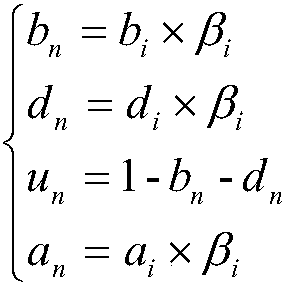A method for routing security and privacy protection in an Internet of Things network
A privacy protection and Internet of Things technology, applied in data exchange networks, digital transmission systems, electrical components, etc., can solve problems such as lack of consideration of internal attacks, achieve the effect of resisting collusion attacks and improving accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0033] The present invention will be further described below in conjunction with the accompanying drawings and embodiments.
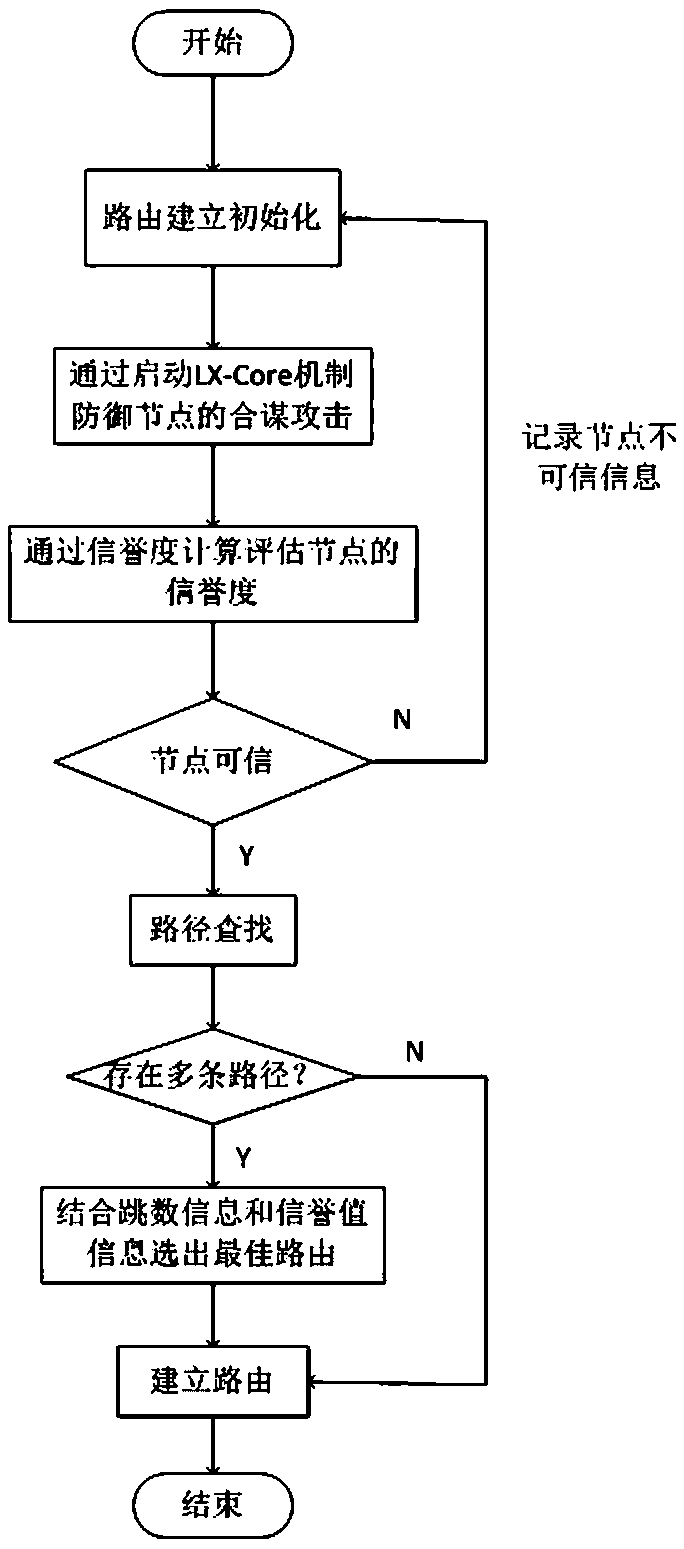
[0034] Please refer to figure 1 , the present invention provides a method for routing security and privacy protection in an Internet of Things network, characterized in that it comprises the following steps:
[0035] Step S1: The source node u broadcasts a SETM message to neighbor nodes, and starts the route discovery process;
[0036] Step S2: After receiving the SETM message, any neighbor node v executes the LX-Core mechanism on this node to defend against collusion attacks from other nodes;
[0037] In the LX-Core mechanism, there are the following theorems:
[0038] Theorem 1: In the process of routing selection, when a small number of nodes collude, there will be a relationship WD(N)≥WD′(N), where WD′(N) is when there is collusion WD(N) value at time;
[0039] The stated Theorem 1 is proved as follows:
[0040] Proof: if the system model fig...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com