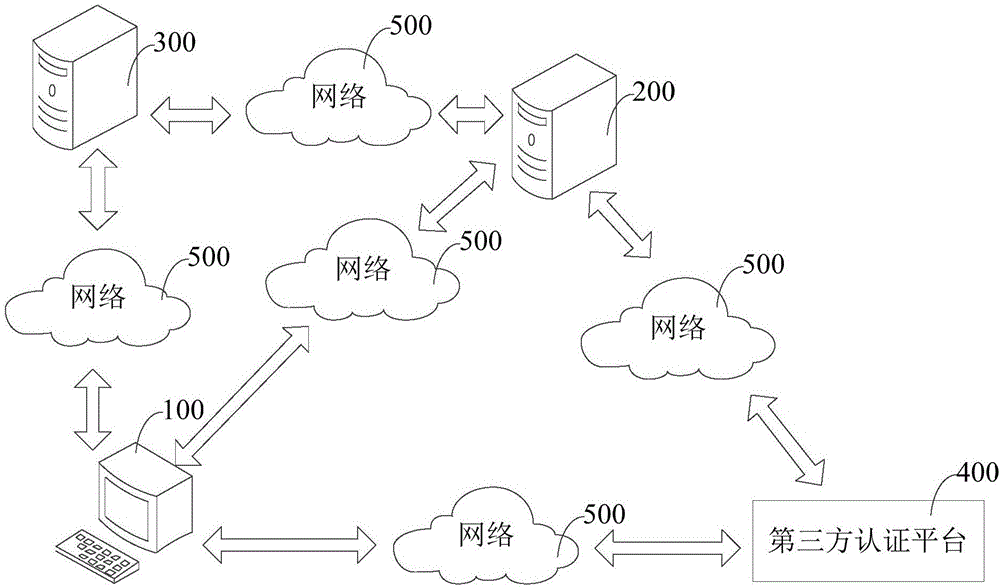
Third party login authentication method and system, proxy server and client
A proxy server, login authentication technology, applied in the field of proxy server, client and system, third-party login authentication method, can solve problems such as inconvenience of website or APP, and achieve the effect of improving efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
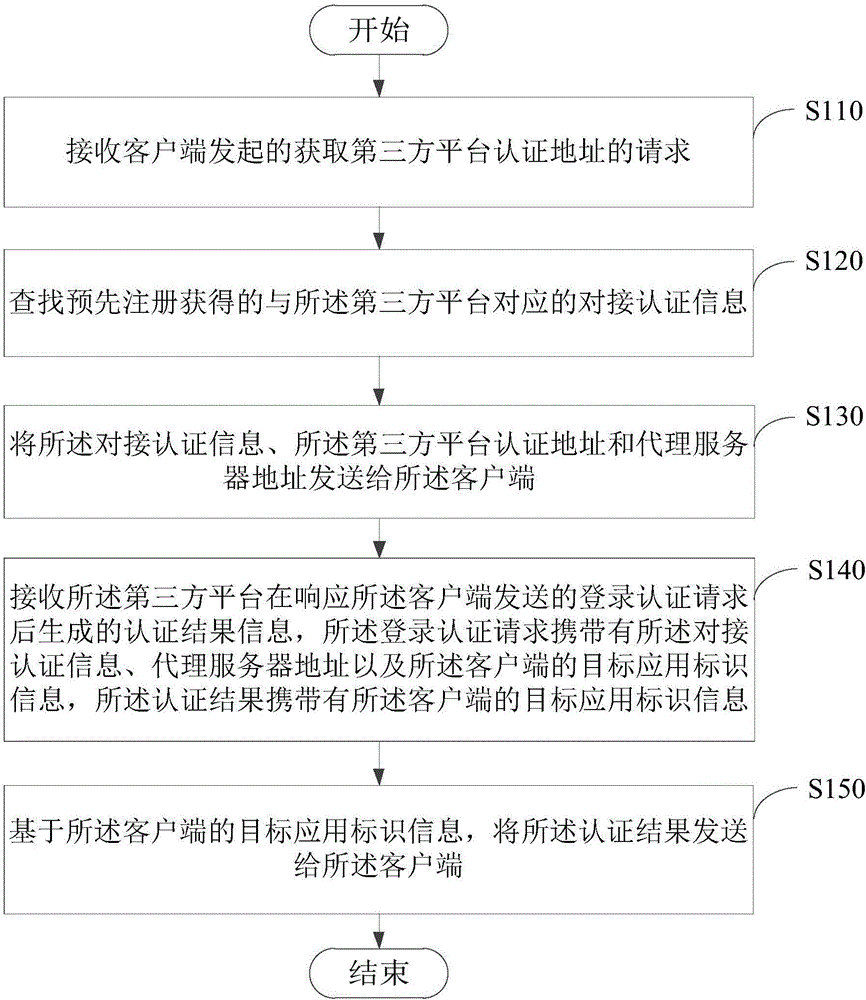
[0024] Please see figure 2 , figure 2 It is a flowchart of a third-party login authentication method provided by an embodiment of the present invention, and the method is applied to a proxy server. The methods include:
[0025] Step S110: Receive the request initiated by the client to obtain the authentication address of the third-party platform.
