Method and device for preventing IGMP (Internet Group Management Protocol) from being cheated and attacked
A technology of MAC address and message, which is applied in the field of computer data communication, can solve the problems of increasing the CPU burden of multicast routers, occupying software and hardware resources, and wasting bandwidth, and achieves the effect of safe operation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0035] In order to describe the technical content, achieved objectives and effects of the present invention in detail, the following will be described in detail in conjunction with the implementation methods and accompanying drawings.
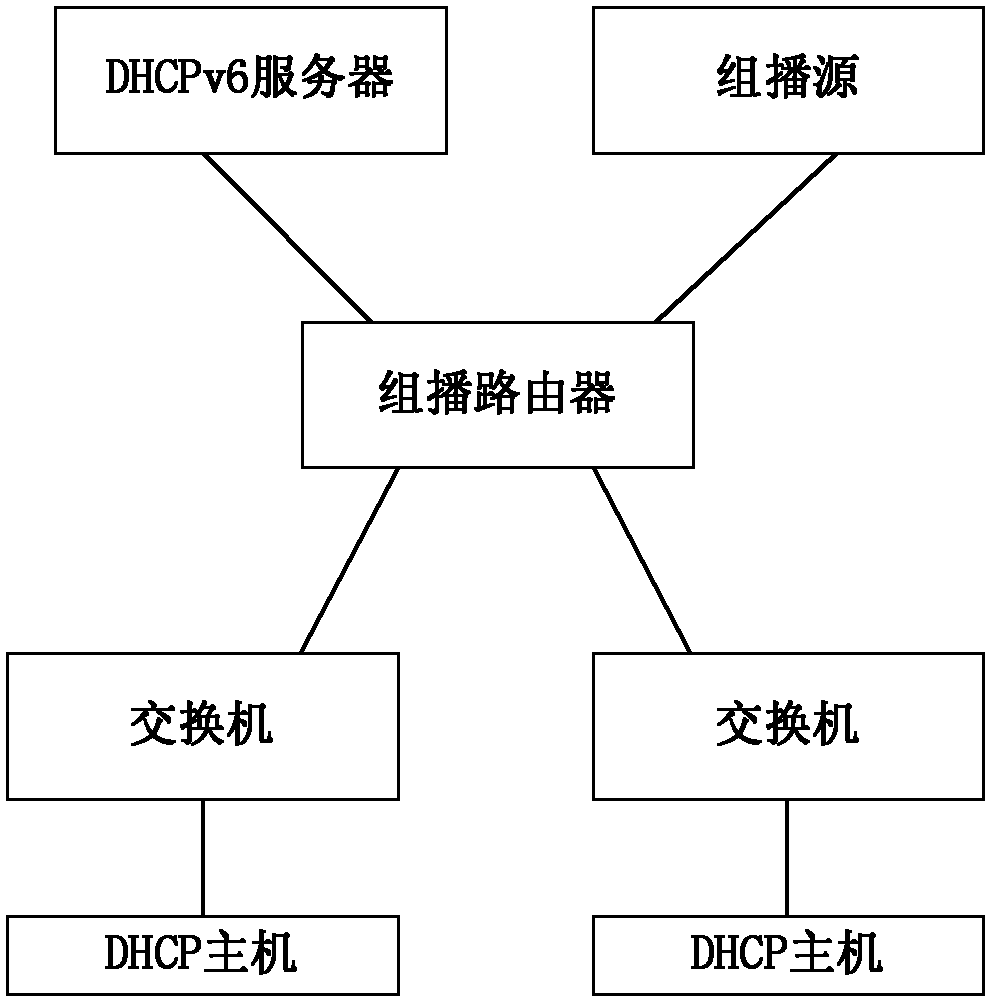
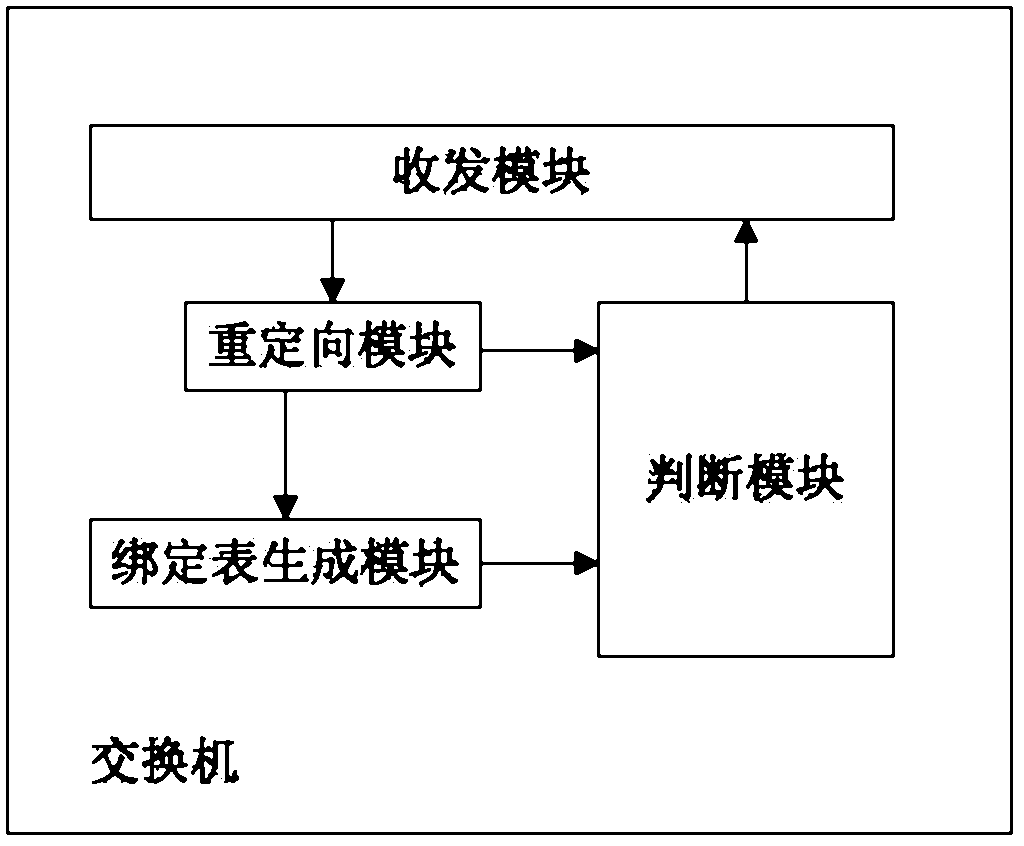
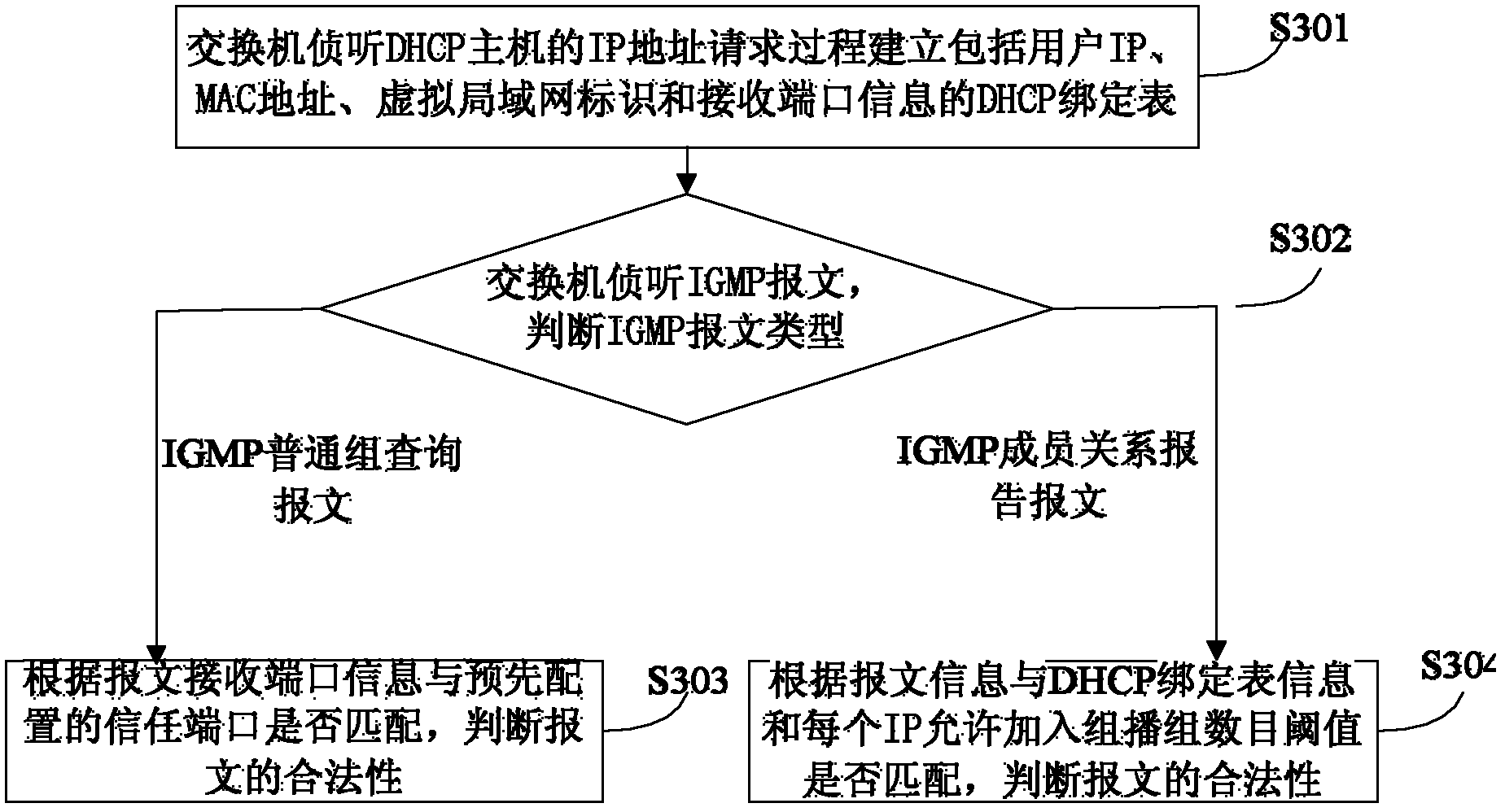
[0036] figure 1It is a system block diagram of preventing IGMP spoofing and attacking under the DHCP environment of the embodiment of the present invention. The system includes a DHCP host, a switch, a multicast router, a DHCP server and a multicast source, the DHCP host is connected to the multicast router through a switch, the multicast router is connected to the multicast source, and the multicast router connects to the DHCP server; wherein, the The multicast router is used to initiate an IGMP member query and allow the nodes in need to respond; the switch is used to listen to the IP address request process of the DHCP host to establish a DHCP binding including user IP, MAC address, virtual local area network identifier and receiving port in...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com