Anticipatory cyber defense
A network and identification technology used in the field of anticipating and addressing network security threats
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
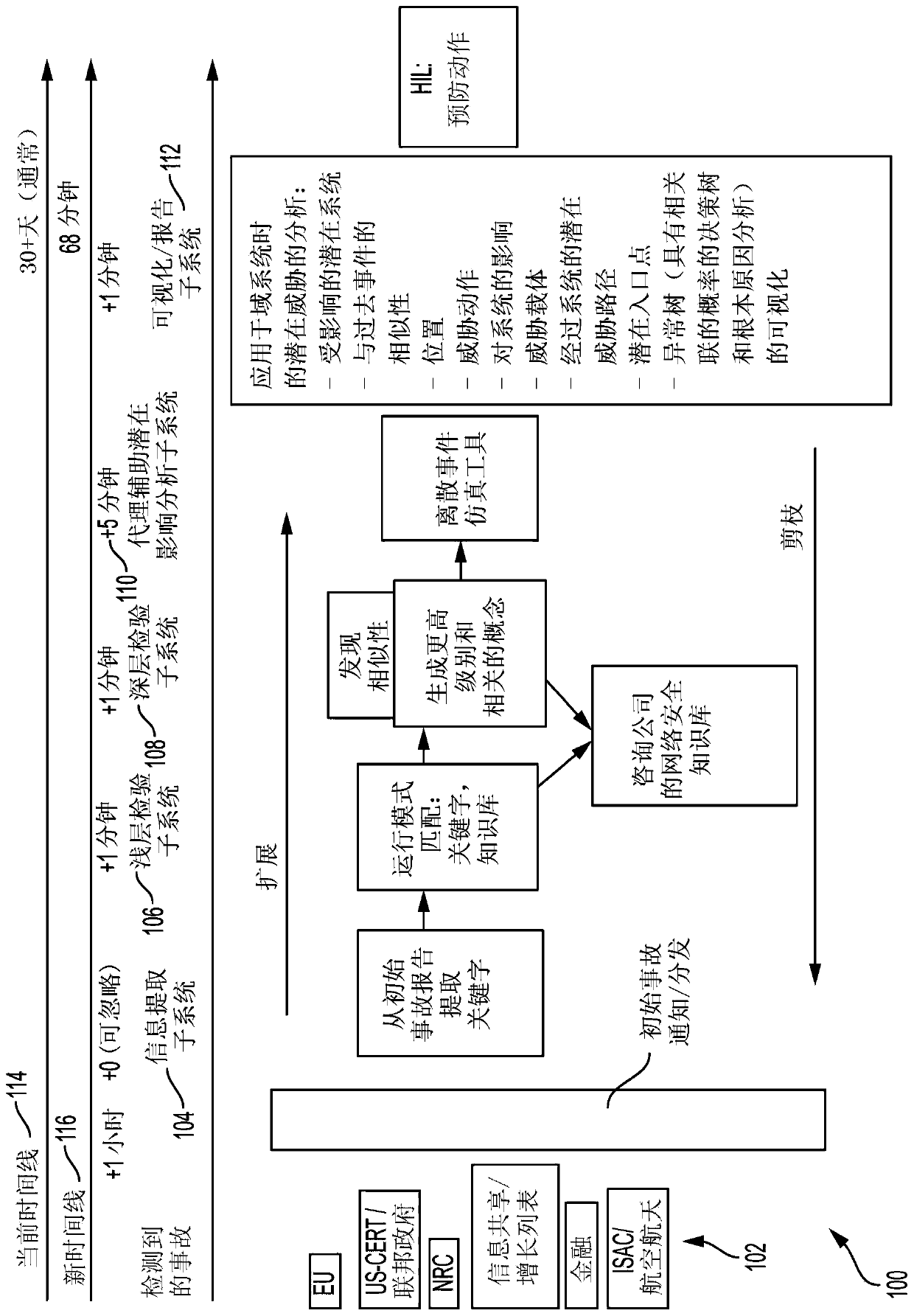
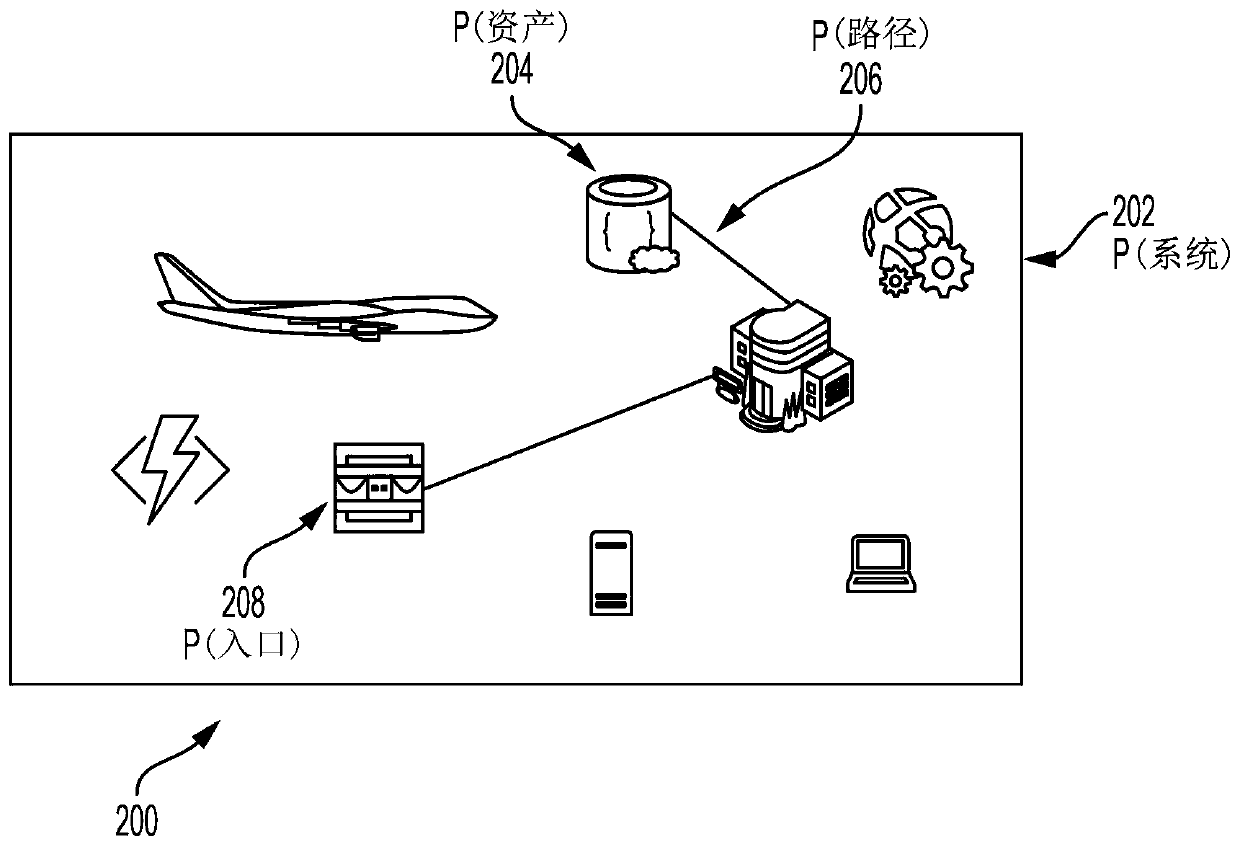
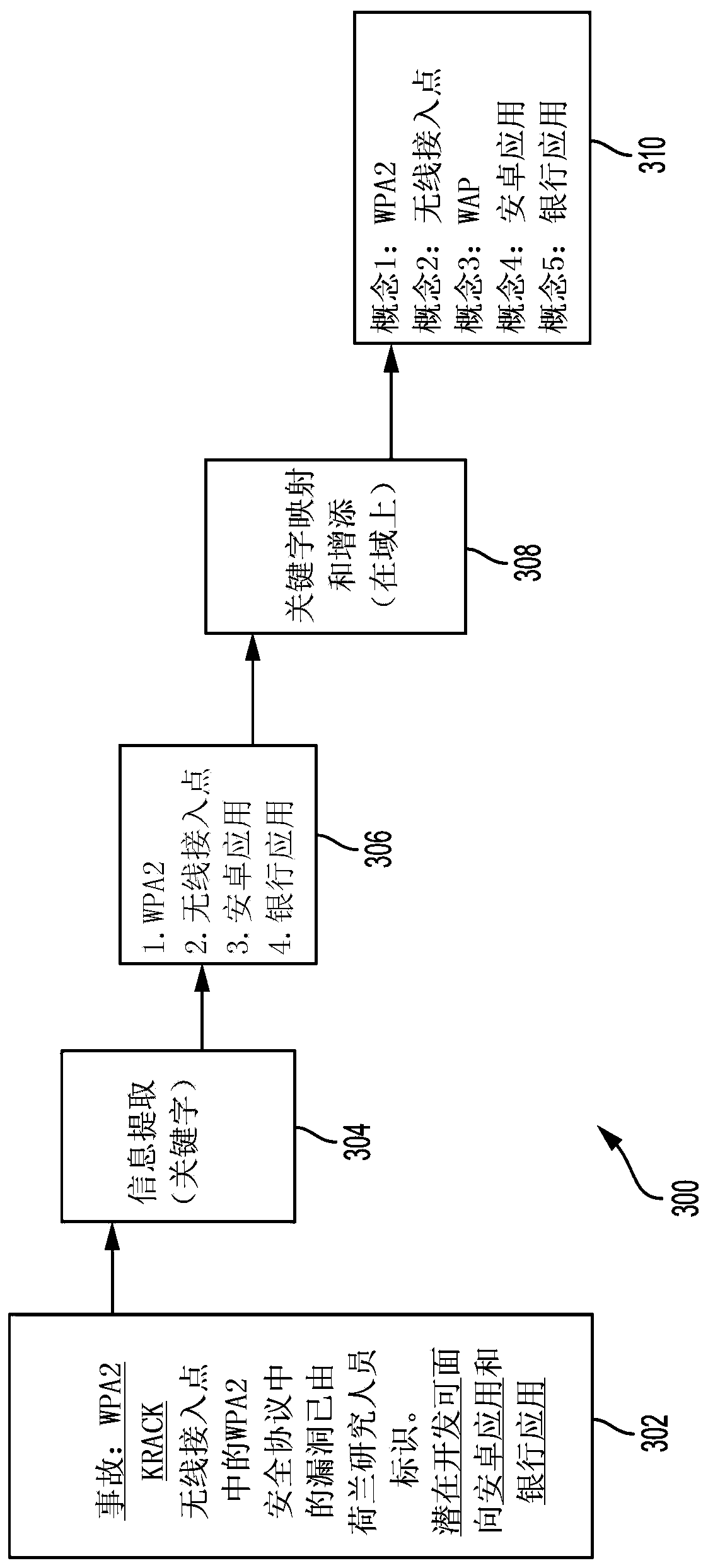
[0085] Clause 1: A computer-implemented method of proactive cyber defense of a plurality of networked assets, the method comprising the steps of: receiving a plurality of cyber incident reports; extracting keywords from the plurality of cyber incident reports; and applying shallow machine learning techniques to the identification of the plurality of networked assets to obtain an identification of a first subset of networked assets susceptible to at least a first threat scenario and an identification of the first threat scenario; applying deep machine learning techniques to the identification of a first subset of networked assets affected by a threat scenario, the identification of the first threat scenario, the keyword, and the identification of the plurality of networked assets vulnerable to at least a second threat scenario identification of a second subset of networked assets affected and identification of a second threat scenario; simulating the plurality of networked asset...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com