Authentication method, authentication system and authentication server
A technology of authentication server and authentication method, applied in the fields of authentication method, authentication system and authentication server, and can solve problems such as loss
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
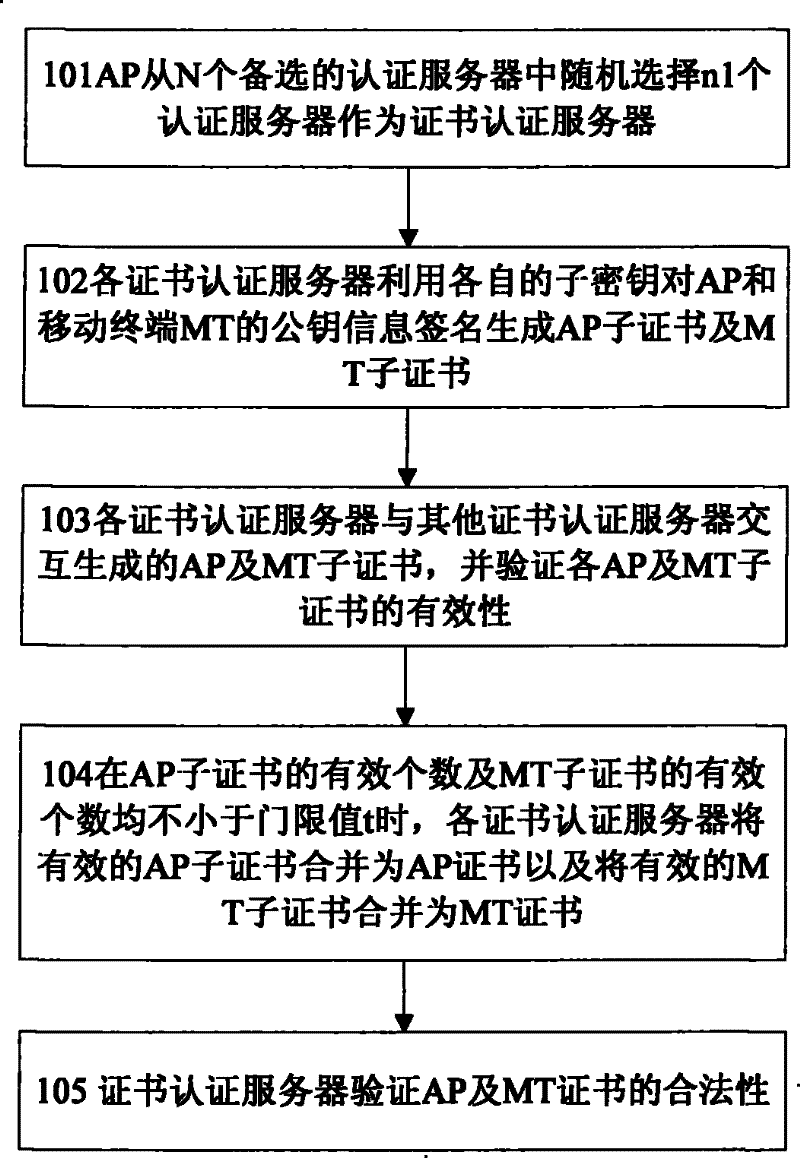
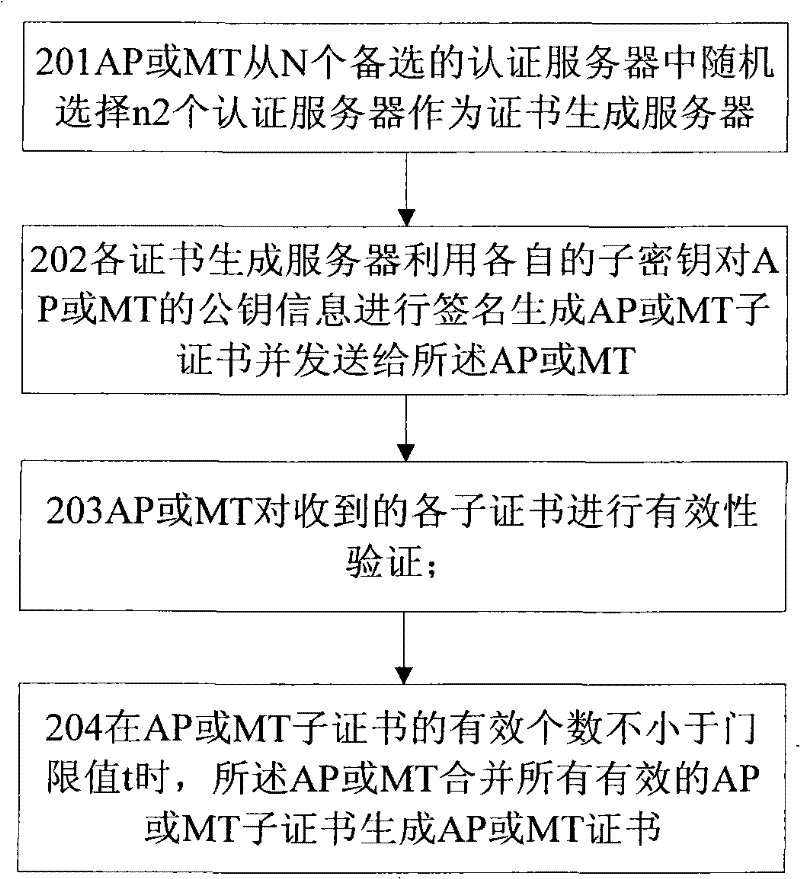
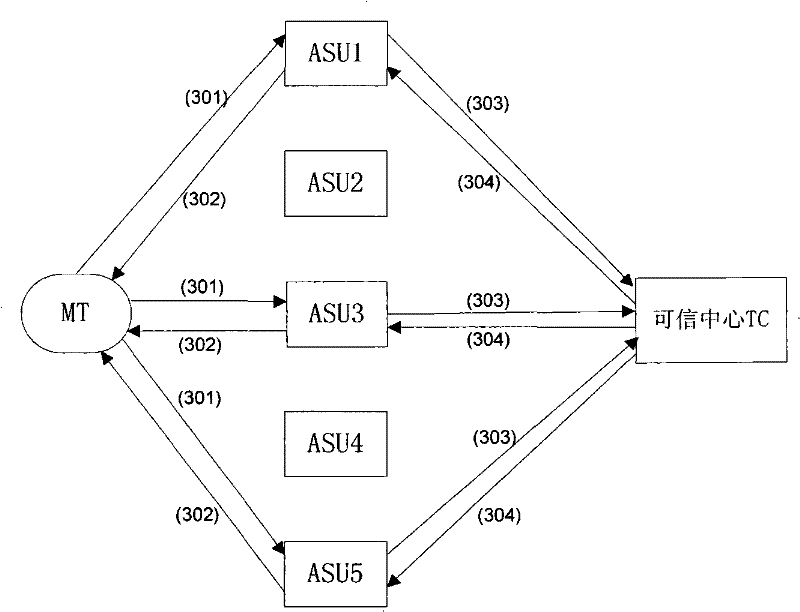
[0119] Example 1: ASU1 needs to verify the validity of the AP sub-certificate and MT sub-certificate generated by ASU3 and ASU5. If the AP sub-certificate or MT sub-certificate provided by ASU3 fails the verification, it is considered that ASU3 has cheated, and then reported to the TC.
example 2
[0120] Example 2: If ASU1 verifies that the AP sub-certificate generated by ASU3 is invalid, and ASU3 verifies that the AP sub-certificate generated by ASU5 is invalid, the TC records that both ASU3 and ASU5 have cheated
[0121] Step 406: ASU1, ASU3, and ASU5 merge sub-certificates, and after comparing with the MT certificate and AP certificate in the authentication request message to obtain the verification result, send an authentication request response message to the AP;
[0122] Step 407: After the AP receives the authentication response message sent by ASU1, ASU3, ASU5, it decides whether to allow the MT to access the network according to the certificate verification results of the MT by ASU1, ASU3, and ASU5; If all the certificate verifications of ASU1, ASU3 and ASU5 pass, the MT is allowed to access the network, and the AP sends an access authentication response message to the MT. If the request message passes the certificate verification of the AP, the MT decides to a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com