Method, device and system for accessing to network
A technology for accessing the network and access authentication, which is applied in the field of network technology applications, can solve problems such as low login efficiency, and achieve the effect of solving low login efficiency and improving login efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
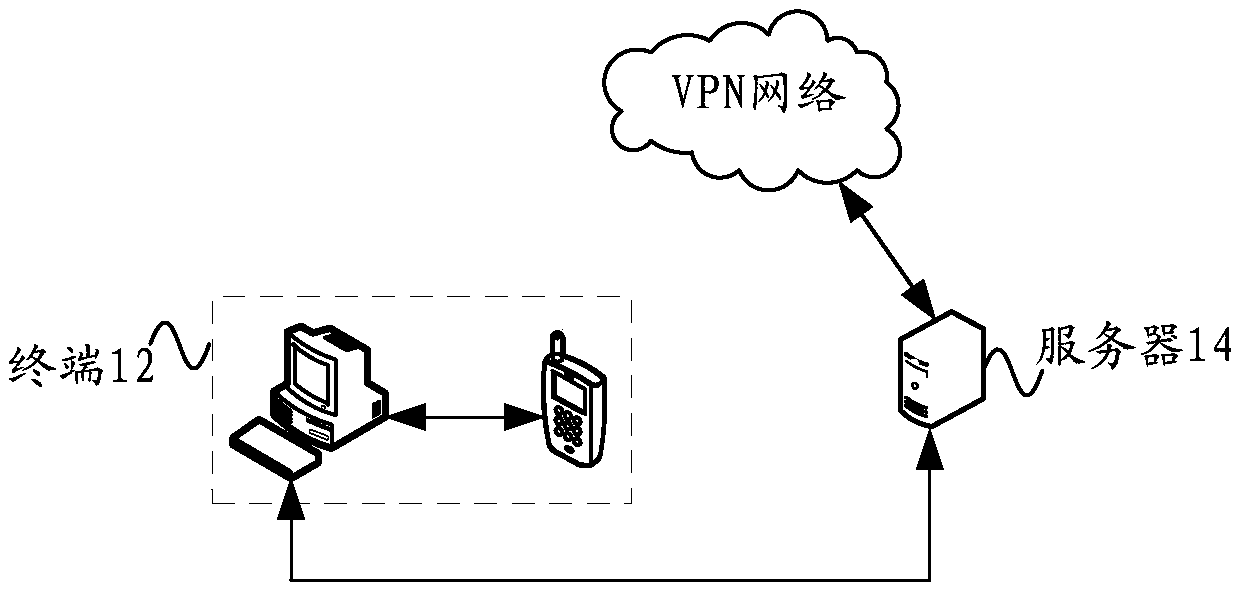
[0055] According to an embodiment of the present application, a system embodiment for accessing a network is provided, figure 1 It is a schematic structural diagram of a system for accessing a network according to an embodiment of the present invention.
[0056] Such as figure 1 As shown, the access network system includes: a terminal 12 and a server 14, wherein,
[0057] The terminal 12 is used to determine that the data connection to be accessed needs to be connected to a virtual private network, verify the data to be accessed through a preset verification method, and send an access request to the server 14 according to the verification result, wherein the preset verification method is used to verify the terminal Whether the pre-stored identity verification information of 12 satisfies the standard for accessing the server 14; the network to which the server 14 belongs is a virtual private network; the server 14 is connected with the terminal 12, and is used to receive the a...
Embodiment 2
[0087] According to another embodiment of the present invention, an embodiment of a method for accessing a network is also provided. It should be noted that the steps shown in the flowcharts of the accompanying drawings can be executed in a computer system such as a set of computer-executable instructions , and, although a logical order is shown in the flowcharts, in some cases the steps shown or described may be performed in an order different from that shown or described herein.
[0088] The method embodiment provided in Embodiment 1 of the present application may be executed in a mobile terminal, a computer terminal, or a similar computing device. Figure 5 It is a block diagram of a hardware structure of a computer terminal (or mobile device) for implementing a method for accessing a network according to an embodiment of the present invention. Such as Figure 5 As shown, the computer terminal 50 (or mobile device 50) may include one or more (502a, 502b, ..., 502n are used...