[0026] Wherein, after the client responds to the third-party login authentication event, it sends a request to the proxy server to obtain the authentication address of the third-party platform. The third-party login authentication event may be an event triggered when the user of the client needs to use a third-party login method (such as QQ, Weibo, WeChat, etc.) to log in to the application on the client in the process of using the client. The request is triggered by the user of the client, or the client may be triggered when the installation is completed. It can be understood that the request carries identification informatio...
no. 2 example
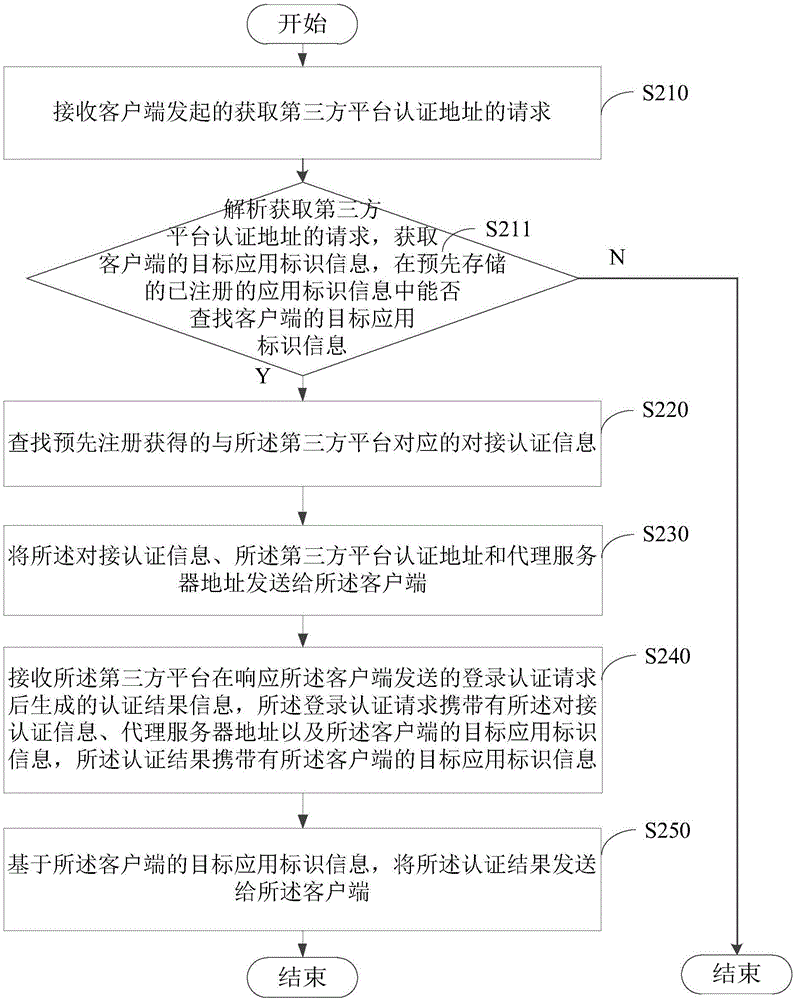
[0037] Please see image 3 , image 3 It is a flowchart of a third-party login authentication method provided by an embodiment of the present invention, and the method is applied to a proxy server. The methods include:
[0038] Step S210: Receive the request initiated by the client to obtain the authentication address of the third-party platform.
[0039] Step S211: Analyzing the request for obtaining the authentication address of the third-party platform, obtaining the target application identification information of the client, searching for the target application identification information of the client in the pre-stored registered application identification information, if the search is successful, Then perform the search for the docking authentication information corresponding to the third-party platform obtained through pre-registration.
[0040] The proxy server may respond to the registration request of the client, and save the target application identification info...
no. 3 example
[0047] Please see Figure 4 , Figure 4 It is a flowchart of a third-party login authentication method provided by an embodiment of the present invention, and the method is applied to a client. The methods include:
[0048] Step S310: Initiate a request to the proxy server to obtain the authentication address of the third-party platform.
[0049] Certainly, after responding to the third-party login authentication event, the client may initiate an access request based on the third-party platform authentication to the target application server in advance, and receive the proxy server address returned by the target application server.
[0050] Based on the returned proxy server address, the client initiates a request to the proxy server to obtain the authentication address of the third-party platform.
[0051] In this embodiment, the third-party login authentication event may be triggered by the client terminal when the user selects third-party login authentication using the c...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com