Method, device and system of authentication and service calling
An authentication server and authentication technology, applied in transmission systems, security devices, electrical components, etc., can solve problems such as malicious ordering, illegal services provided by application server users, and poor security, and achieve the effect of preventing replay attacks.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
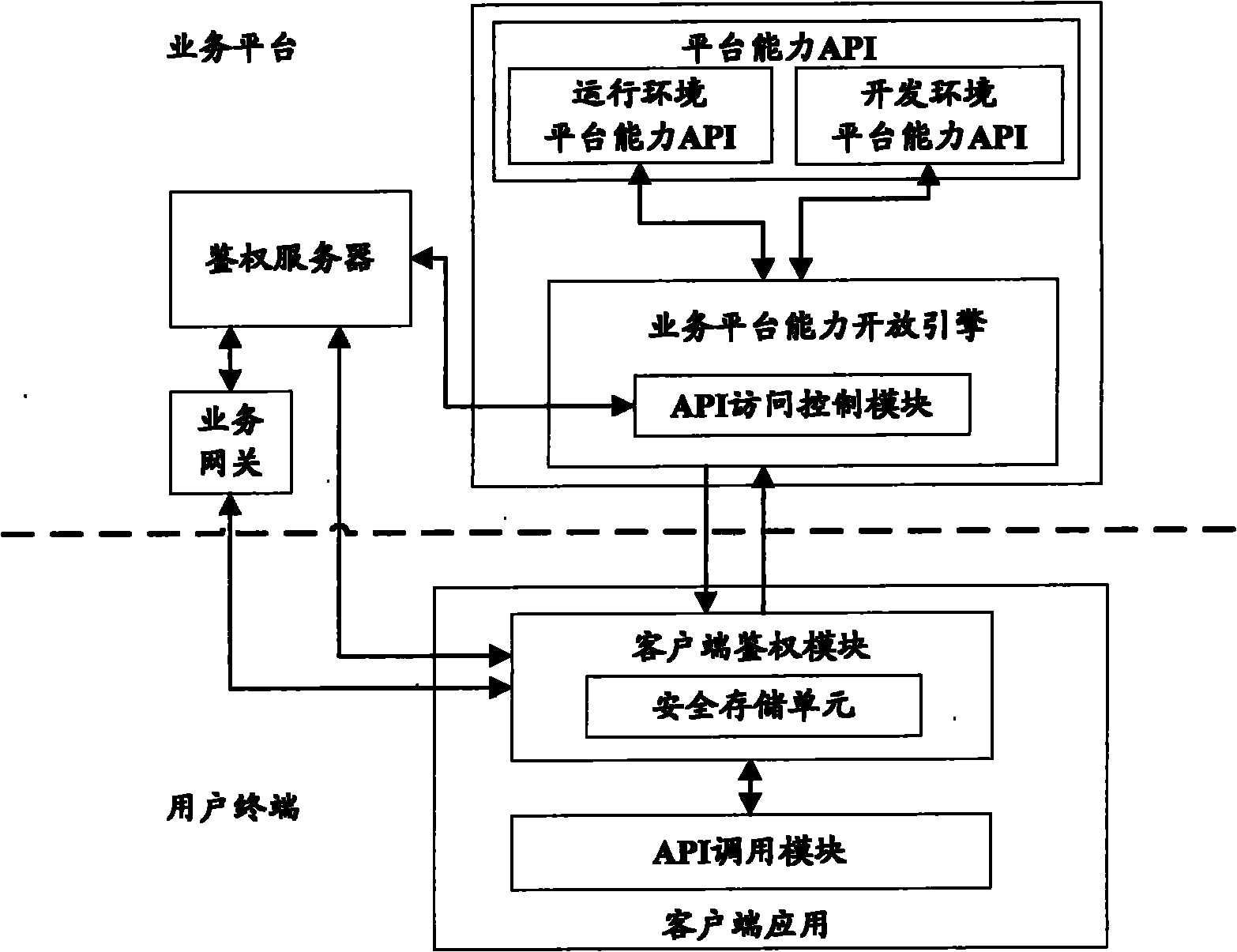
[0066] First introduce the system architecture involved in the embodiment of the present invention, such as image 3 shown, including:
[0067] Platform capability API, where the platform capability API is divided into "running environment platform capability API" and "development environment platform capability API", "running environment platform capability API" is mainly used by user terminals during business operations, and "development environment platform capability Capability API "is mainly used by developers and network operators during the development and testing process, and is mainly used in the development environment SDK for call testing;
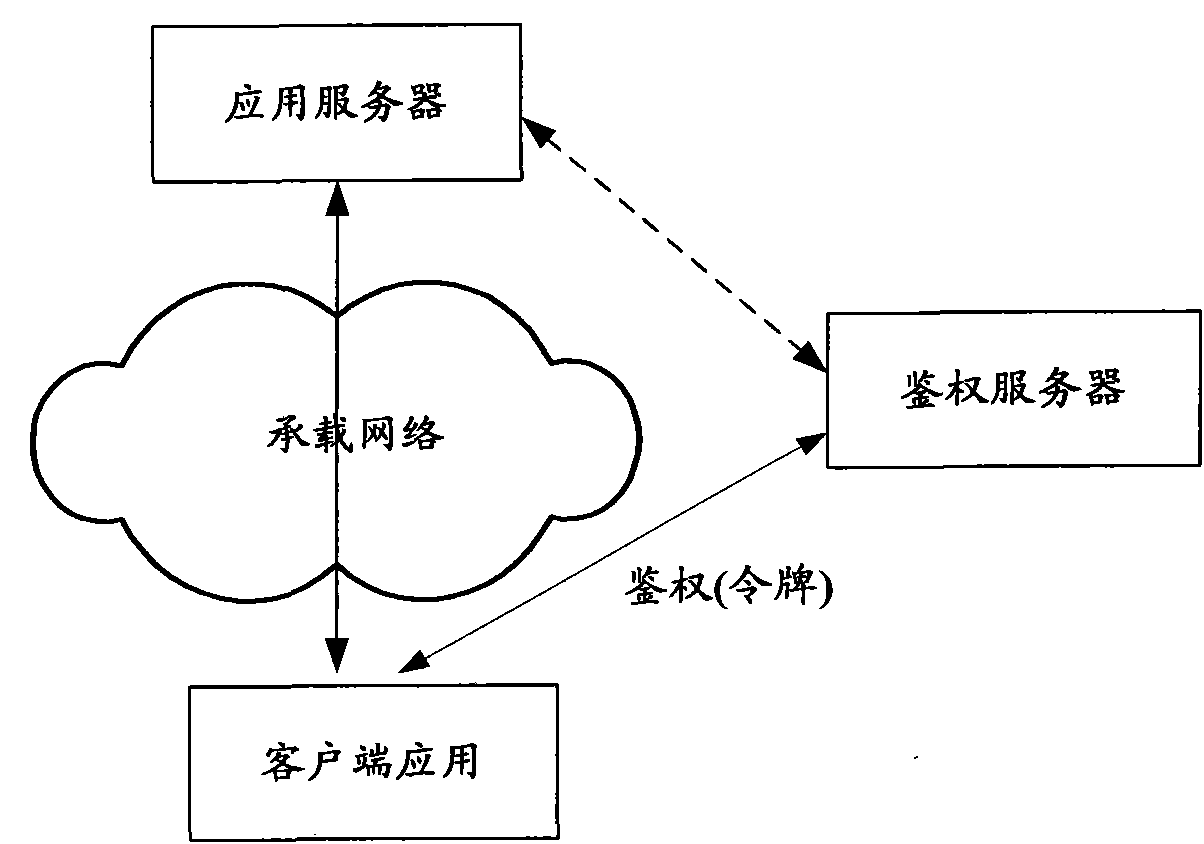
[0068] The authentication server is used to store the identity information of user terminals and client applications, and provide secure identity information and dynamic tokens for the running phase;
[0069] The API access control module is implemented in the business platform capability open engine, and is used to perform leg...
Embodiment 2
[0080] In order to realize the legitimacy authentication and authentication of the client application by the authentication server (the authentication server is a part of the service platform), the embodiment of the present invention proposes an authentication method based on the registration mechanism of the client application, so that the service platform can authenticate the user The legitimacy authentication of the terminal and the two-way authentication between the client application and the business platform also realize the acquisition of the authentication factor by the client application and provide the basis for subsequent calls to the platform capability API.
[0081] First, the development and testing phase of the client application is introduced.
[0082] The SDK environment includes a "Test Authentication Module" for development and testing. The developer develops and tests the client application based on the "test authentication module", and the client applicati...
