Attack detection method and device, equipment and storage medium
A technology of attack detection and attack messages, applied in the network field, can solve problems such as abnormal computer processing, computer blue screen of death, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach 1
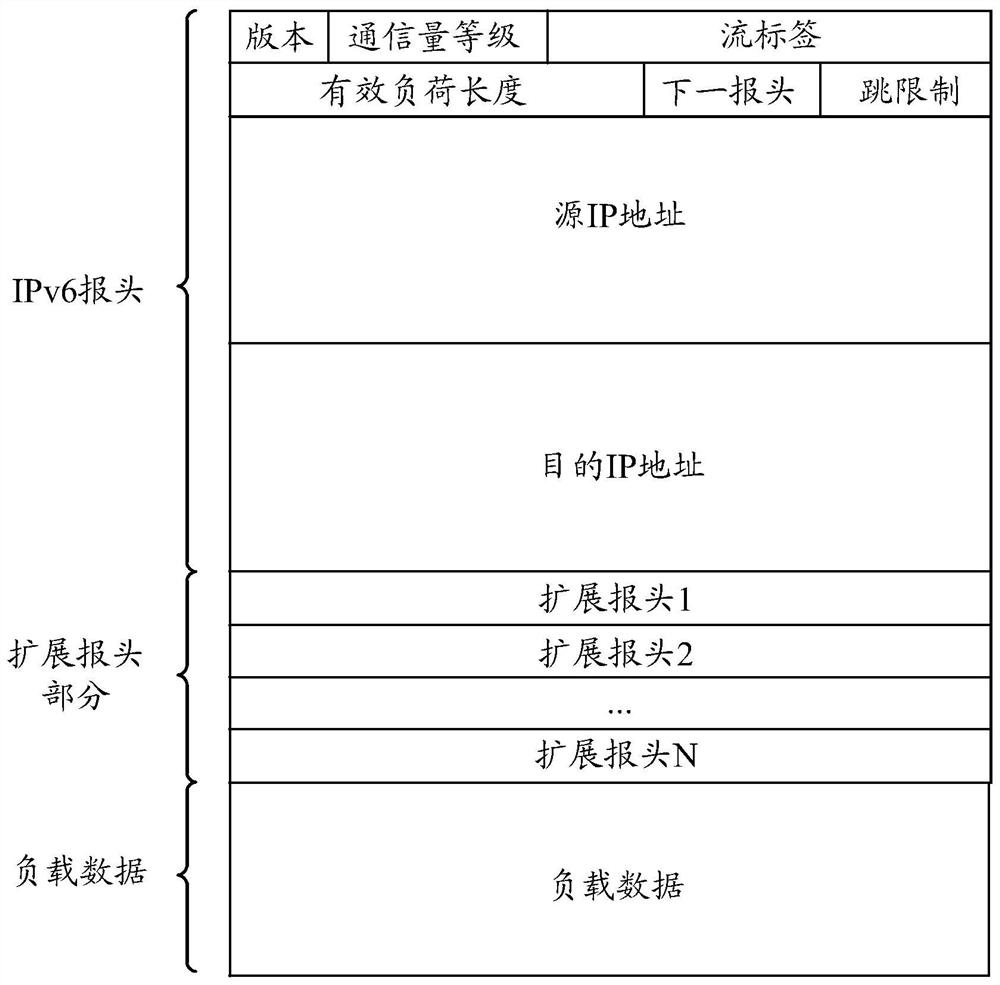
[0092] Embodiment 1. If the fragmentation end flag in the second header of a fragmented message is 1, and the number of bytes corresponding to a fragmented message is less than the maximum transmission unit of the first link, discard the fragmented message .
[0093] Specifically, the first link maximum transmission unit is the lower limit value of the link maximum transmission unit. Different links correspond to different link maximum transmission units. Each link MTU corresponds to an upper limit and a lower limit.
[0094] For example, in Ethernet, the upper limit value of the link maximum transmission unit is 1500 bytes, and the lower limit value of the link maximum transmission unit is 1280 bytes.
[0095] In each fragmented message, except for the last fragmented message, the number of bytes corresponding to each fragmented message is greater than or equal to the lower limit of the maximum transmission unit of the link, and less than or equal to the upper limit of the ...
Embodiment approach 2
[0098] Embodiment 2, if the fragmentation end flag in the second header of a fragmented message is 1, and the number of bytes corresponding to a fragmented message is not an integer multiple of 8, or the number of bytes corresponding to a fragmented message If the difference between the number of sections and the maximum transmission unit of the second link is greater than 4 bytes, the fragmented message is discarded.
[0099] Specifically, the second link maximum transmission unit is an upper limit value of the link maximum transmission unit. When a fragmented message is not the last fragmented message, the number of bytes corresponding to the fragmented message is an integer multiple of 8, and at the same time, the number of bytes corresponding to the fragmented message is close to the maximum transmission unit of the link upper limit value.
[0100] For example, in Ethernet, the upper limit of the maximum transmission unit of a link is 1500 bytes. For a normal fragmented m...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com