Processing system for authenticating request
A technology for processing systems and verification requests, which is applied in the field of login verification and can solve problems such as weak data processing capabilities
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0046] It should be understood that the specific embodiments described herein are only used to explain the present invention, but not to limit the present invention.
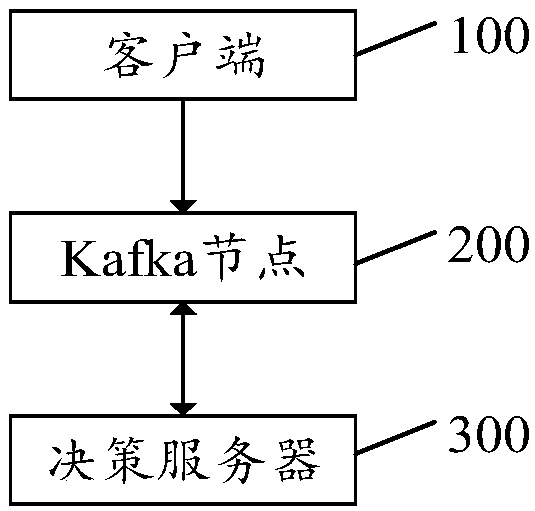
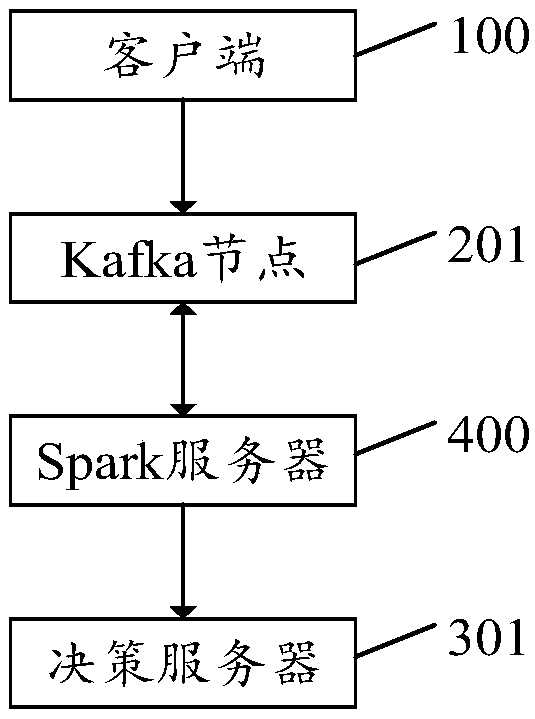
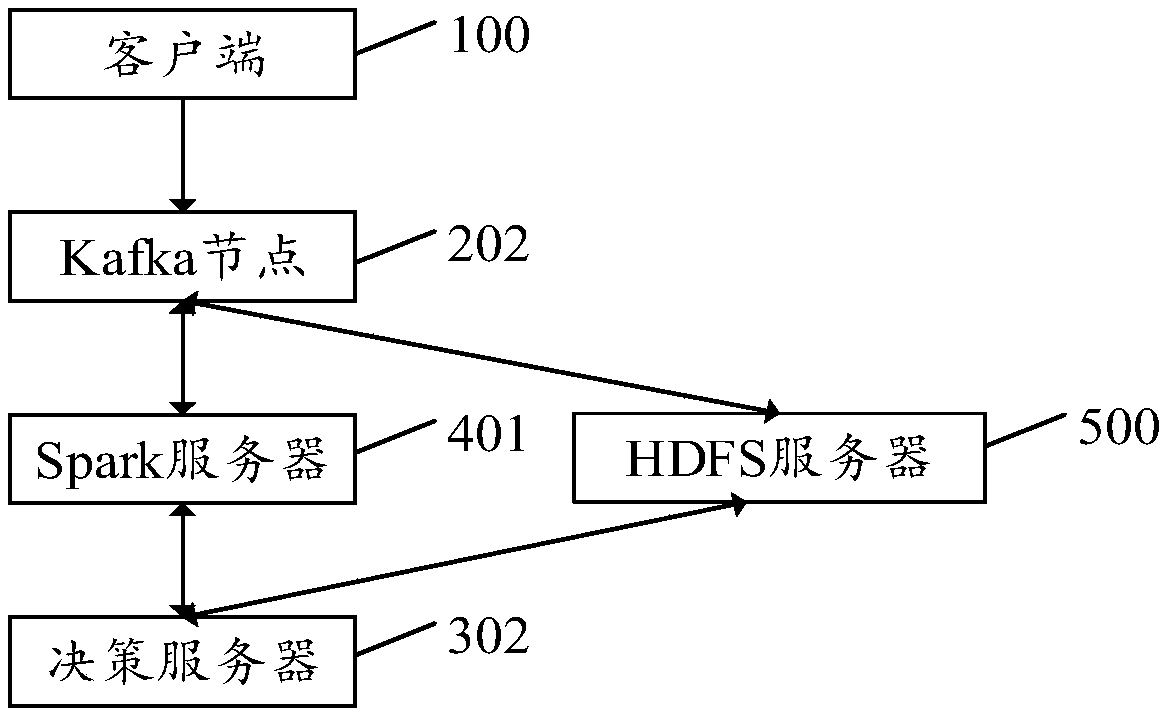
[0047] refer to figure 1 , figure 1 It is a structural block diagram of the first embodiment of the verification request processing system of the present invention. The processing system for the verification request includes: a client 100 , a Kafka node 200 and a decision server 300 .
[0048] It is understandable that, in order to deal with the login requests with the daily activity of hundreds of millions, the server cluster can be rebuilt to establish a server cluster with strong data processing ability, so as to have the processing ability to handle the login request of the daily activity of hundreds of millions, and use the millisecond-level standard for request response.
[0049]The client 100 is configured to obtain a first login verification request, and send the first login verification request to th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com