Application unlocking method, device and facility
A technology for unlocking and equipment, applied in electrical components, transmission systems, digital data authentication, etc., can solve problems such as multiple levels of unlocking processes, low efficiency, and slow unlocking speed
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
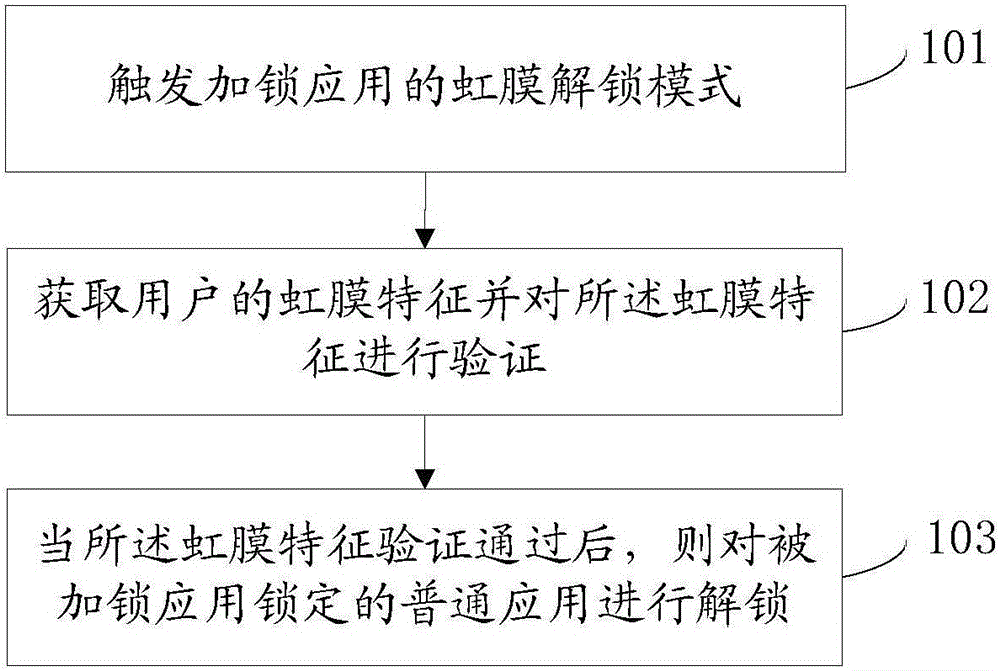
[0064] refer to figure 1 , which shows a flow chart of the steps of Embodiment 1 of an applied unlocking method according to the present invention, which may specifically include the following steps:
[0065] Step 101, triggering the iris unlocking mode of the locking application;
[0066] The embodiments of the present invention are applicable to mobile terminals, including mobile phones, tablet computers, and the like.
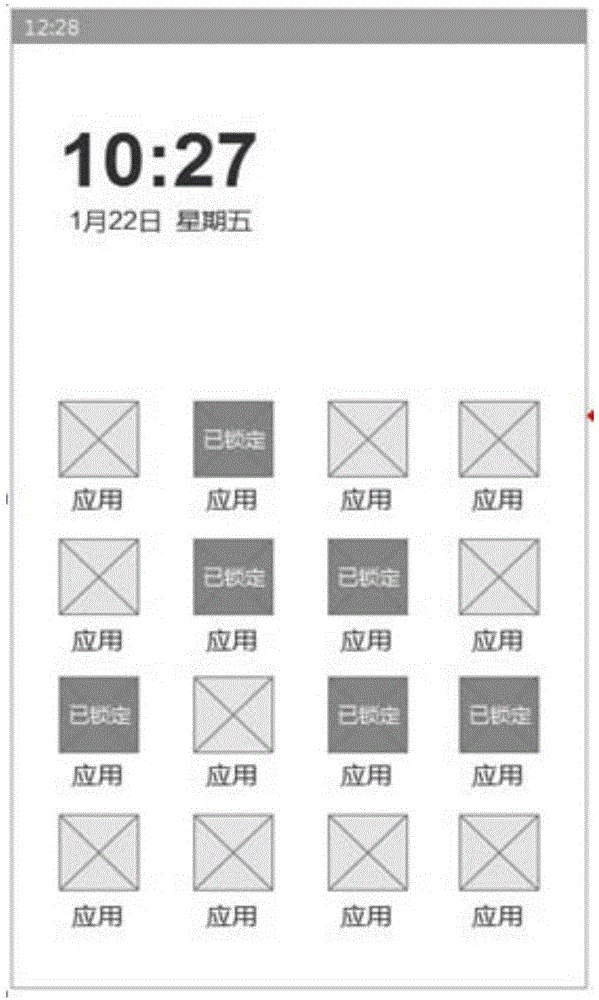
[0067] In practical applications, in order to ensure application account security and user privacy, it is often possible to download a locked application on a mobile terminal, and then the user can open the locked application and select one or more common applications to lock. Wherein, the application lock, as a special application of the mobile terminal, can lock other common applications. like Figure 1A , 6 normal apps are locked by the locked app and are in the locked state. Other ordinary applications are not locked by the locked application and are...
