Power Internet of Things network security risk prediction method
A power Internet of Things and network security technology, applied to electrical components, transmission systems, etc., can solve problems such as poor long-term prediction results, and achieve the effect of facilitating mid- and long-term predictions and enriching the causal library
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0033] The present invention will be further described below in conjunction with the accompanying drawings. Embodiments of the present invention include, but are not limited to, the following examples.
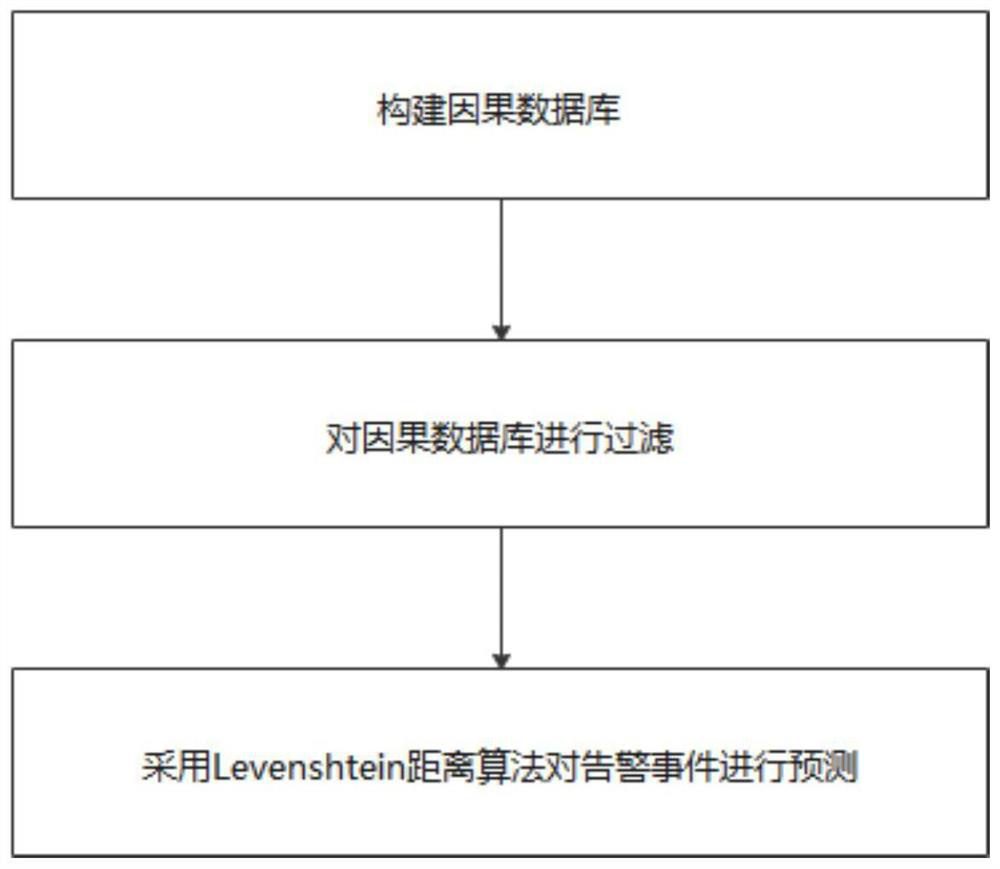
[0034] like figure 1 The shown power Internet of Things network security risk prediction method includes an acquisition module, a filter module, a prediction module and a display module, and includes the following steps:
[0035] Step 1. Build a causal database.
[0036] Among them, a single alarm event in the power Internet of Things specifically includes the attack source IP, attack behavior, attack IP, start time and end time, and the attack source IP, attack behavior, and attack IP in a single alarm event are regarded as a valid alarm information.
[0037] In addition, all alarm information is obtained through the acquisition module, and a causal database is constructed for each alarm information. Advance forward, take the six alarm events that are closest to the start ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com