DEM Integrity authentication method based on prevention of repeating embedding of double watermarks
An authentication method and anti-duplication technology, applied in the field of geographic information security, which can solve the problems of incomplete data and wrong data authentication, and achieve the effect of preventing repeated embedding, accurate integrity authentication results, and avoiding tampering and denial behavior.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0037] The present invention will be described in further detail below in conjunction with the accompanying drawings and embodiments.
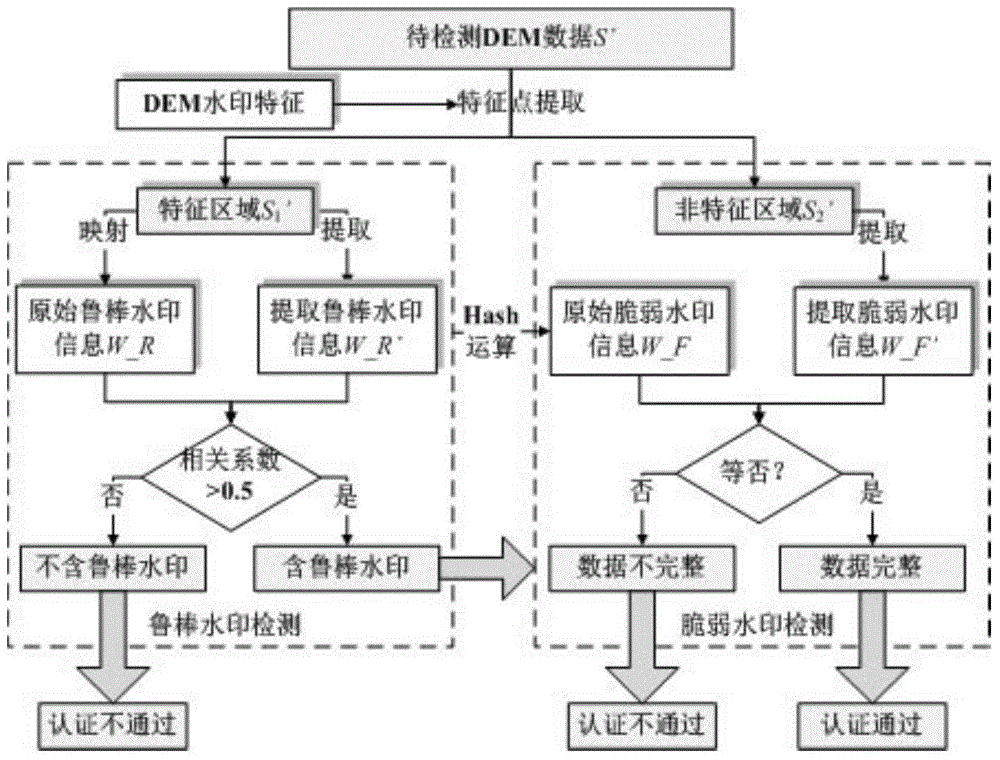
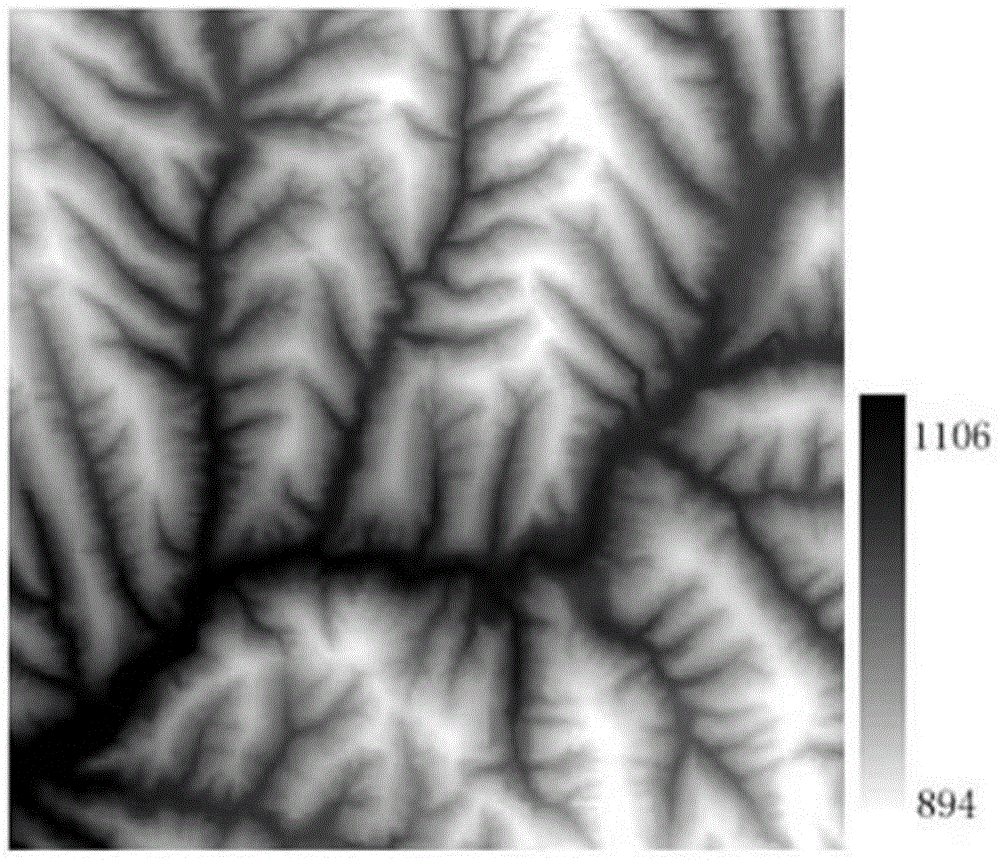