Embodiment 2
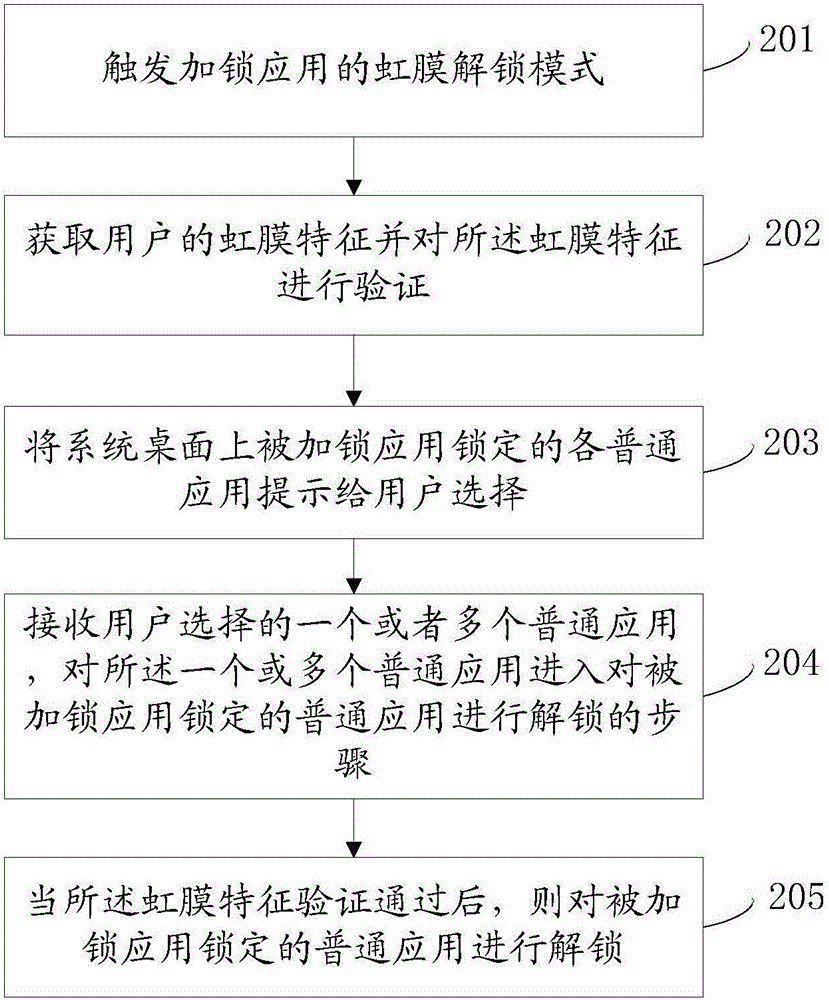
[0085] refer to figure 2 , shows a flow chart of the steps of Embodiment 2 of an applied unlocking method according to the present invention, which may specifically include the following steps:
[0086] Step 201, triggering the iris unlocking mode of the locking application;
[0087] Step 202, acquiring the user's iris feature and verifying the iris feature;
[0088] Step 203, prompting the user to select each common application locked by the locked application on the system desktop;
[0089] In the embodiment of the present invention, the user may be allowed to independently select common applications that need to be unlocked. Specifically, the mobile terminal displays all locked common applications on the system desktop to the user for selection by the user. When a user's selection operation such as clicking is received, the common application selected by the user is used as the application to be unlocked. It can be understood that after the user selects the normal appl...
Embodiment 3
[0109] refer to image 3 , which shows a flow chart of the steps of Embodiment 3 of an applied unlocking method according to the present invention, which may specifically include the following steps:
[0110] Step 301: Add an iris authentication interface and an iris unlocking interface in the system service; wherein, the iris authentication interface is used to obtain the iris characteristics of the user and verify the iris characteristics; the iris unlocking interface is used when the After the above iris feature verification is passed, the normal application locked by the locked application is unlocked;
[0111] Wherein, the system service is the background service of the mobile terminal, which provides various service interfaces for the user. In the embodiment of the present invention, in order to be able to unlock locked common applications, obtain and verify iris features, it is necessary to add an iris unlocking interface and an iris authentication interface in the sys...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com