Method for verifying legality of cloud shields in long-distance mode
A remote verification and legality technology, applied in the field of remote verification of cloud shield legality, can solve the problems of forgery and theft of important data and materials
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0009] The present invention will be described in detail below in conjunction with accompanying drawing and embodiment:
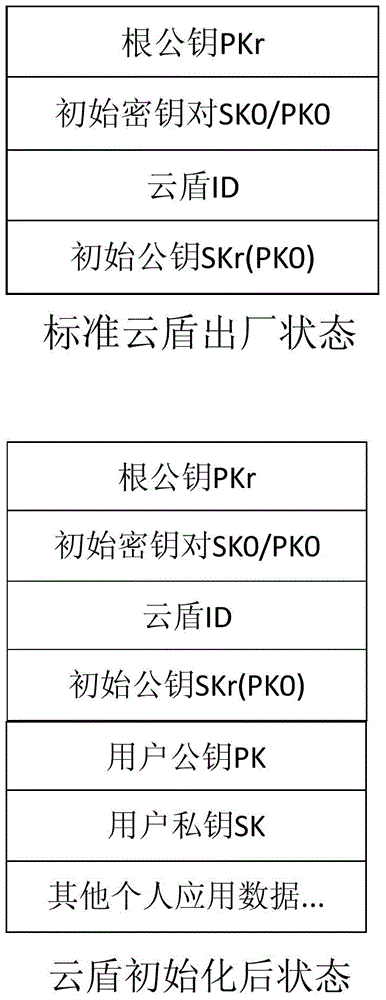
[0010] Such as figure 1 As shown, the method of remotely verifying the legitimacy of Cloud Shield, the specific steps are as follows:
[0011] (1) Set the cloud shield so that each cloud shield saves four non-modifiable data inside the cloud shield when it leaves the factory. A. Root public key PKr: there is always only one pair of root public key PKr and root private key SKr; B. Initial key pair SK0 / PK0: The initial key pair of each Cloud Shield is randomly generated, where SK0 is the initial private key and PK0 is the initial public key; C. Cloud Shield ID: the ID of each Cloud Shield They are all different; D. The initial public key SKr(PK0) signed by the root private key SKr;
[0012] (2) Assuming that network transmission is insecure, hackers may modify data during data transmission. The legitimacy of Cloud Shield can be verified remotely by transmi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com