[0038] In this embodiment, a piece of 1:10,000 grid DEM experimental data (such as image 3 ), for the whole process of watermark information generation, embedding and detection, an embodiment of the method of the present invention is given, and the present invention is further described in detail.
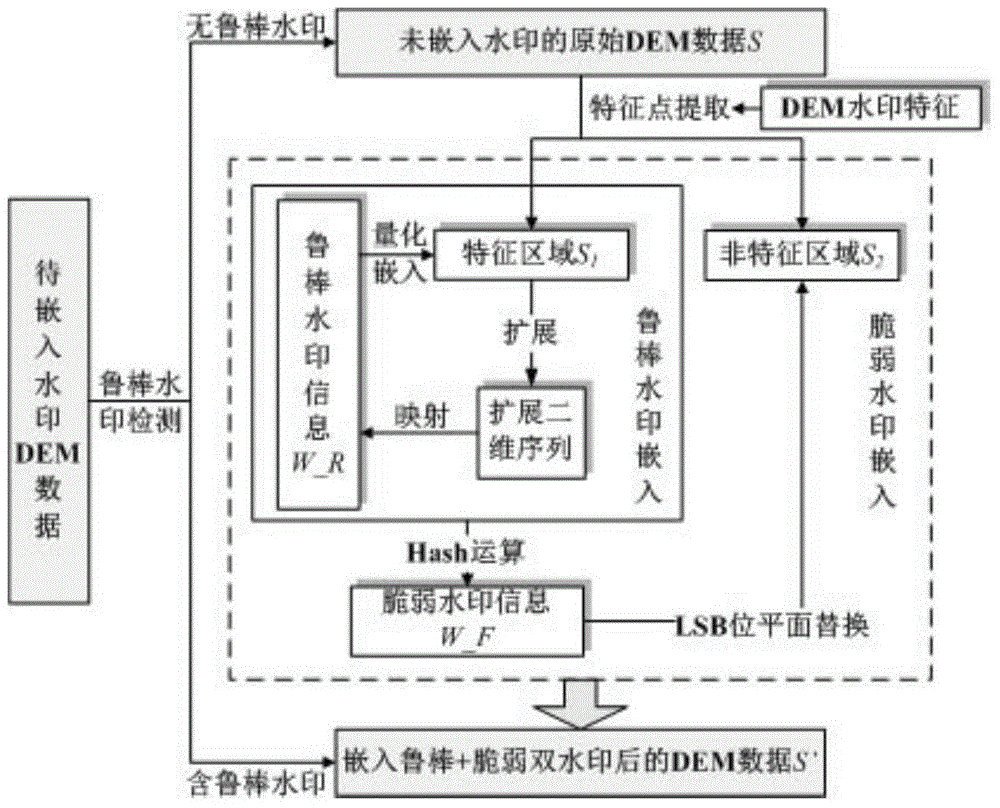
[0039] 1. Watermark information generation and embedding
[0040] Step 1: extract the terrain feature points to be embedded in the watermarked DEM data, and obtain the feature area and non-feature area of the data;
[0041] Step 2: Detect the correlation coefficient of the robust watermark in the extracted data feature area. If the correlation coefficient is less than 0.5, skip to step 3. Otherwise, skip to step 5, and no longer embed the watermark on the data;
[0042] Step 3: Use the mapping mechanism to generate a robust watermark W_R from ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com