Anti-phishing method, client and system for communication content
A communication content and anti-phishing technology, applied in the field of network security, can solve problems such as weak security awareness and successful phishing, and achieve the effect of preventing phishing fraud and improving network security awareness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
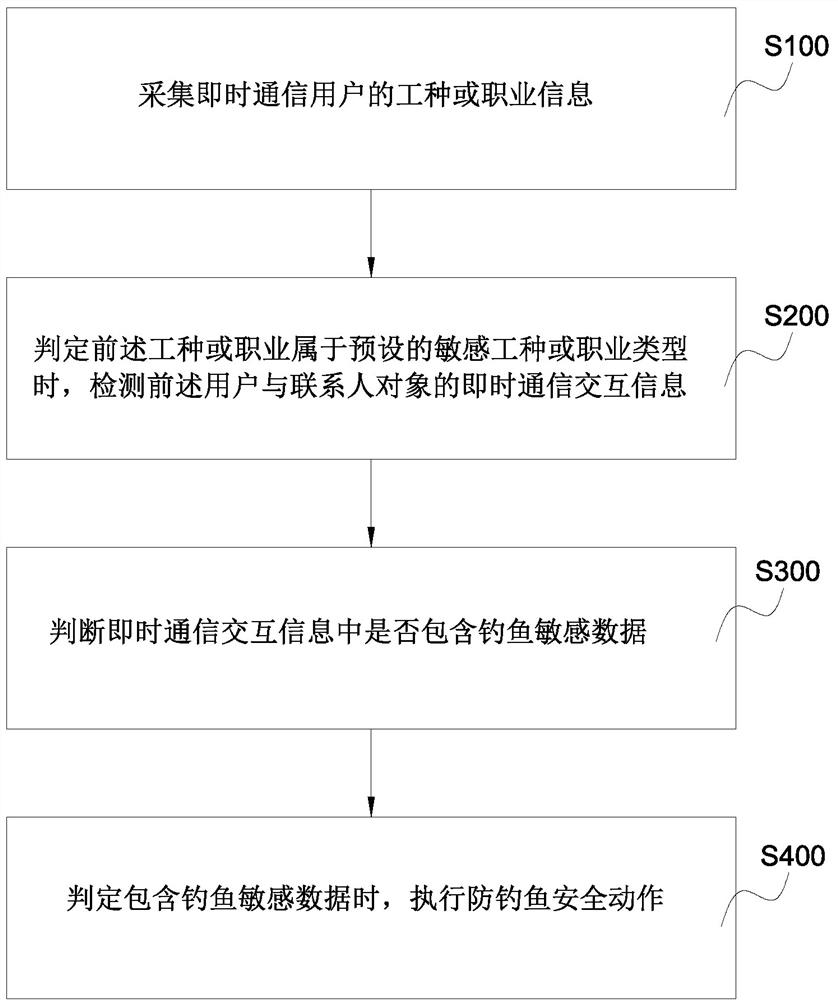
[0056] see figure 1 As shown, it is an anti-phishing method for communication content provided by an embodiment of the present invention. The method comprises the steps of:
[0057] S100. Collect job type or occupation information of instant messaging users.
[0058] The type of work or occupation information of the user can be set by the user or the system. Specifically, for example, the user can actively set his or her job type or occupation information based on the instant messaging tool.
[0059] The instant messaging tools, also known as instant messaging tools, generally refer to clients with instant messaging functions in this field, such as WeChat, QQ, and DingTalk. As an example and not a limitation, the instant messaging tool may be a network version application, a PC version application or a handheld terminal APP application. Optionally, a job type or occupation setting column is set in the instant messaging tool for the user to set related information.
[0060...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com