Method and device for filtering IP (Internet Protocol) message
A technology of IP message and filtering method, which is applied in the field of information security and encryption to achieve the effect of improving configuration efficiency, reducing impact, and reducing coupling
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0075] Embodiment 1: An IP packet filtering method includes:
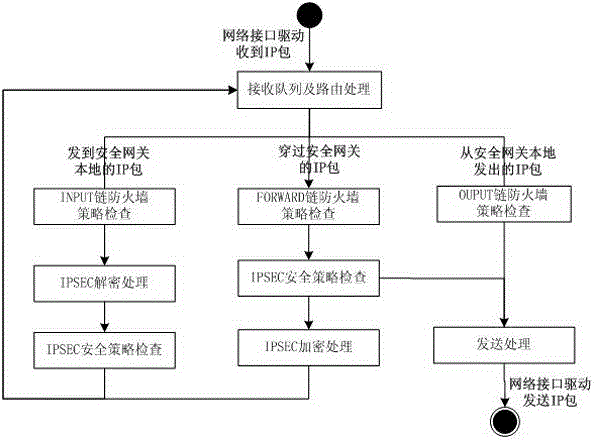
[0076] Step 1. It is conducive to the netfilter packet filtering mechanism of Linux. When the IPtables module is initialized, set the default policy of OUTPUT chain to "Allow" and the default policy of INPUT chain to "Discard", and add a firewall policy to the INPUT chain to allow IPSEC encapsulated secret The notification message enters the gateway, and the key agreement message is allowed to enter the gateway;
[0077] Step 2. Set the default policy of the FORWARD chain to "discard", create a new rule chain named "SECPOLICY", add a policy in the FORWARD chain to jump to this chain, and load all firewall policies configured by the administrator on the chain. This allows filtering of IP packets that are not processed by IPSEC in and out of the gateway.
[0078] Step 3. Use the policy matching function provided by the xt_policy module to add the following two firewall policies at the end of the FORWARD chain:
[0079] 1) T...
Embodiment 2
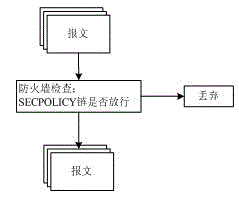
[0081] Embodiment two: such as figure 2 As shown, on the basis of Embodiment 1, the specific process of filtering IP packets that enter and exit the gateway without IPSEC processing in the step 2 includes:
[0082] Step 21: Receive a clear IP message that passes through the gateway. The IP message does not have a matching IPSEC security policy and does not need IPSEC processing;
[0083] Step 22: After routing processing, enter the firewall FORWARD chain, check the firewall policy under its sub-chain SECPOLICY, and determine whether to pass or discard the IP packet;
[0084] Step 23: If the firewall policy is to allow, the IP packet is forwarded.
Embodiment 3
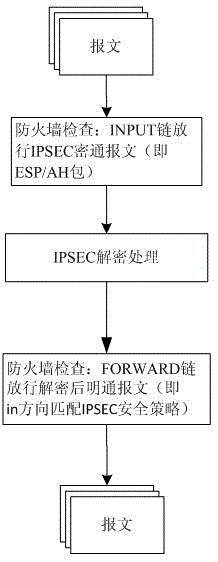
[0085] Embodiment 3: On the basis of Embodiment 1 or 2, such as image 3 As shown, the specific process of filtering the IP packets after the IPSEC decryption in the inbound direction in the step 3 includes:
[0086] Step 311: Receive an IPSEC cipher message from the remote gateway;
[0087] Step 312: Enter the firewall INPUT chain after routing processing. Since it is checked that the IPSEC cipher text is an ESP / AH protocol packet, it is allowed to pass;
[0088] Step 313, according to the triplet information: the message destination address, SPI security parameter index, and security protocol number (AH or ESP) to find the security association, and perform IPSEC decryption processing. The decrypted clear message destination address is the gateway Internal network;
[0089] Step 314, after routing processing, enter the firewall FORWARD chain, check that the decrypted plain notification text matches the IPSEC policy in the IN direction, and release the IP message;
[0090] Step 315: Th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com