Embodiment 3
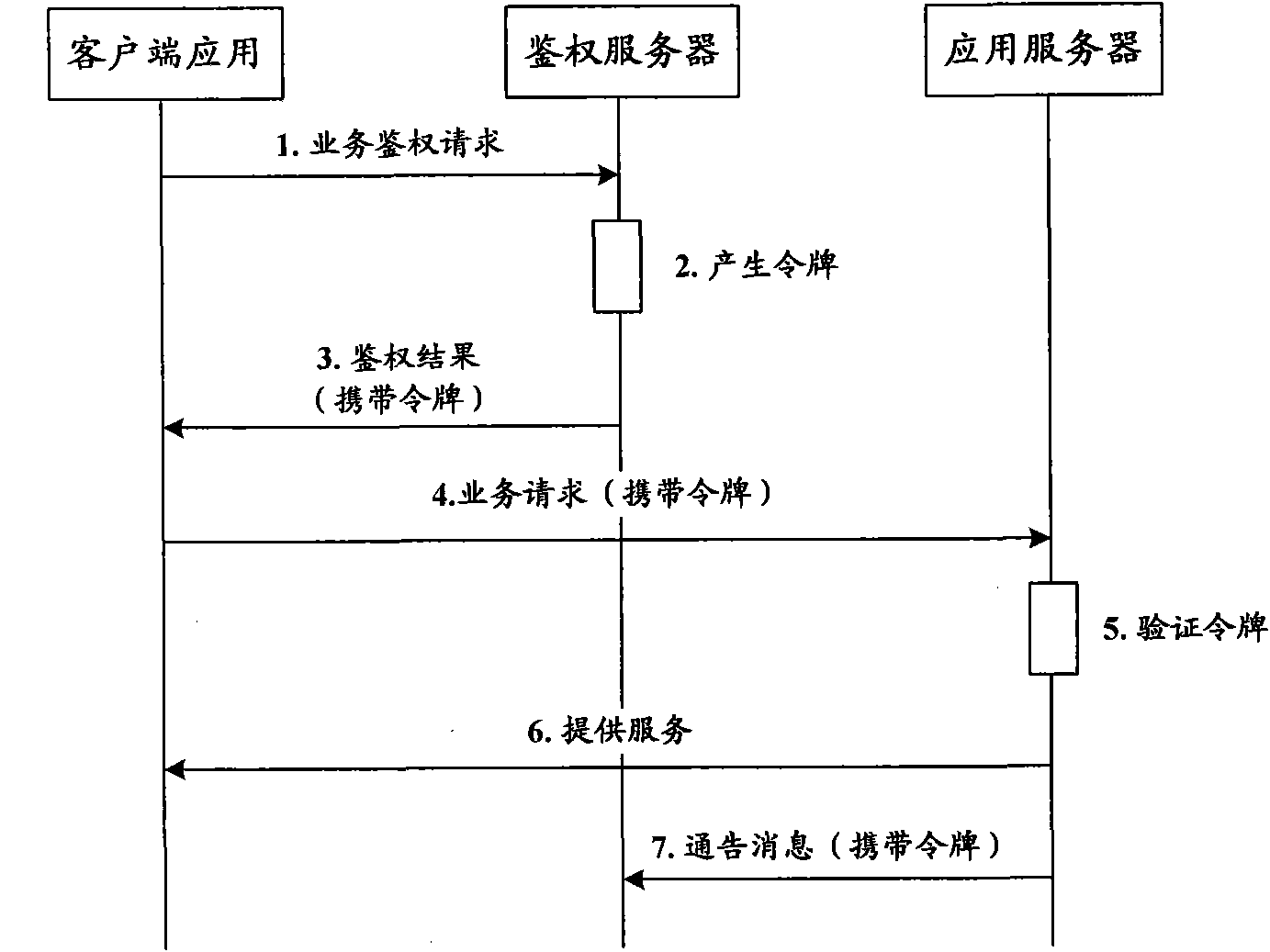
[0109] When the API calling module needs to call the platform capability API, the API calling module first transfers the business request to the client authentication module, and the client authentication module optionally performs a local integrity check on the client application according to the security policy, and then generates a real-time Dynamic token and optionally set token usage parameters, and add the dynamic token and token usage parameters to the original business request and then send it to the business platform through the HTTPS secure data transmission channel established with the API access control module, the business After receiving the business request, the API access control module in the platform confirms that the type or priority of the business request meets the requirements of the token usage parameters, and then forwards the dynamic token to the authentication server for verification. If the dynamic token passes the authentication server The verificati...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com