Transaction method and device
A transaction method and transaction request technology, applied in the field of data security, can solve problems such as the inability to adjust the security authentication method and the inability to guarantee transaction security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach 1
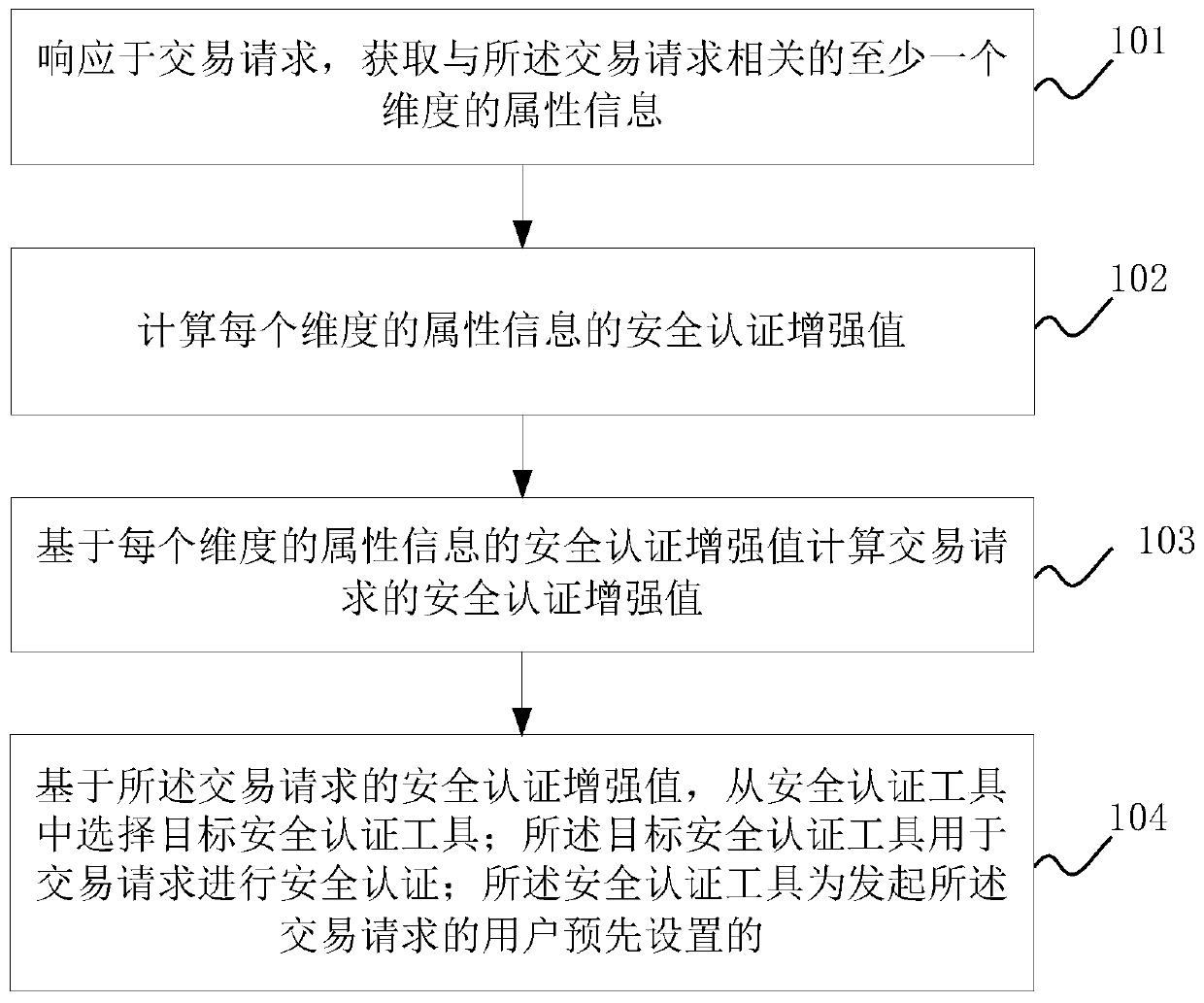
[0053] Embodiment 1: Add the enhanced security authentication values of the attribute information of each dimension to obtain the enhanced security authentication values of the transaction request.
[0054] For example: the enhanced security authentication value of the customer type is -2, the enhanced security authentication value of the transaction type is -3, the enhanced security authentication value of the transaction amount is -2, and the enhanced security authentication value of the transaction channel is -4, then the transaction request The enhanced value of the security authentication is: -2+(-3)+(-2)+(-4)=-11
Embodiment approach 2
[0055] Embodiment 2: Based on different weight values, the enhanced security authentication value of the attribute information of each dimension is added to obtain the enhanced security authentication value of the transaction request.
[0056] For example: the enhanced security authentication value of the customer type is -2, the enhanced security authentication value of the transaction type is -3, the enhanced security authentication value of the transaction amount is -2, the enhanced security authentication value of the transaction channel is -4, and the enhanced security authentication value of the customer type is -2. Weight, 0.1, the weight of the transaction type is 0.2, the weight of the transaction amount is 0.3, the security authentication weight of the transaction channel is 0.4, then the security authentication enhancement value of the transaction request is: (-2)*0.1+(-3)*0.2 +(-2)*0.3+(-4)*0.4=-3.
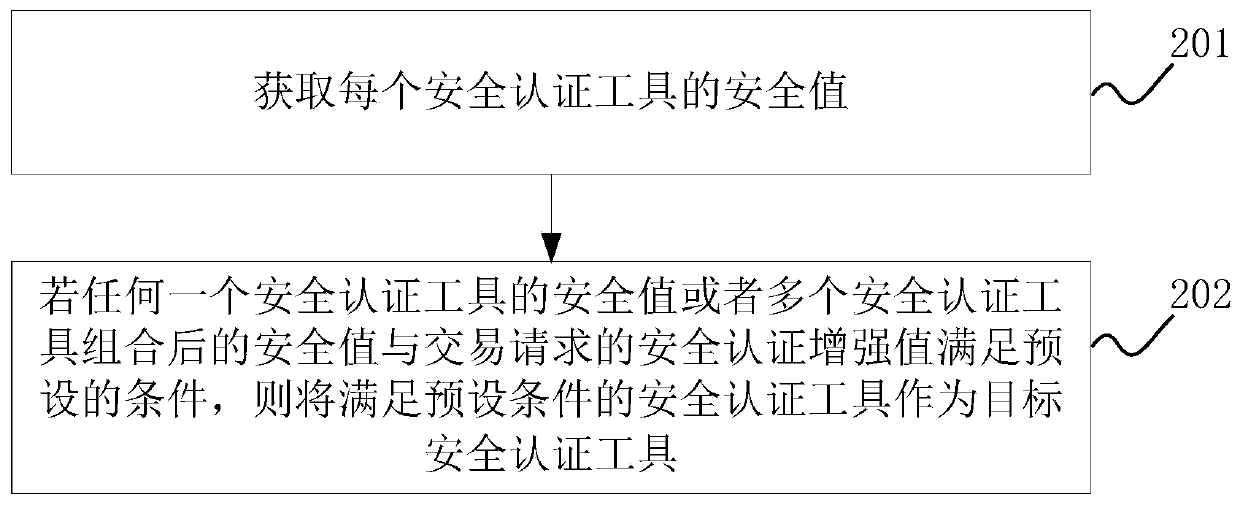
[0057] S104: Based on the security authentication enhancement val...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com