Social network user identity authentication method based on relation statement
A technology of user identity authentication and social networking, applied in user identity/authority verification, transmission system, public key for secure communication, etc., to achieve the effect of easy operation and convenient verification
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
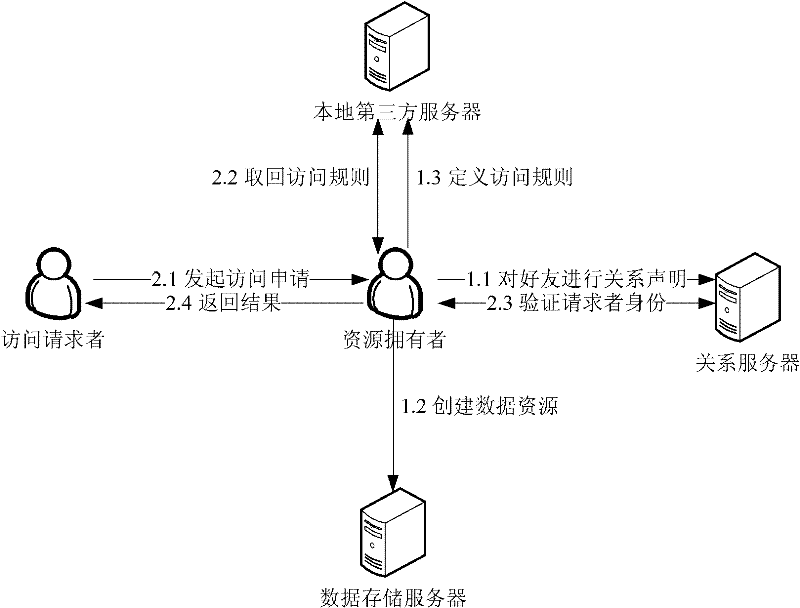
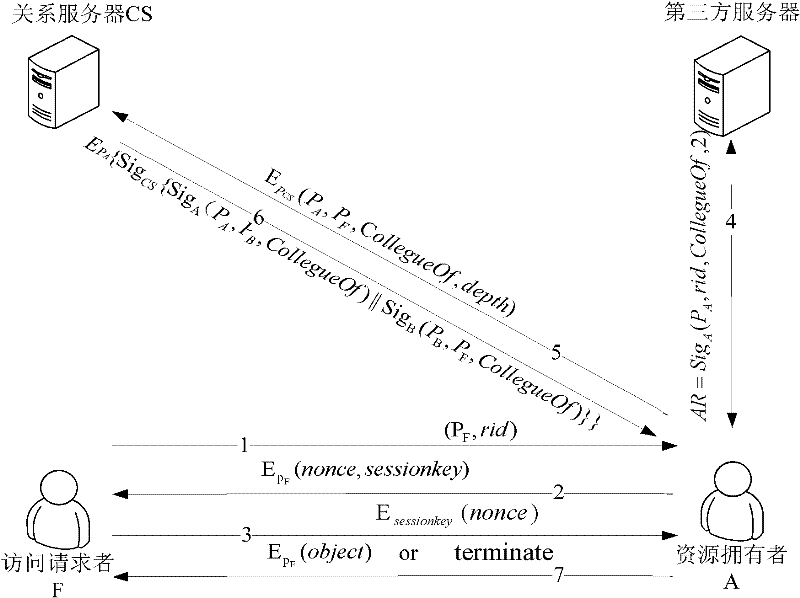
[0048] See figure 1 , the present invention is a social network user identity authentication method based on relationship statement, the specific steps of the method are as follows:
[0049] Step 1: Issuing a Relationship Statement
[0050]The user first issues a relationship statement to his direct friends, and the relationship statement contains these parameters: {the issuer of the relationship statement, the receiver, the relationship type, and the timestamp}. where the timestamp indicates when the relationship statement was signed. The relationship declaration in Extensible Markup Language (XML) form is as follows:
[0051]
[0052] publisher public key
[0053] recipient public key
[0054] Relation Type
[0055] current time
[0056]
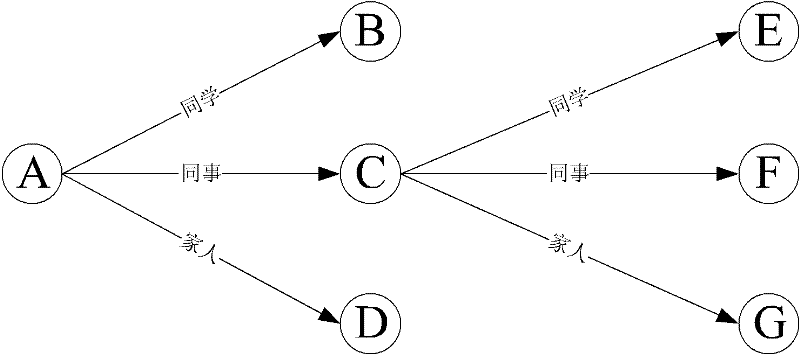
[0057] For example in figure 2 In , A wants to issue a relationship statement with a colleague relationship to B. This relationship statement can be expressed as: Sig A (P A , P B , CollegeOf, TS), where TS refers to the tim...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com