A continuous identity authentication method for collecting user interaction behaviors by using a mobile terminal
A mobile terminal and identity authentication technology, applied in the information field, can solve the problems of user privacy leakage, users are easy to be peeped, easy to be imitated, etc., and achieve the effect of overcoming privacy leakage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0040] The present invention will be further described below in conjunction with the accompanying drawings.
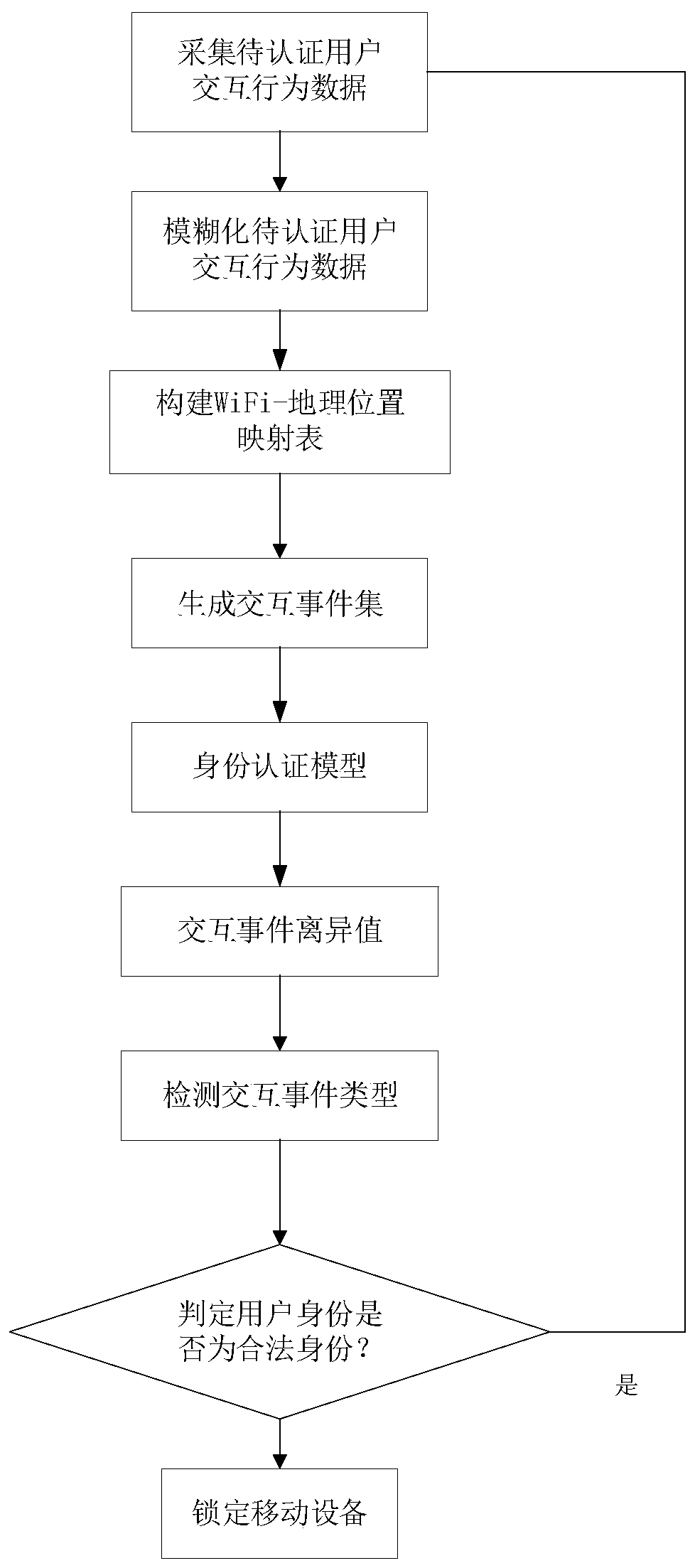
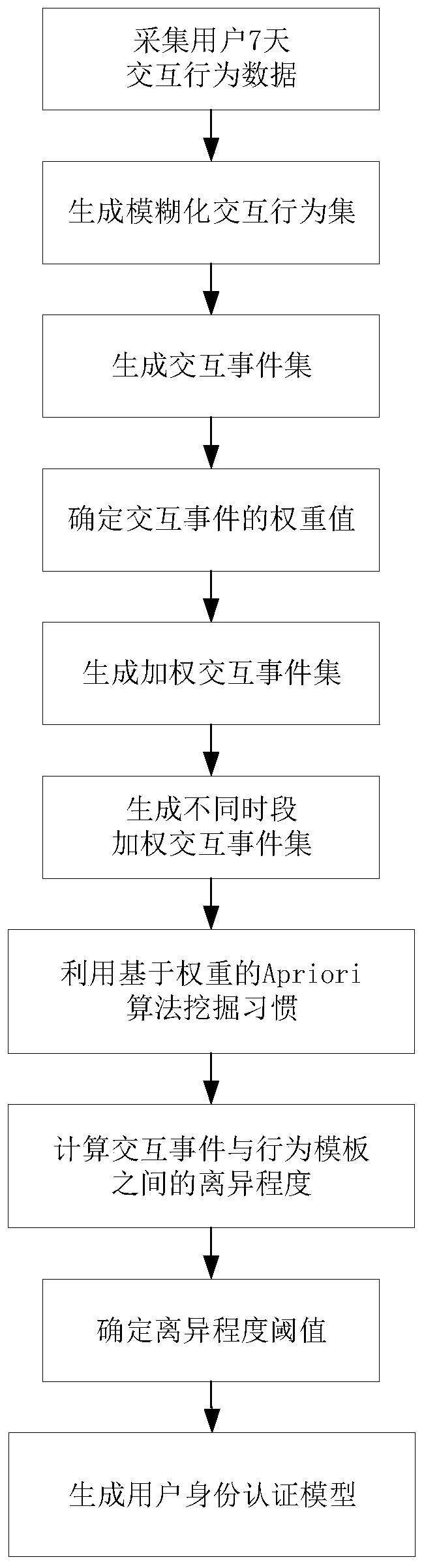
[0041] refer to figure 1 The specific steps for realizing the present invention are further described.
[0042] Step 1. Use the data collection method to collect N consecutive interactive behaviors of the user to be authenticated to obtain a set of interactive behaviors of the user to be authenticated. N is a natural number in the interval [1,20].
[0043] The data collection method is to use a mobile device to take 1 minute as a sampling period to synchronously collect the MAC address data, user status data, and application software name data of all WiFi signals existing in the space where the user to be authenticated is located; The multiple collected MAC addresses form a MAC address list; the MAC address list, user status data, application software name data and sampling time collected in each cycle are arranged in the order of collection time, MAC address list, us...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com