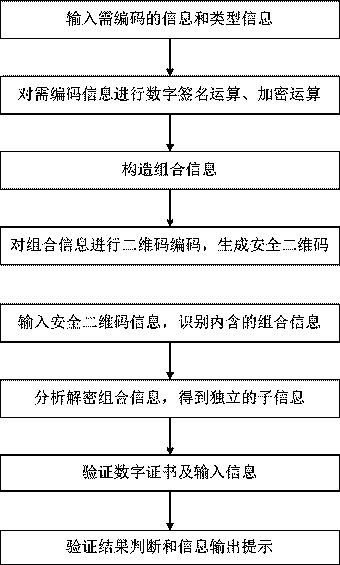
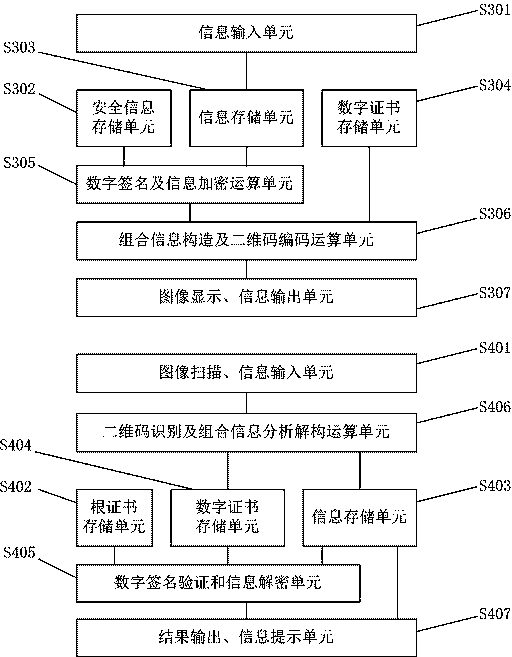
Off-line verifiable secure two-dimensional code structure verification method and device
A technology of verification method and construction method, which is applied in the field of information technology and security verification, and can solve problems such as information being easily modified and forged, security cannot be judged, and two-dimensional code security verification.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0126] ABC Bank generates a public information security QR code that can be read by public users for its online banking entrance address, and users can safely scan the code and access the online banking system.
[0127] The specific implementation steps are as follows:
[0128] 1. Enter the information and type information to be encoded
[0129] The information to be encoded includes basic information, target information, and dynamic information. The basic information is: Base:{Name:ABCBank}, the target information is: OBJ:{URI:https: / / www.abc.com}, and the dynamic information is: DYN:{Created:2016-1-1 12:00: 00|Expired: 2026-1-1 12:00:00}. The type information is a public information security QR code.
[0130] Connect the input information with vertical bars and bracket symbols, as shown in Table 1.
[0131] Table 1 Encoding information required in Embodiment 1
[0132][OBJ:{URI:https: / / www.abc.com}Base:{Name:ABC Bank}DYN:{Created:2016-1-1 12:00:00|Expired:2026-1-1 12:00...
Embodiment 2
[0190] The ABC Pay payment platform, for taxi mobile payment applications, generates public information security QR codes for each taxi operator that can be read by public users, and passengers can safely scan the code to pay for car rentals.
[0191] The specific implementation steps are as follows:
[0192] 1. Enter the information and type information to be encoded
[0193] The information to be encoded includes basic information, target information, and dynamic information. The basic information is: Base:{TaxiID: Shanghai A12345|LicenseID:123456|UserID:12345678|Domain:abcpay.com}, the target information is: OBJ:{URI:https: / / sqr.abcpay.com / zrk1rjziurlr2w3ira}, dynamic The information is: DYN:{Created:2016-1-1 12:00:00|Expired:2017-1-1 12:00:00}. The type information is a public information security QR code.
[0194] Connect the input information with vertical bars and bracket symbols, as shown in Table 8.
[0195] Table 8 Embodiment 2 needs to encode information
[019...
Embodiment 3
[0225] ABC Mall shopping center, when the user pays, uses the device of the present invention to generate in real time a public information security two-dimensional code containing information such as the name of the receiving merchant, date, amount, and valid time, and the user can scan the code to pay safely.
[0226] The specific implementation steps are as follows:
[0227] 1. Enter the information and type information to be encoded
[0228] The information to be encoded includes basic information, target information, and dynamic information. The basic information is: Base:{Name:ABCMall|Addr:No.1288,ABC Rd.,Shanghai|Domain:abcpay.com}, the target information is: OBJ:{URI:https: / / pay.abcpay.com / dkri67zin9oo8tzxy9ojquz8mcaedhzcljix1jeu }, the dynamic information is: DYN:{Created:2016-5-1 12:00:00|Expired:2016-5-1 12:10:00|PaymentID:e7db7c48642c78a669fd|Total:580.00RMB}. The type information is a public information security QR code.
[0229] Connect the input information wi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com