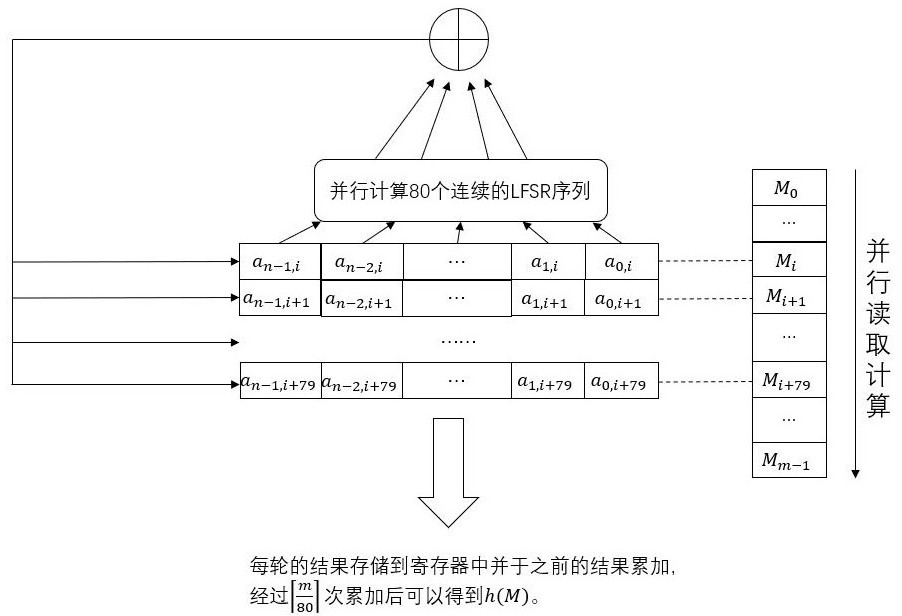
[0043] Preferably, take n =128, select public p ( x ) =x 128 +x 29 +x 27 +x 2 + 1. It should be noted that this embodiment only demonstrates the first round of authentication, and each subsequent round of authentication follows the steps of the first round of authentication.
[0044] Step 1, the authentication parties share the initial state of 128 bits generated by random numbers s and a random bit string r . s and r The information is only shared by the authenticating parties. Preferably, this step is implemented using the BB84 protocol quantum key distribution, thereby ensuring that the attacker cannot obtain s and r any information.
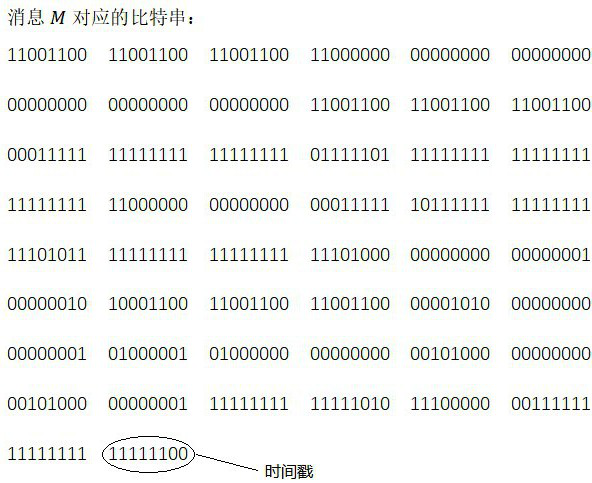
[0045] Step 2, assuming that the sender Alice wants to send a string of 392-bit text, then she converts this message into a binary code, and adds a timestamp after the string of codes. Optionally, an 8-bit clock is used, that is, the clock period is 256, assuming that the time stamp at this time is (11111100). Timestamp th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com