Implementation method of plug-and-play reference frame-independent dual-field quantum key distribution protocol
A quantum key distribution, plug-and-play technology, applied in the field of communication, to achieve the effect of increasing the distance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
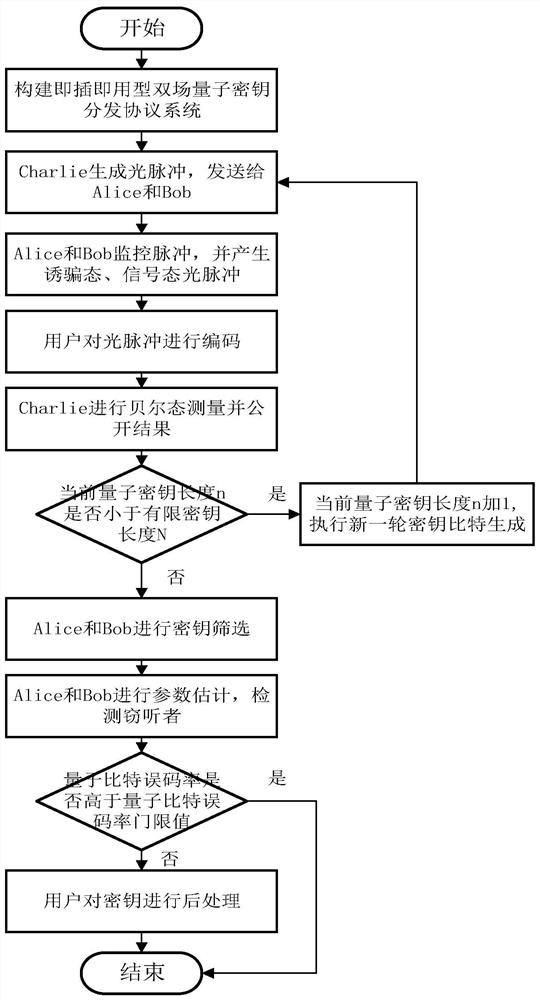
[0028] The quantum key distribution QKD protocol plays an important role in the communication network. Although the two-field quantum key distribution TF-QKD protocol and the improved version of the TF-QKD protocol have broken through the limit of the coding rate-distance, these protocol systems are in the light source preparation There are high requirements for the consistency of the preparation of the double light source, and the preparation of the double light source may bring about security vulnerabilities, resulting in a decrease in the key rate of the quantum key distribution system. At the same time, the above-mentioned quantum key QKD protocol system does not use the reference frame-independent RFI protocol combined with the plug-and-play structure, so reference frame alignment and an additional phase polarization calibration system are required, which greatly increases the complexity of the system and further leads to quantum key distribution. A decrease in the key rat...
Embodiment 2
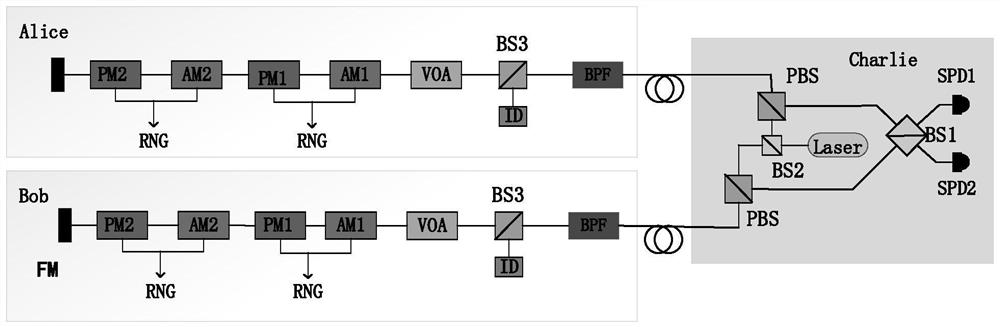
[0055]The RFI-TF-QKD protocol implementation method of the plug-and-play type reference frame-independent dual-field quantum key distribution RFI-TF-QKD is the same as embodiment 1, and the construction quantum key distribution system described in step (1), see figure 1 , including the following:
[0056] (1a) Determine the structure of the plug-and-play double-field quantum key distribution TF-QKD system: the present invention involves two legal communication users, Alice and Bob, and an untrusted third party Charlie. The TF-QKD system with dual-field quantum key distribution is equipped with two communication user branches and a measurement end; the third party Charlie at the measurement end uses a single light source to prepare light pulses and splits them into two paths through the beam splitter BS2. The polarizing beam splitter PBS is sent to two communication user optical branches; the two communication user optical branches adopt the same structure, and the optical puls...
Embodiment 3
[0061] The implementation method of the plug-and-play double-field quantum key distribution protocol independent of the reference frame is the same as that of embodiment 1-2, and the communication users described in step (3) monitor and modulate the optical pulse, see figure 1 , including the following:
[0062] (3a) The monitoring module overcomes the Trojan horse attack: In the present invention, the monitoring module is jointly realized by the optical beam splitter BS3 and the photodetector ID. Since the third-party Charlie at the measurement end uses a single light source to prepare light pulses, and sends the light pulses to communication users through the optical fiber channel, there may be an eavesdropper Eve who replaces the photon number distribution of the light pulses on the channel with an arbitrary distribution to obtain More information. Therefore, in the present invention, Alice and Bob, both communication users, obtain the photon number distribution PND of thei...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com