Safe multicast listener discovery (MLD) snooping method and device
A discovery protocol and multicast technology, applied in digital transmission systems, electrical components, transmission systems, etc., can solve problems such as denial of service attacks, occupying software and hardware resources, increasing the CPU burden of multicast routers, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0037] The technical solutions of the present invention will be further described below in conjunction with the accompanying drawings and through specific implementation methods.
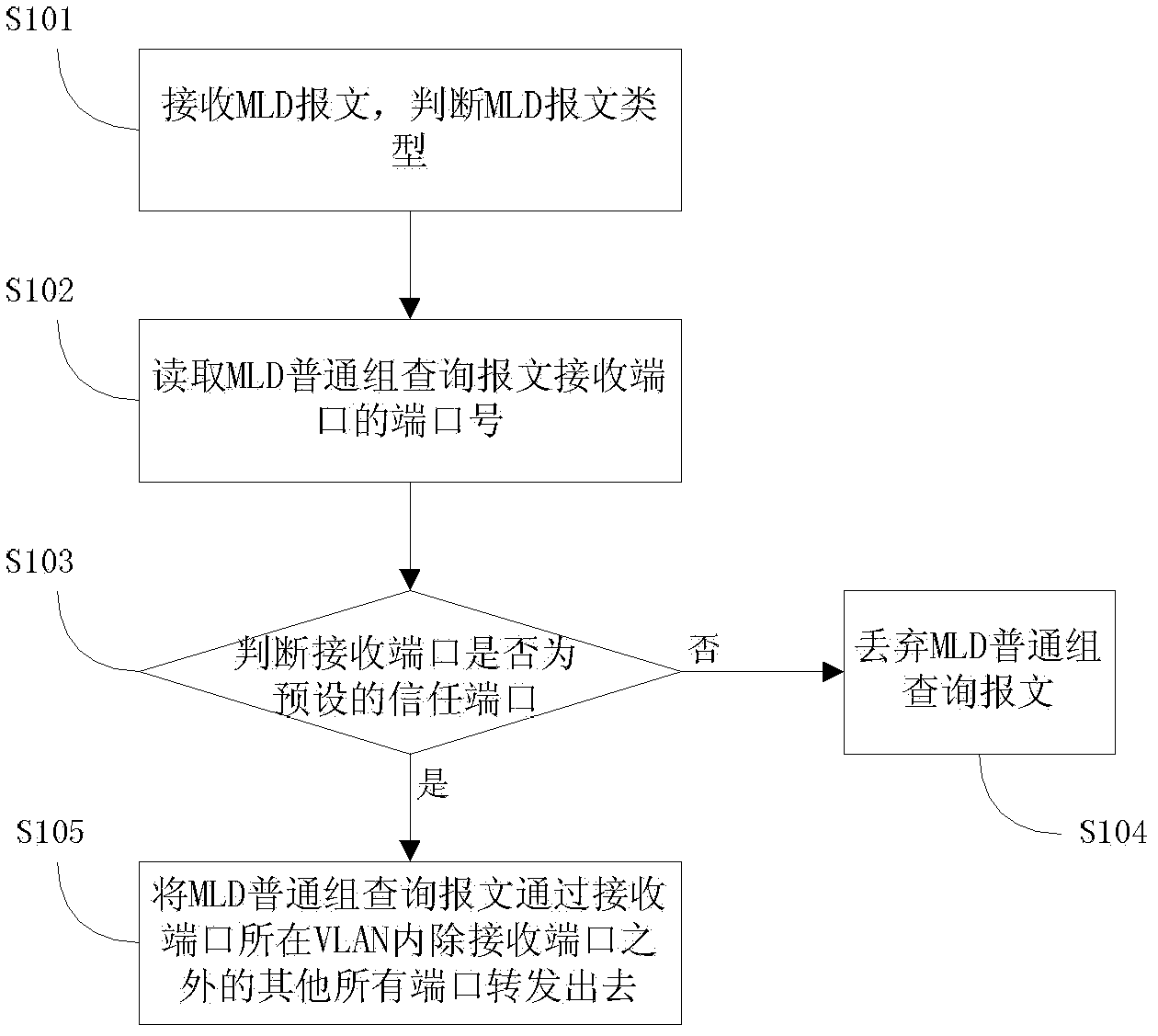
[0038] figure 1 It is a schematic flowchart of a method for secure multicast listener discovery protocol snooping provided by Embodiment 1 of the present invention. like figure 1 As shown, the method includes:
[0039]Step S101, receiving an MLD message, and judging the type of the MLD message. The type of the MLD message is determined by reading the information in the MLD message type field.
[0040] Step S102, when the type of the received MLD message belongs to the MLD general group query message, read the port number of the receiving port of the MLD general group query message. The port number of the receiving port is that the packet receiving driver reads from the chip register, and is recorded in the port field in the software format of the MLD general group query message, and the software...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com