A locker-based third-party authorized pick-up system and its authorized pick-up method
A locker, pick-up technology, applied in the direction of coin-operated equipment for distributing discrete items, coin-free or similar appliances, coin-operated equipment with meter control, etc. The mode of information tracking, the inability to track the system, etc., to achieve the effect of flexible use
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
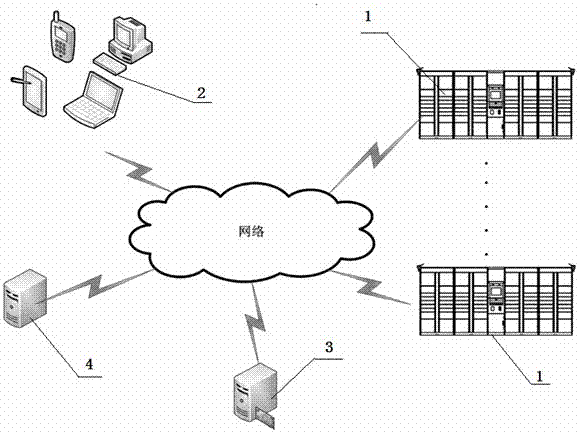
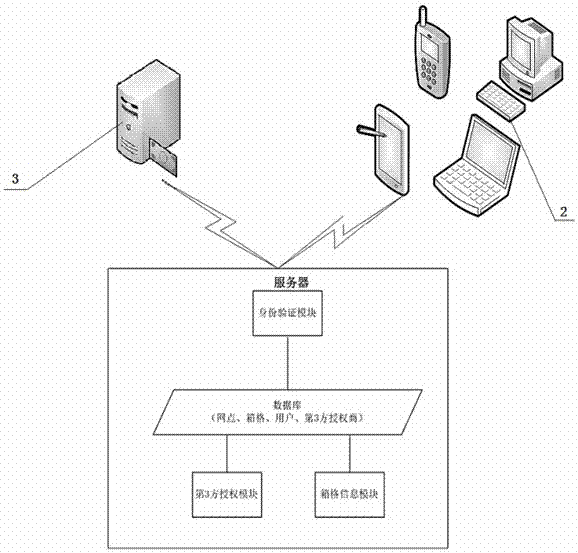
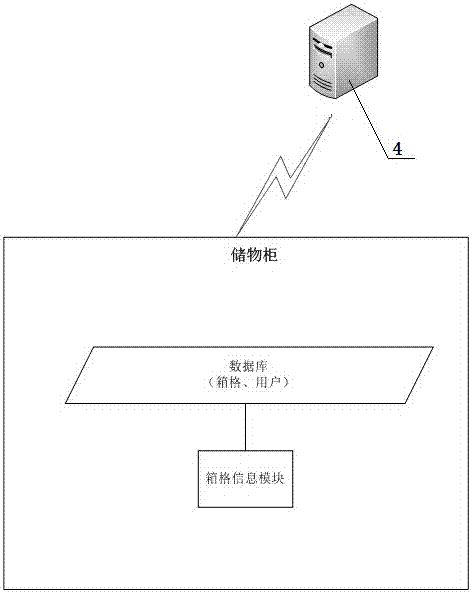
[0054] A third-party authorized pick-up system based on a locker, including a locker 1, an intelligent terminal 2, a third-party authorizer 3 and a server 4, the locker 1 is used to store the user's items to be picked up, and the smart terminal 2 is used to After the user sends the authorization pickup request to the server 4 and receives the authorization pickup result fed back by the server 4, the third-party authorizer 3 provides the server 4 with the information of the authorized pickup person, and the server 4 is used to handle the operation of the authorization pickup.
[0055] If the picker is waiting to pick up the item in the locker 1, the picker obtains the authorized picker information through the third-party authorizer 3, and completes the authorization operation of the pick-up through the server 4; after authorization, the authorized person goes to the locker 1 to pick up the item. Take the corresponding express;
[0056] Items to be picked up are parcels, letters...
Embodiment 2
[0091] For the locker-based third-party authorized pick-up system in Embodiment 1, the server 4 is also provided with a third-party authorization module, which is used to interact with the smart terminal 2 and the locker 1 respectively. Information and pick-up pending authorization information are also used to call third-party authorizer information in the server database.
[0092] For the third-party authorized pick-up method of the system with the third-party authorization module, the following steps are included:
[0093] A. The user enters personal login information through the smart terminal 2, and the personal login information is sent to the identity verification module of the server 4 to verify whether the user's identity is legal; if it is legal, proceed to the next step; if not, the user re-enters the personal login information and verify;
[0094]B. For a user who has successfully logged in, retrieve the user's box information to be picked up from the server databa...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com