Advanced cybersecurity threat mitigation using behavioral and deep analytics
An advanced, network technology, applied in the field of network security and threat analysis, computer management, can solve the problems of inability to form predictive analysis data transformation, and the role of the network security field is small
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
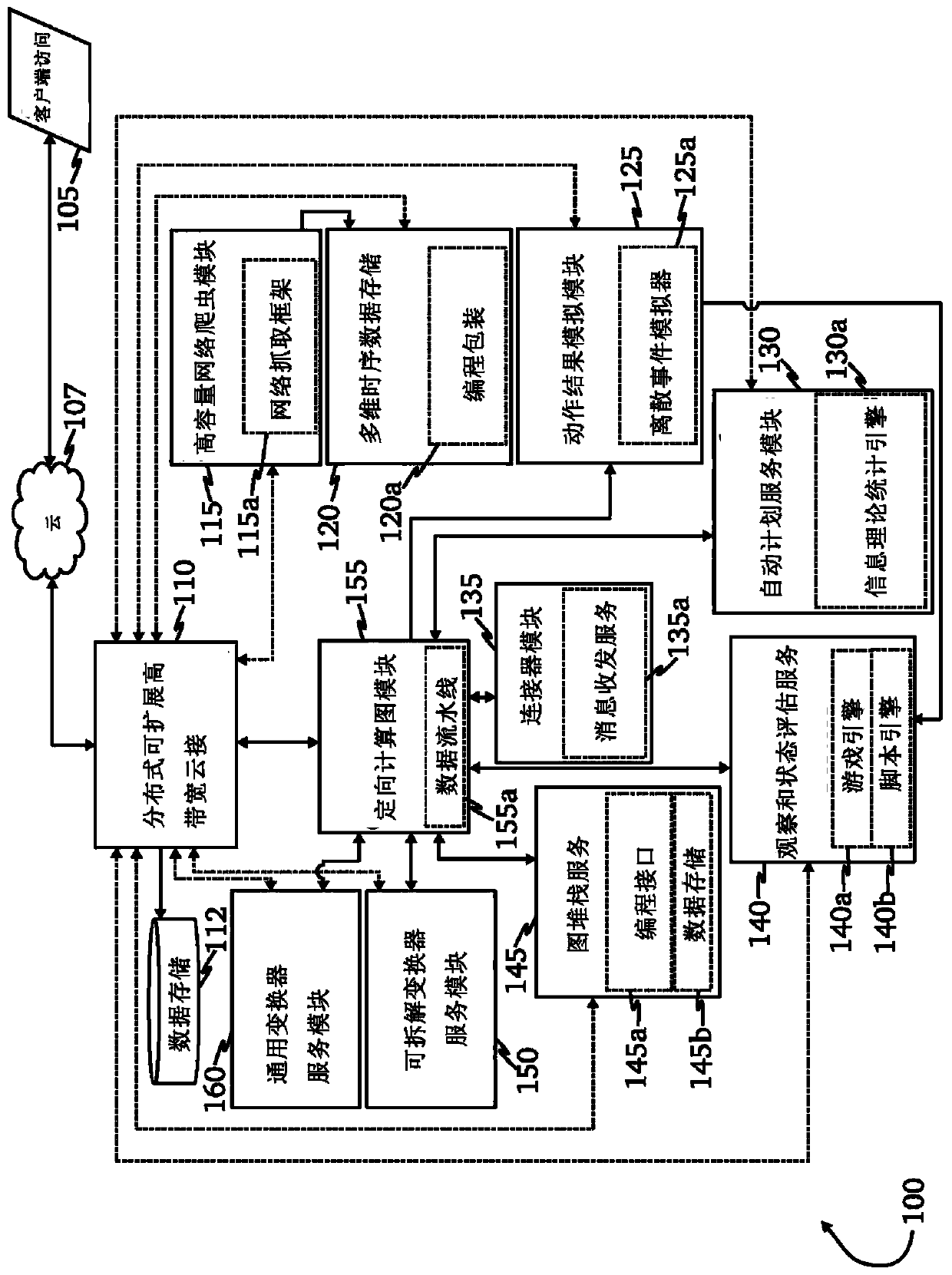
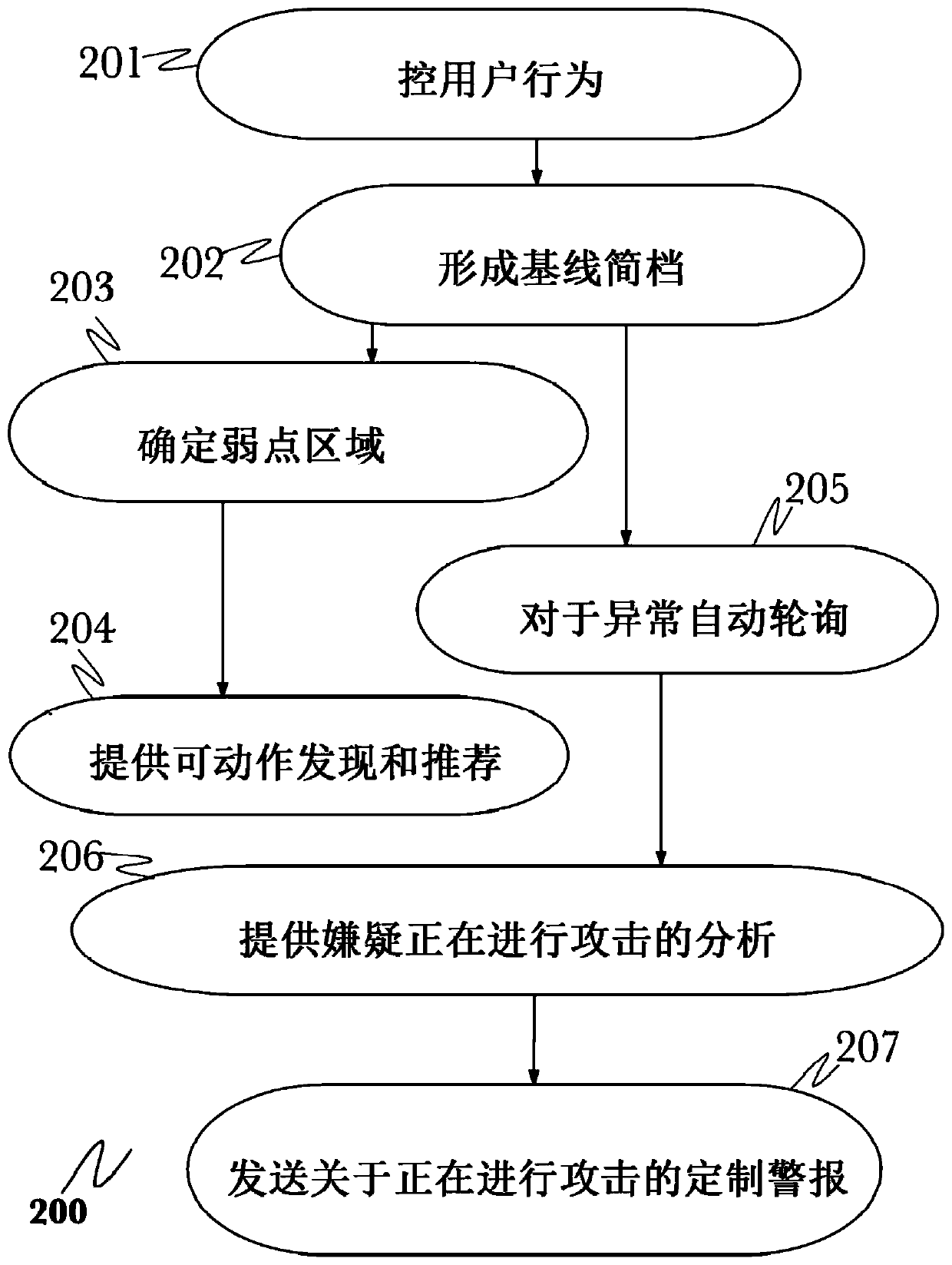
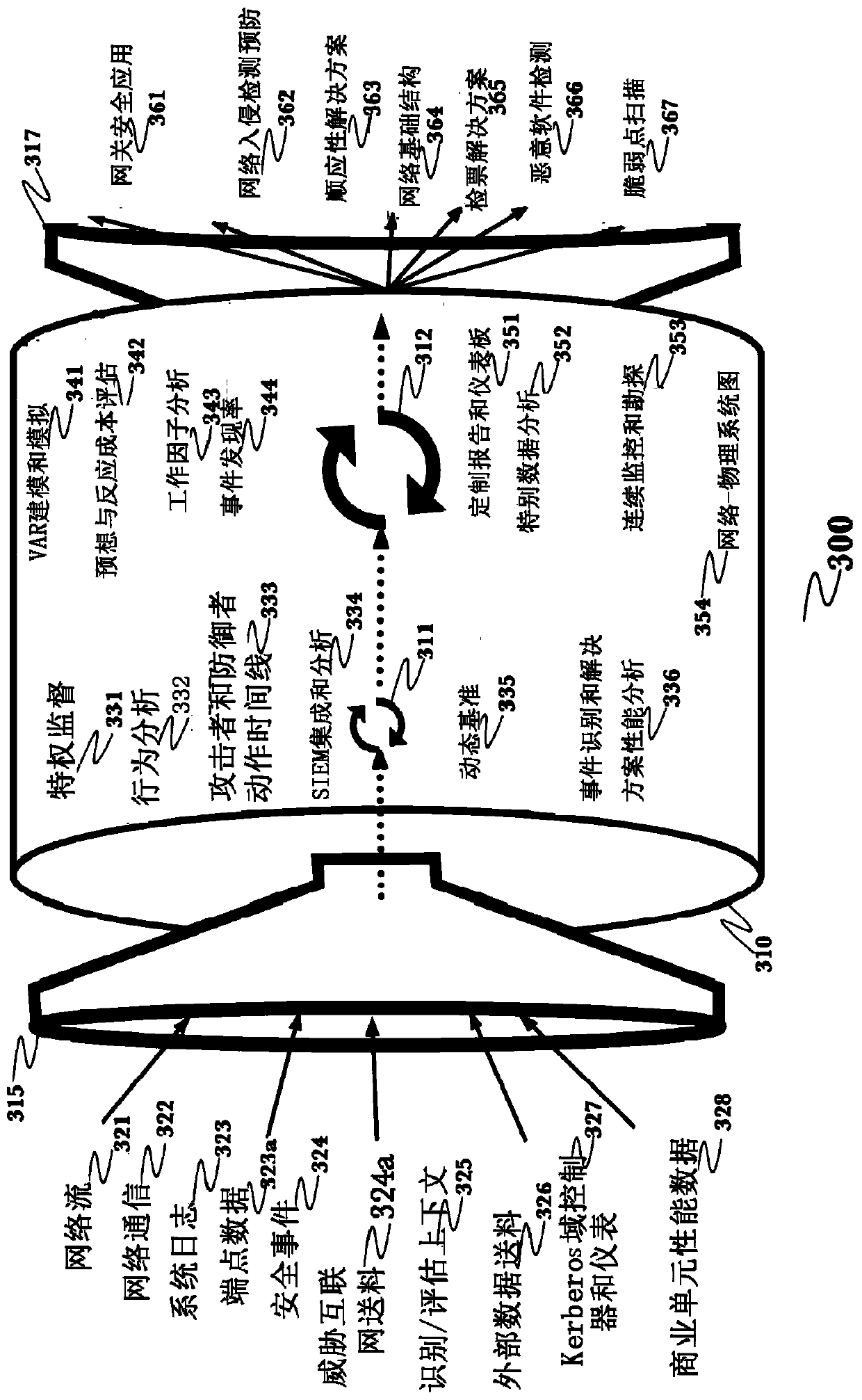
[0031] The inventors have envisioned and put into practice an advanced network security threat mitigation using behavioral and deep analytics.
[0032] One or more different feature aspects may be described in this application. Further, several alternative arrangements may be described for one or more of the feature aspects described herein; it should be understood that these are presented for illustrative purposes only and are not limiting in any way to the feature aspects contained herein or in terms of The claims shown here. One or more of the arrangements may apply broadly to several feature aspects, as is readily apparent from the description. Generally, arrangements are described in sufficient detail to enable one skilled in the art to practice one or more of the features, and it is understood that other arrangements may be utilized and structural, logical, software, electrical, and other changes may be made without departing from the specific features. range of aspect...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap