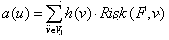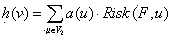Web search results security sorting method based on Hits algorithm
A technology of search results and sorting methods, which is applied in the field of network security, can solve problems such as endangering the information security of users' computer terminals, reduce the probability of accessing unsafe web pages, and enhance Web security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0021] The present invention is based on the Hits algorithm-based Web search result security sorting method, and establishes a malicious feature library F ( f 1 , f 2 , f 3 , … , f n ), the malicious signature database contains n A network virus, a Trojan horse, and a feature code that appear in a web page, and each feature code of the malicious feature database f i represented by m The vector form composed of components, namely f i =( f i1, f i2 , f i3 , … , f im ),in i ∈{1,2,…, n}, f i ∈ F ; Then, based on the Hits algorithm, the security ranking of webpages is performed according to the following steps:
[0022] Step 1: Submit the search topic to the text-based search engine, and take the top page from the set of returned result pages t A collection of web pages, denoted as the root set R ; to the root set R root set R Referrers and Referrer Root Sets R web pages, after processing internal links and irrelevant links, the root set R ex...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com