Network safety measure validity evaluation method, device and equipment and storage medium
A network security and effectiveness technology, applied in the field of network security, can solve problems such as enterprise losses, achieve the effect of solving effective evaluation, realizing effectiveness evaluation, and solving technical problems
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
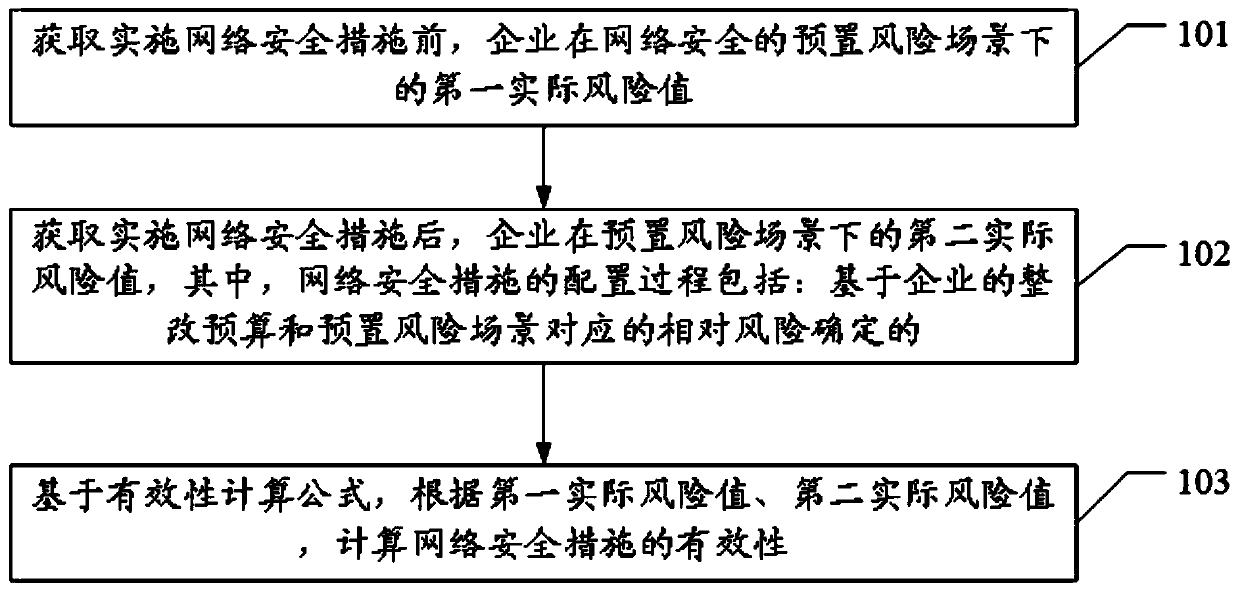
[0067] The above is the first embodiment of the method for evaluating the effectiveness of a network security measure provided by the embodiment of the present application. The following is the second embodiment of the method for evaluating the effectiveness of a network security measure provided by the embodiment of the present application. For details, please refer to figure 2 .
