Wireless communication device and method for realizing service security thereof
A wireless communication device and wireless communication module technology, applied in wireless communication, safety devices, electrical components, etc., can solve problems such as chaotic economy in customer operation market, different software and hardware interfaces, losses, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
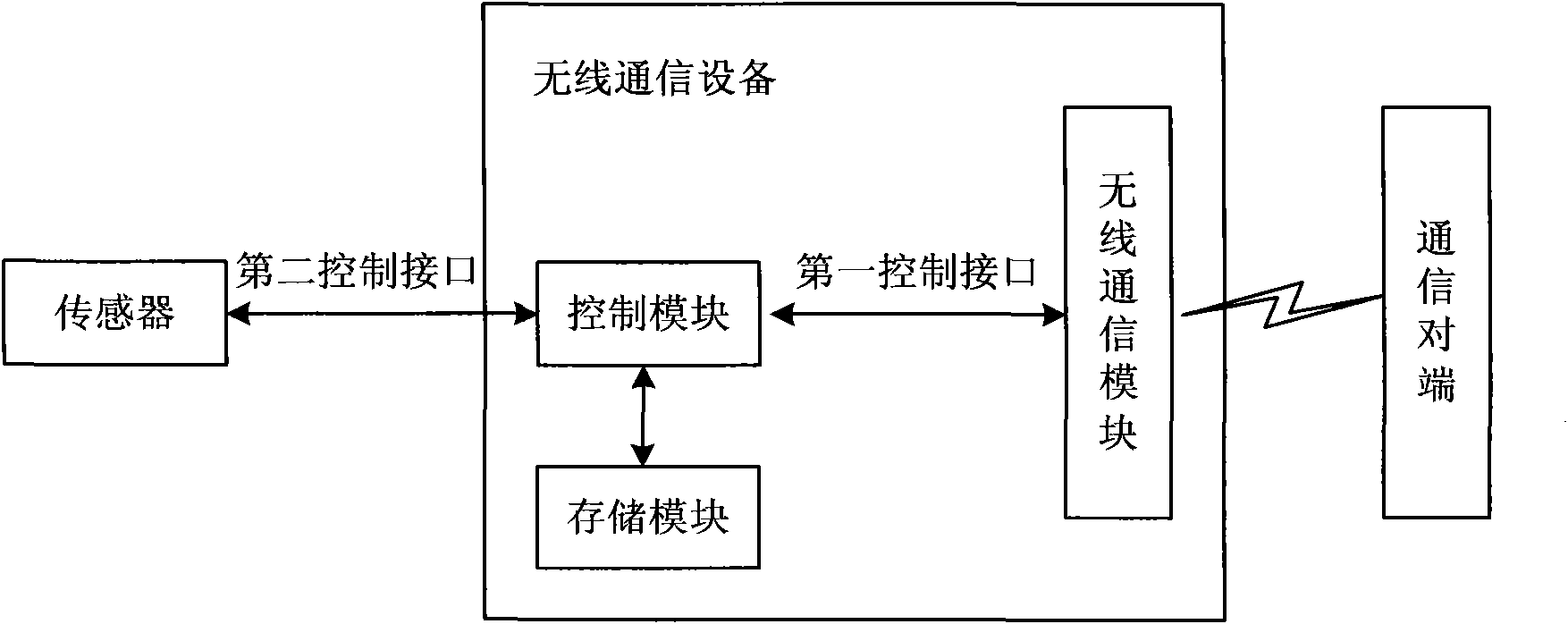
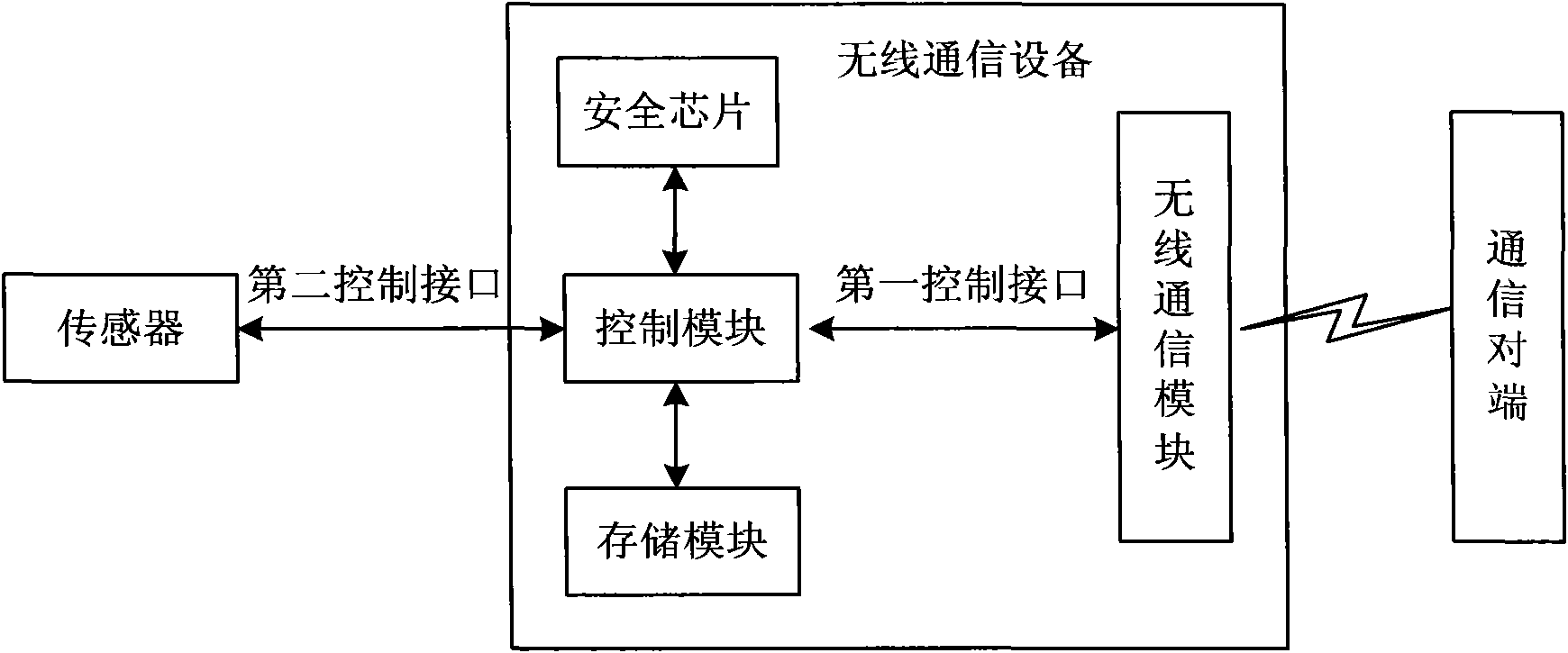
[0088] In this embodiment, the structure of the wireless communication device is as follows Figure 2AAs shown, it includes a control module, a wireless communication module, a storage module and a security chip, wherein the control module, the wireless communication module and the storage module have original functions. The security chip is integrated on the main board of the wireless communication device, directly connected with the control module, and has no direct interface with the wireless communication module. In each embodiment, the security chip can be packaged in the wireless control device by SMD welding and applying anti-tamper glue, so as to realize the integration of the wireless control device and the security chip.
