Defense method, device and system based on existing threats in target node
A technology of target nodes and nodes, which is applied in the field of network security and can solve the problems of waste of network resources and defense costs.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
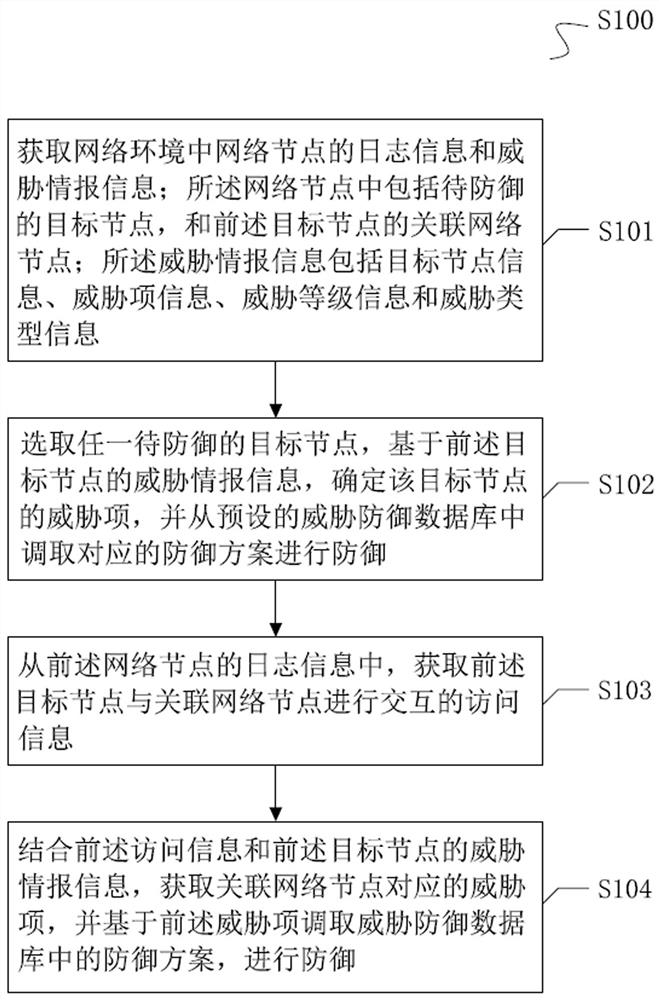
[0046] see figure 1 Shown is a flowchart provided by the present invention. The implementation step S100 of the method is as follows:
[0047] S101. Obtain log information and threat intelligence information of network nodes in the network environment; the network nodes include target nodes to be defended, and associated network nodes of the aforementioned target nodes; the threat intelligence information includes target node information, threat item information , threat level information, and threat type information.
[0048] The network node refers to a terminal in a network environment with an independent network address and data processing functions, and the data processing functions include but not limited to the functions of transmitting data, receiving data and / or analyzing data.
[0049] The network nodes may be workstations, clients, network users, or personal computers, as well as servers, printers, and other network-connected devices.
[0050] It should be noted ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com