[0068] Such as figure 2 As shown, an embodiment of a method for evaluating the effectiveness of a network security measure in this embodiment specifically includes:
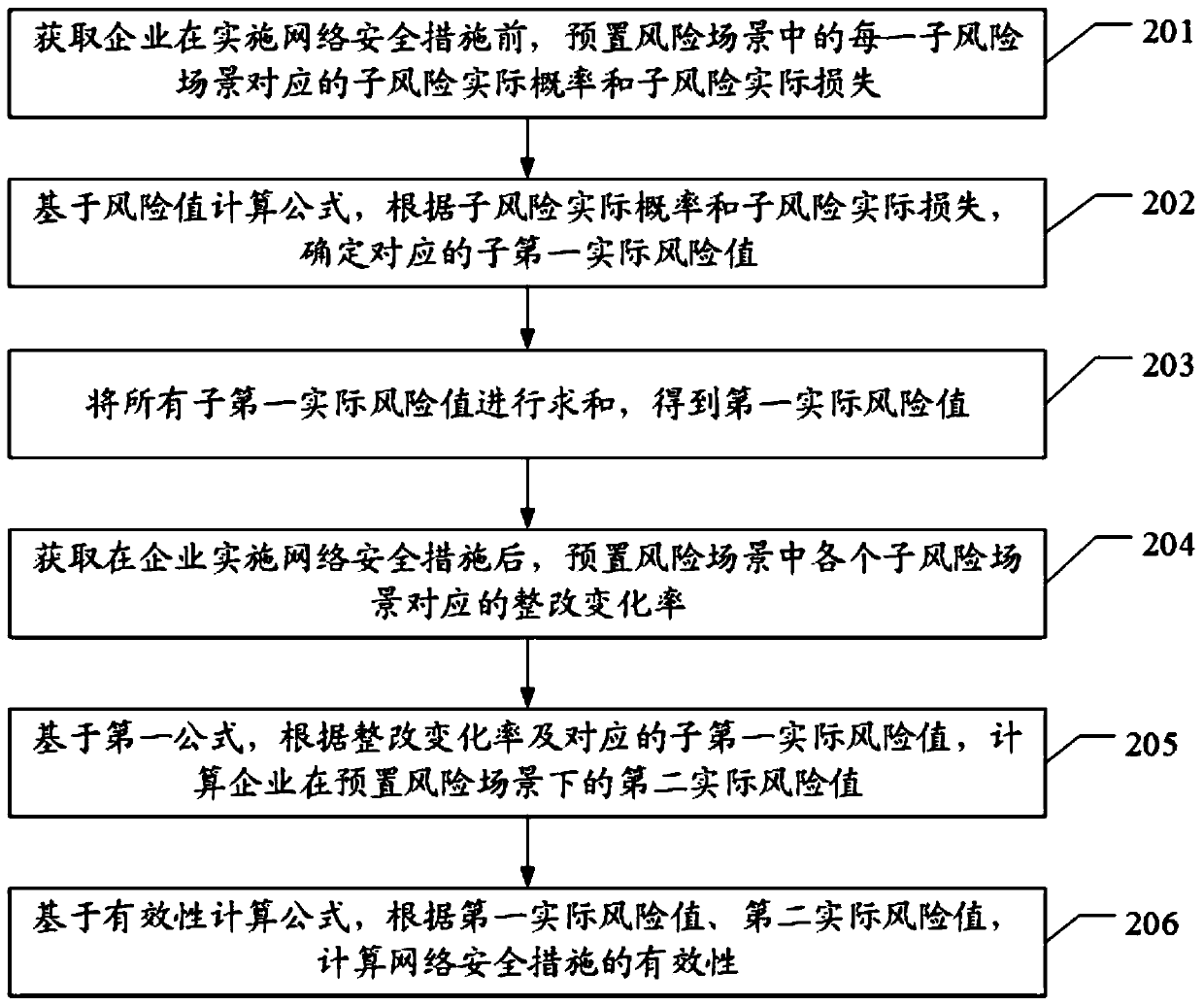
[0069] Step 201. Obtain the actual sub-risk probability and sub-risk actual loss corresponding to each sub-risk scenario in the preset risk scenario before the enterprise implements network security measures.
[0070] In this embodiment, before the enterprise implements network security measures, the first actual sub-risk value in the preset risk scenario is calculated by summing the sub-actual risk values corresponding to each s...
Embodiment 2
[0100] The above is the second embodiment of the method for evaluating the effectiveness of a network security measure provided by the embodiment of the present application, and the following is an application example of the device for evaluating the effectiveness of a network security measure provided by the embodiment of the present application.
[0101] Step S1, in this application example, quantify the sub-relative probabilities p of all sub-risk scenarios in the preset risk scenarios in combination with the company's own situation ri , sub-relative loss l ri and child relative risk value r ri , where i is the ith sub-risk scenario, and r represents relative;
[0102] Step S2. Calculate the sub-actual probability p of each sub-risk scenario of the enterprise gi , sub-actual loss l gi and sub-first actual risk r gi , and calculate the first actual risk value R through all sub-first actual risk values, the calculation formula is as follows:
[0103]
[0104] Among th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com