[0089] The security chip stores one or more keys, and can optionally store one or more of the following data:
[0090] a) one or more security algorithms;
[0091] b) one or more security protocols;
[0092] c) A network identification of the wi...
no. 2 example
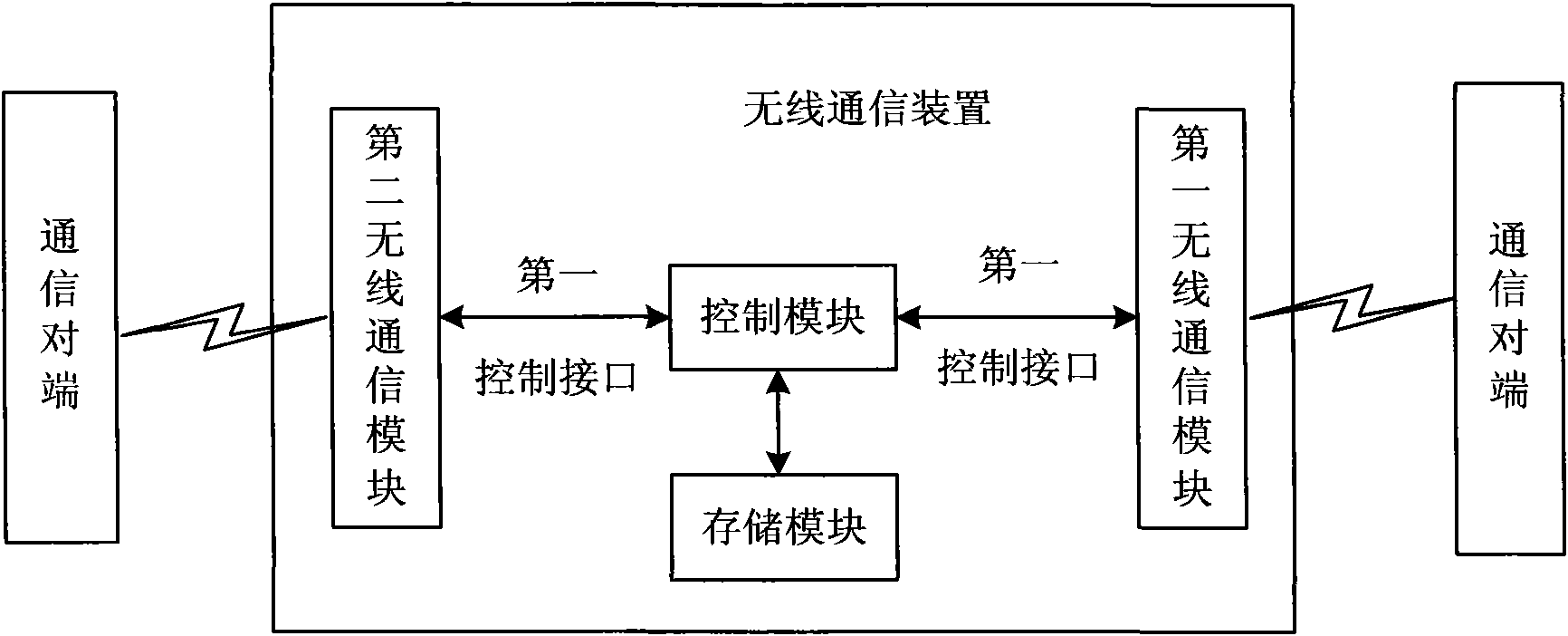
[0165] The structure of the wireless communication device of this embodiment is as follows Figure 6 As shown, it includes a control module, a wireless communication module, a storage module and a security chip. The difference from the first embodiment is that the security chip is integrated in the wireless communication module and becomes an integral part of the wireless communication module. The security chip passes wireless The communication module is connected with the control module. for Figure 2B wireless communication device, a security chip can be integrated in each wireless communication module.
[0166] The function and processing flow of each module in this embodiment are basically the same as those in the first embodiment, except that when the security chip interacts with the control module, it needs to forward data through the wireless communication module, and when the wireless communication module needs to obtain the key from the security chip, It can no long...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com