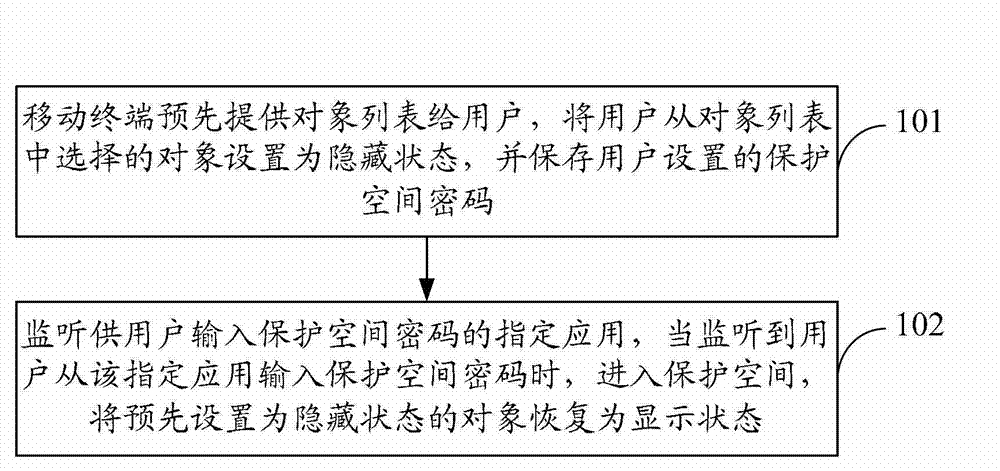
Method for improving security of mobile terminal and mobile terminal
A mobile terminal and security technology, applied in the field of information security, can solve problems such as hidden dangers of application programs or files, and achieve the effect of improving security and being easy to use
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
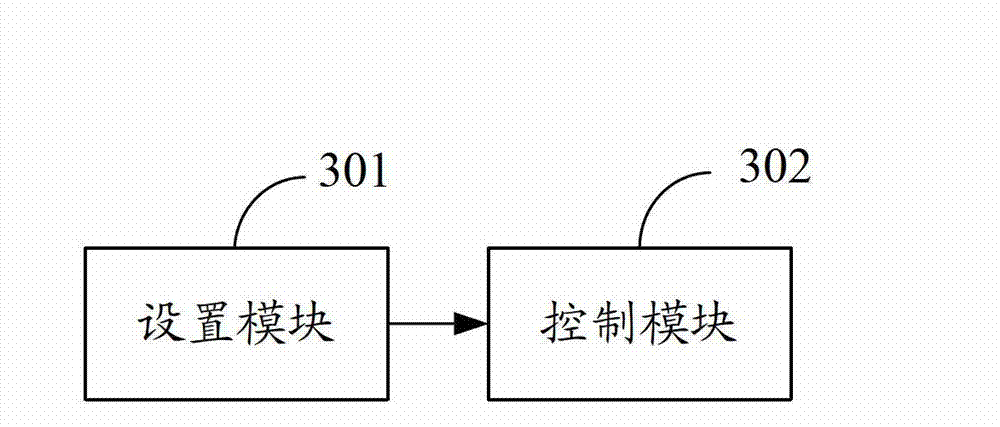
[0069] see Figure 4 , in one embodiment, the setting module 301 includes:
[0070] The providing unit 301a is configured to provide the user with an application list in advance, the application list including applications installed in the mobile terminal; and / or provide the user with a file list in advance, the file list including files saved in the mobile terminal.
[0071] In another implementation manner, the control module 302 also includes:
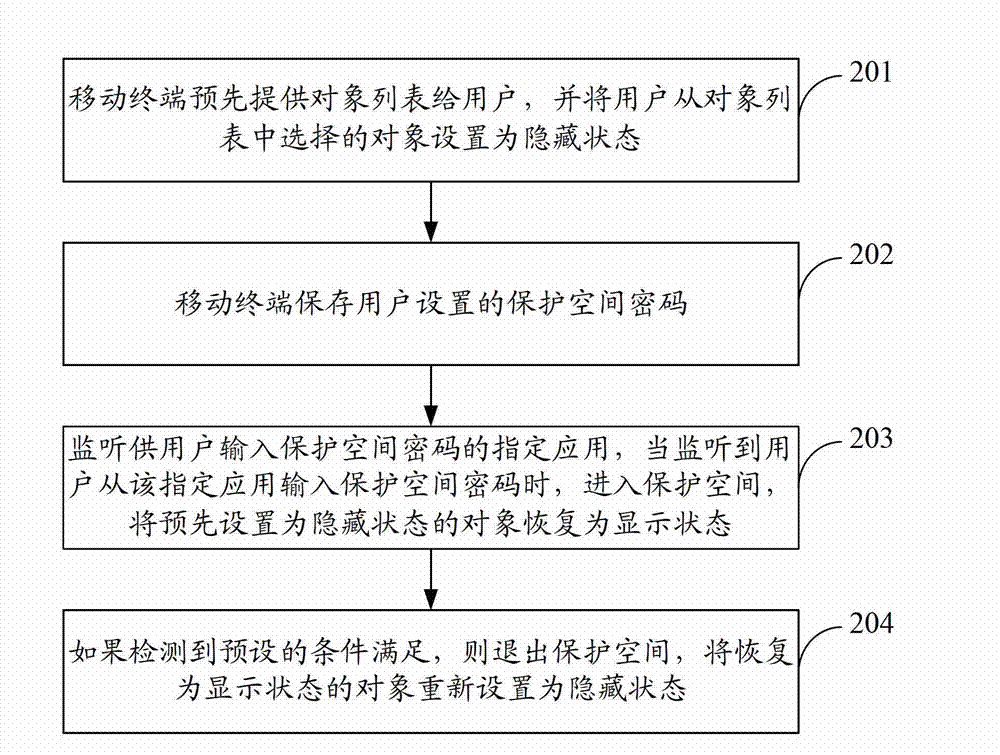
[0072] The exit unit 302a is configured to exit the protection space and reset the object restored to the display state to the hidden state if it is detected that the preset condition is met after the object previously set to the hidden state returns to the display state.
[0073] In yet another implementation manner, the exit unit 302a is used to:
[0074] After the object preset to the hidden state returns to the displayed state, if the screen of the mobile terminal is locked, or the time of no operation in the protected space r...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com