Code processing method and apparatus
A processing method and password technology, which are applied in the field of terminal interaction of password information, can solve the problem of password being easily stolen, and achieve the effect of improving security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0044] Embodiment 1 of the present invention discloses a cryptographic processing method, refer to figure 1 , the method may include the following steps:
[0045] S101: Receive a current character input by a user during a password input process, and store the current character.
[0046] S102: Displaying the set password hidden substitution symbol at a preset position, so as to realize hidden substitution display of the current character by using the password hidden substitution symbol.
[0047] In this embodiment, the preset position is specifically a password input edit box.
[0048] The hidden password substitution symbol can be various character patterns such as black solid dots and asterisk characters that can hide and protect the password characters input by the user.
[0049] When the user needs to enter the password in the password input edit box based on certain application requirements or service transaction requirements, during the entire password input process, th...
Embodiment 2
[0052] In the second embodiment, refer to figure 2 , the step S101 can be specifically implemented through the following steps:
[0053]S201: Receive the current character input by the user during the password input process, and store the current character in the first preset memory instead of the existing character in the first preset memory, the first preset memory The character content in is updated if and only when a character input event from the user is detected.
[0054] On this basis, as figure 2 As shown, the password processing method of the present application may also include:
[0055] S202: Receive the first display request sent by the user;
[0056] S203: Read characters in the first preset memory, and display the read characters.
[0057] In the process of inputting the password, the user often forgets which character has been input due to external interference, or is uncertain whether the currently input character is correct due to a mistake in clicking a...
Embodiment 3
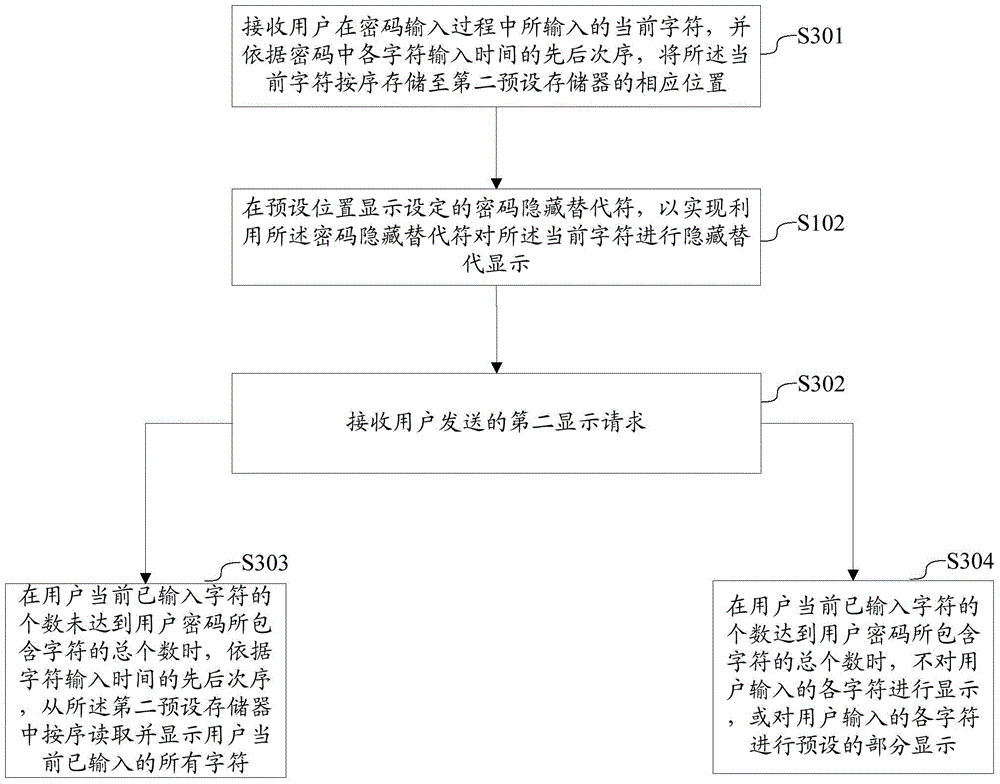
[0065] In the second embodiment, refer to image 3 , the step S101 can be specifically implemented through the following steps:
[0066] S301: Receive the current characters input by the user during the password input process, and store the current characters in sequence in corresponding positions of the second preset memory according to the sequence of input time of each character in the password.
[0067] On this basis, as image 3 As shown, the password processing method of the present application may also include:
[0068] S302: Receive a second display request sent by the user;
[0069] S303: When the number of characters currently input by the user does not reach the total number of characters contained in the user password, according to the order of character input time, read and display the characters currently entered by the user in sequence from the second preset memory. all characters entered;
[0070] S304: When the number of characters currently input by the u...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com