Embodiment 3
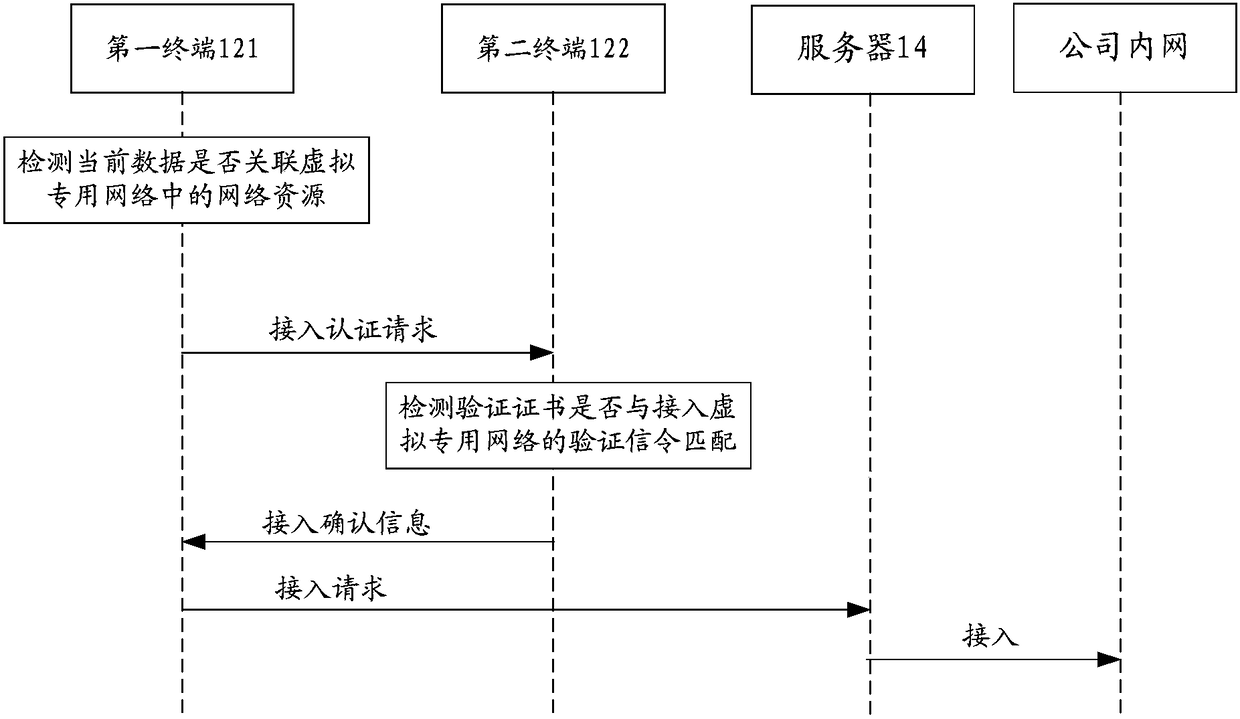
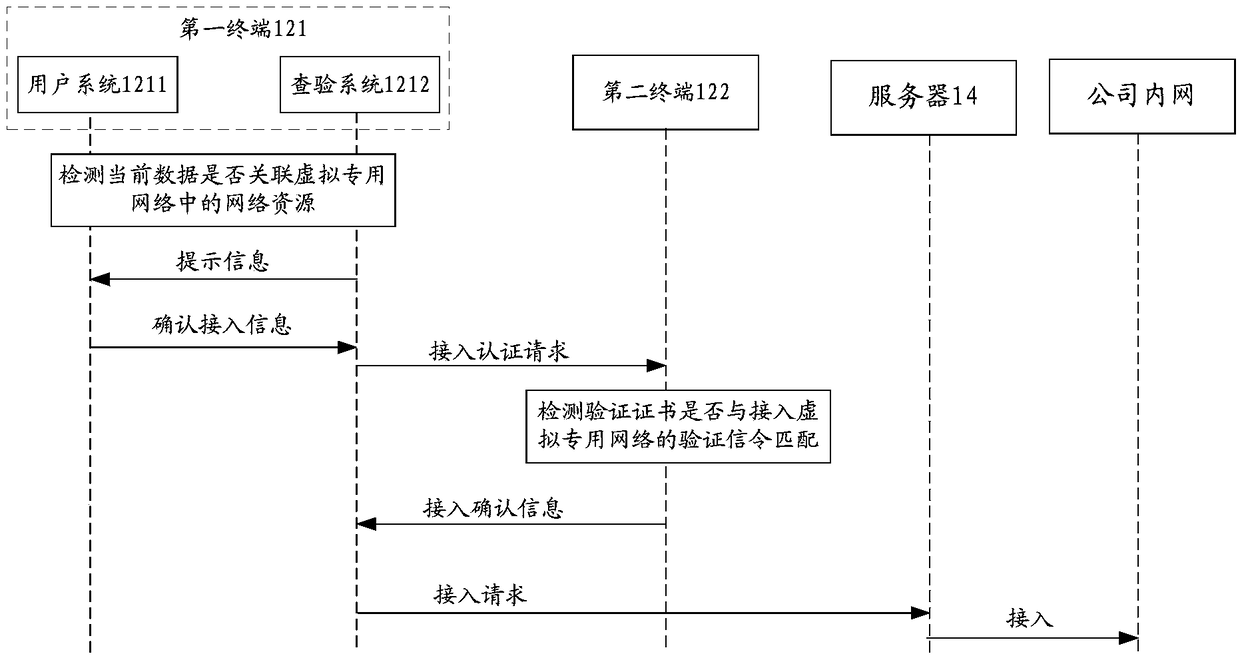
[0132] This application provides Figure 7 The method of accessing the network is shown. On the second terminal side, Figure 7 is a flowchart of a method for accessing a network according to Embodiment 3 of the present invention.
[0133] Step S702, the second terminal receives the access authentication request sent by the first terminal;
[0134] In the above step S702 of this application, based on the Figure 1 to Figure 3 The system for accessing the network provided is combined with the method for accessing the network provided by the first terminal side in Embodiment 2. In this embodiment of the present application, the second terminal side receives the access authentication request sent by the first terminal, wherein the access The access authentication request is used to instruct the second terminal to determine whether to confirm the first terminal's access to the virtual private network according to the pre-stored identity verification information of the first termi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com