Wifi hijack resisting method and device
A technology for URL and web page request, applied in the field of communication, can solve problems such as hijacking
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
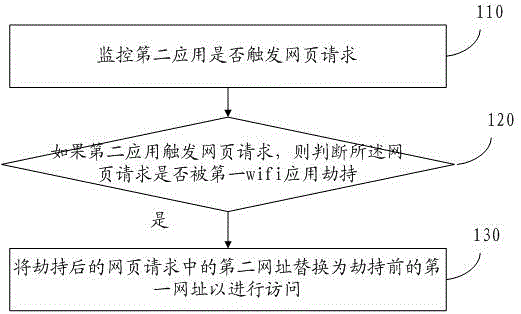
[0073] refer to figure 1 , which shows a flow chart of steps of an anti-wifi hijacking method according to an embodiment of the present invention.
[0074] Step 110, monitoring whether the second application triggers a web page request;
[0075] In the embodiment of the present invention, the user can first use the first wifi application to connect to a certain wifi in the mobile terminal, and then the user can open a certain application and visit the corresponding web page.
[0076] Then, after the user opens a certain second application, the second application may automatically visit a certain webpage, which triggers a webpage request, or the user clicks on a control, element, etc. in the interface of the second application, thereby triggering Web page request.
[0077] Wherein, the above-mentioned mobile terminal may be a mobile terminal such as a mobile phone or a tablet, which is not limited in the present invention.
[0078] Step 120, if the second application trigger...
Embodiment 3
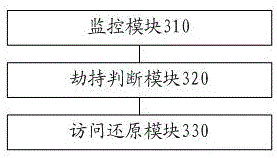
[0142] refer to image 3 , which shows a structural block diagram of an anti-wifi hijacking device according to an embodiment of the present invention.
[0143] A monitoring module 310, configured to monitor whether the second application triggers a web page request;
[0144] A hijacking judging module 320, configured to judge whether the webpage request is hijacked by the first wifi application if the second application triggers the webpage request;
[0145] The access restoration module 330 is configured to replace the second URL in the hijacked webpage request with the first URL before hijacking if the webpage request is hijacked by the first wifi application for access.
[0146] Preferably, the hijacking judging module includes:
[0147] The webpage view component judging sub-module is used to judge whether the URL accessed by the webpage view component is hijacked by the first wifi application; if the URL accessed by the webpage view component is hijacked, ...
Embodiment 4
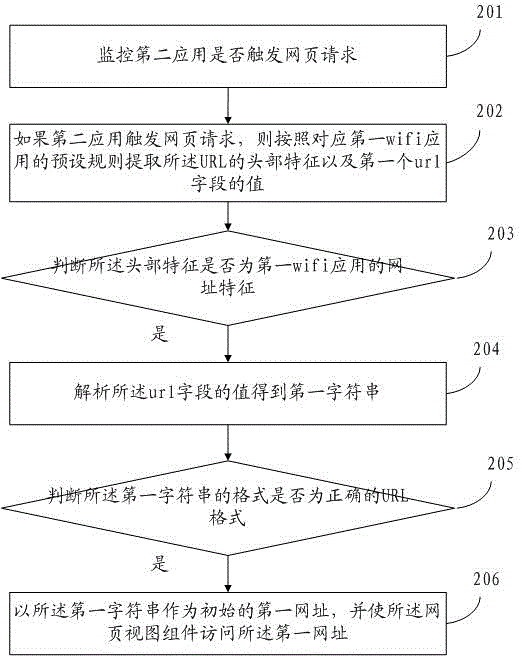
[0168] refer to Figure 4 , which shows a structural block diagram of an anti-wifi hijacking device according to an embodiment of the present invention.
[0169] A monitoring module 310, configured to monitor whether the second application triggers a web page request;
[0170] The hijacking judging module 320 is used to judge whether the webpage request is hijacked by the first wifi application if the second application triggers the webpage request, specifically including:
[0171] The first feature extraction submodule 321 is used to extract the header feature of the URL and the value of the first url field according to the preset rules corresponding to the first wifi application;
[0172] The first feature judging sub-module 322 is used to judge whether the header feature is the URL feature of the first wifi application, and judge whether the value of the url field corresponds to a correct URL; if the header feature is the first wifi application URL characterist...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com