Avoiding exposed node problems in wireless local area networks
A wireless local area network and hidden terminal technology, which is applied in the field of avoiding hidden terminals in wireless local area networks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
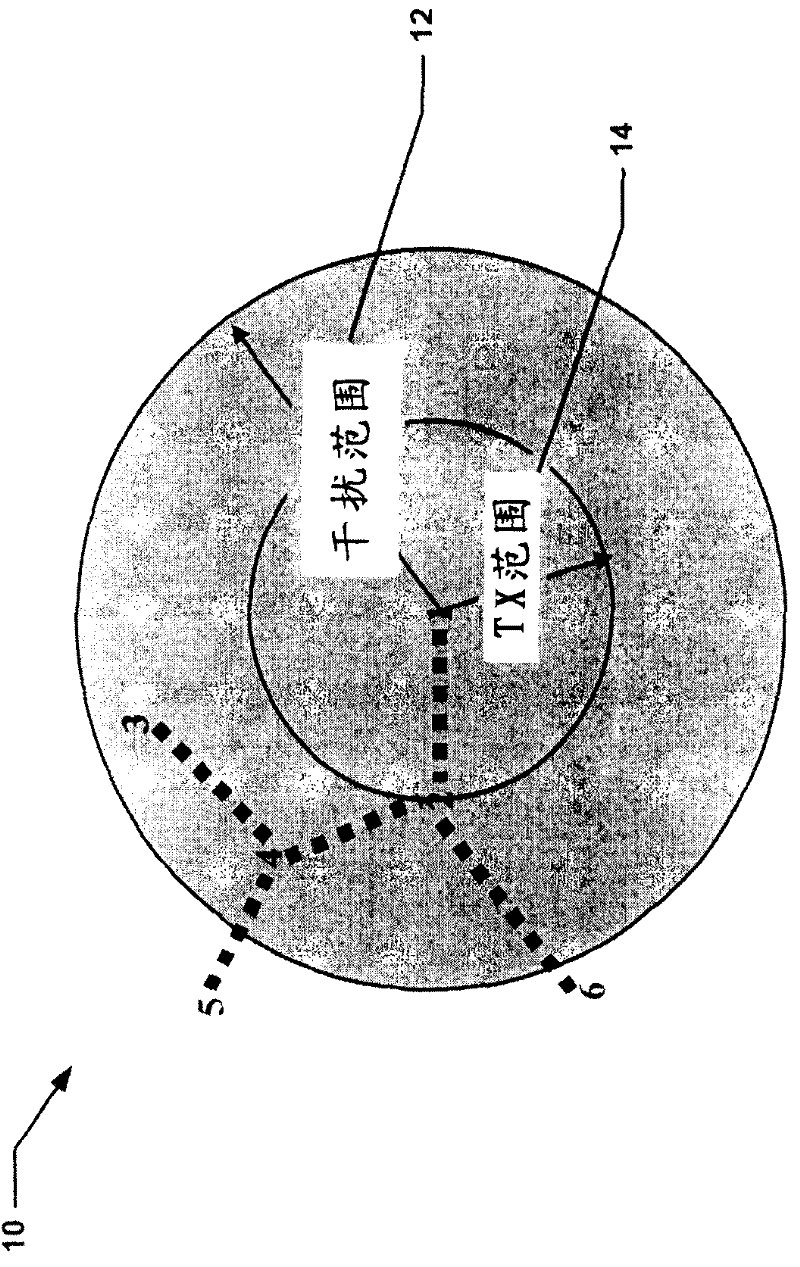
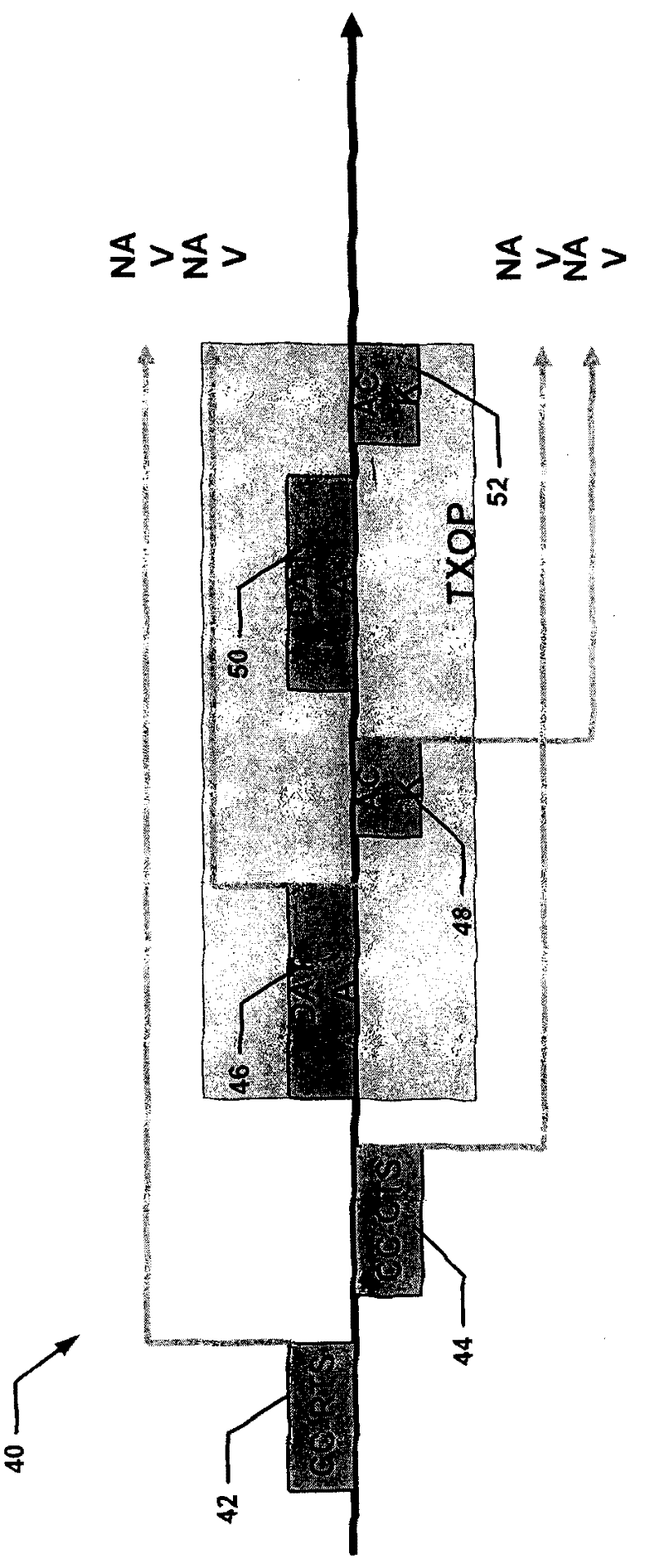
[0027] A wireless LAN network may use a common control protocol (CCC). The CCC protocol is a MAC protocol that extends the IEEE802.11 distributed MAC protocol so that multiple channels can be used in a BSS or mesh network. The CCC protocol defines a flexible channel access structure based on distributed priority contention-based media access. The CCC protocol distinguishes two logical channel functions: Control Channel (CC) and Data Channel (DC). In the following description, a station or network point observing the CCC MAC protocol is called a "node". Nodes exchange control and management frames on the control channel. The data channel carries data services.
[0028] Reservations for transmission on the various data channels are made by exchanging control frames on the control channels. As an extension of the traditional RTS and CTS messages, CC-RTS and CC-CTS are used to reserve the data channel for the time taken to transmit a transmission opportunity (TXOP). As specifie...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com