A continuous identity authentication method for mobile devices to collect user motion behavior
A technology of user identity authentication and user movement, which is applied in the field of continuous identity authentication in which mobile devices collect user movement behaviors. It can solve the problems of users being easily peeped, user privacy leakage, and large power consumption, etc., to overcome the single authentication period. Long-term, the effect of overcoming privacy leakage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
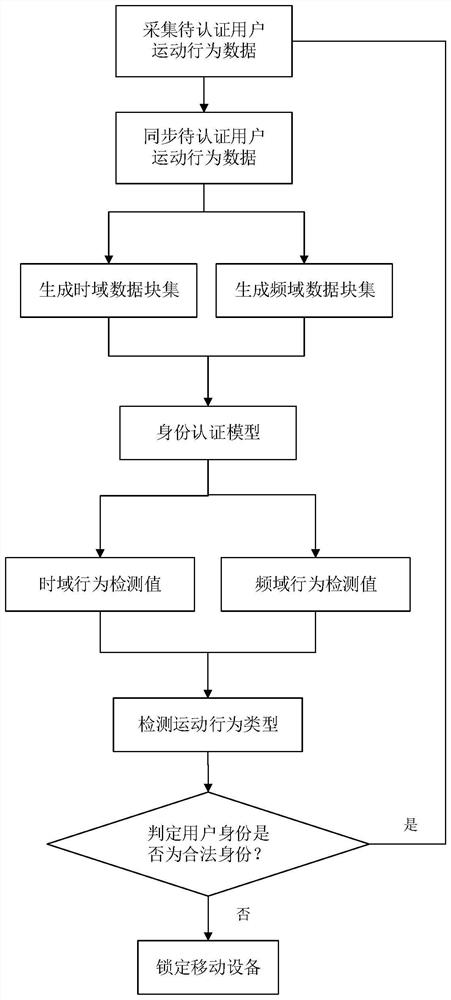
[0042] Attached below figure 1 The specific steps of the present invention are further described.
[0043] Step 1: Use the data collection method to collect the motion behavior data of the user to be authenticated.
[0044] The concrete steps of described data acquisition method:
[0045] Step 1: Use the default accelerometer sampling period in the mobile device to collect behavioral acceleration data of the user to be authenticated during exercise.
[0046] Step 2: Use the default gyroscope sampling period in the mobile device to collect behavioral angular velocity data during the motion of the user to be authenticated.
[0047] In the third step, the acceleration data and the angular velocity data are combined to form the user's motion behavior data.
[0048] Step 2, synchronizing the user's sports behavior data.
[0049] The accelerometer and gyroscope in the mobile device respectively describe the acceleration dimension and the angular velocity dimension of the same us...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com