Method and device for detecting LDoS attack targeting Internet autonomous domain
An attack detection and autonomous domain technology, applied in the field of Internet security, can solve problems such as lack of LDoS attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
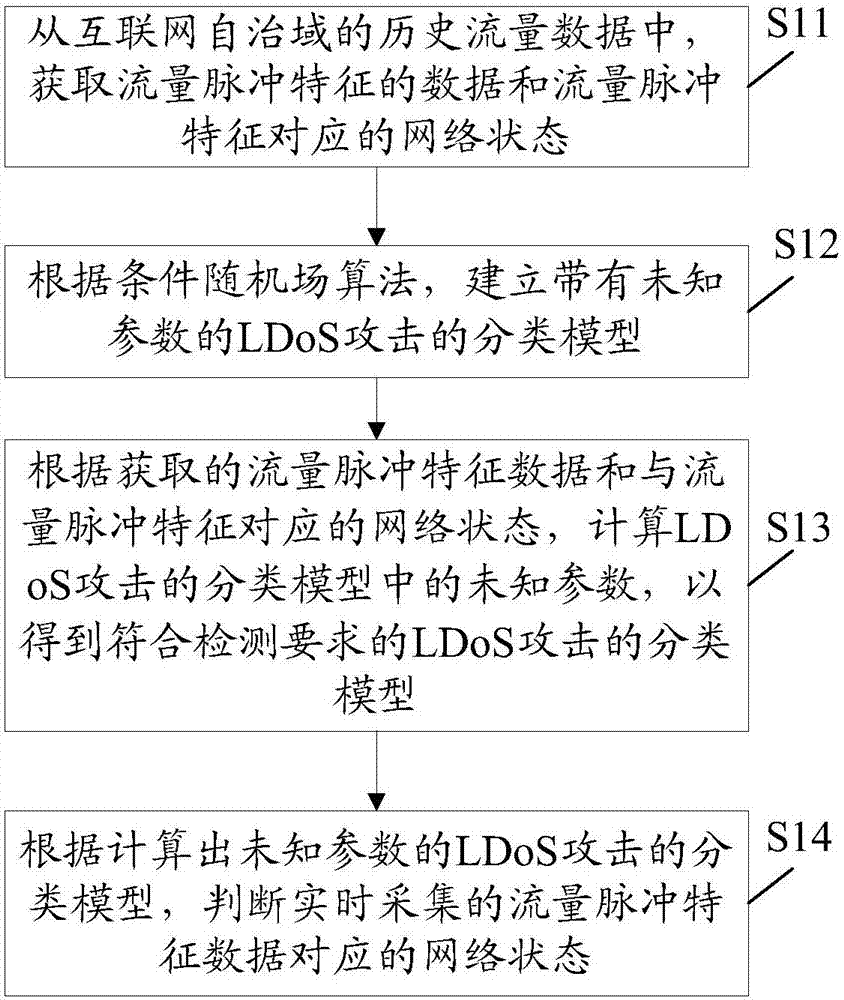
[0045] The embodiment of the present invention provides a method for detecting an LDoS attack facing an Internet autonomous domain, see figure 1 , the method includes:
[0046] Step S11, from the historical traffic data of the Internet autonomous domain, obtain the data of traffic pulse characteristics and the network status corresponding to the traffic pulse characteristics, the traffic pulse characteristics include: pulse length, pulse period, and pulse intensity, the network status includes LDoS Attacked and not attacked by LDoS.
[0047] It should be noted that the traffic pulse of the LDoS attack facing the Internet autonomous domain has at least three important characteristics, including the pulse length L, the pulse period T, and the pulse intensity R. Among them, the pulse length L of the LDoS attack must be large enough to cause data packet loss and induce the BGP session using the Transmission Control Protocol (Transmission Control Protocol, referred to as "TCP") as...
Embodiment 2
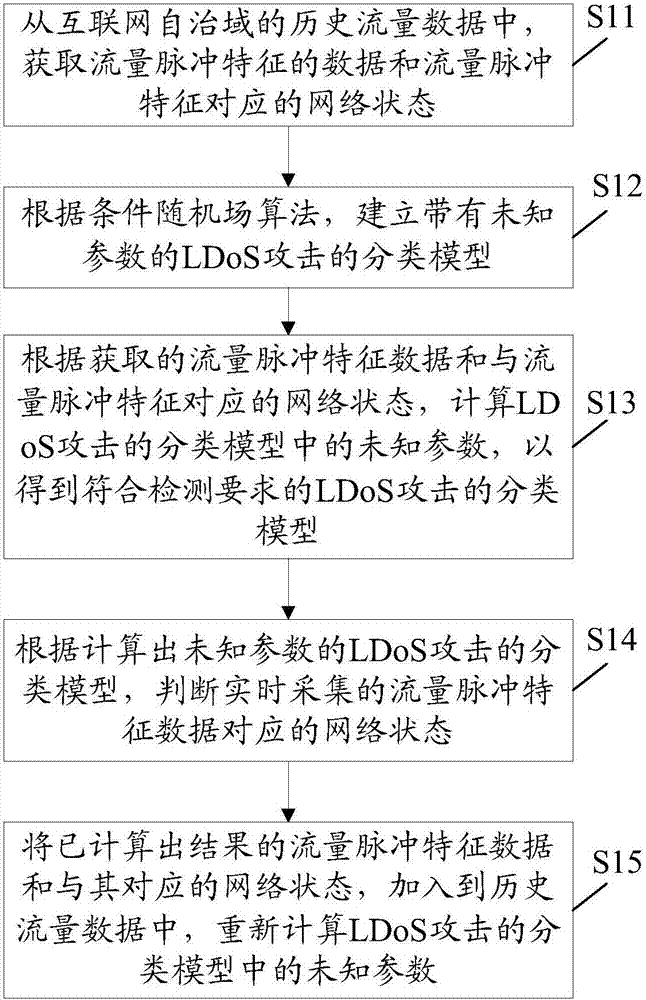
[0073] An embodiment of the present invention provides an Internet autonomous domain-oriented LDoS attack detection device, which can be used to implement the method described in Embodiment 1, see Figure 4 , the device consists of:
[0074] The obtaining module 201 is used to obtain the data of traffic pulse characteristics and the network state corresponding to the traffic pulse characteristics from the historical traffic data of the Internet autonomous domain. The traffic pulse characteristics include: pulse length, pulse period, and pulse intensity. The network state Including being attacked by LDoS and not being attacked by LDoS.
[0075] It should be noted that the traffic pulse of the LDoS attack facing the Internet autonomous domain has at least three important characteristics, including the pulse length L, the pulse period T, and the pulse intensity R. Among them, the pulse length L of the LDoS attack must be large enough to cause data packet loss and induce the BGP ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com