Method, apparatus and system for selecting a serving network
A technology for service network and selection conditions, applied in the field of network communication, can solve the problem that DHCP clients cannot actively select service network, etc., and achieve the effect of improving service ability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
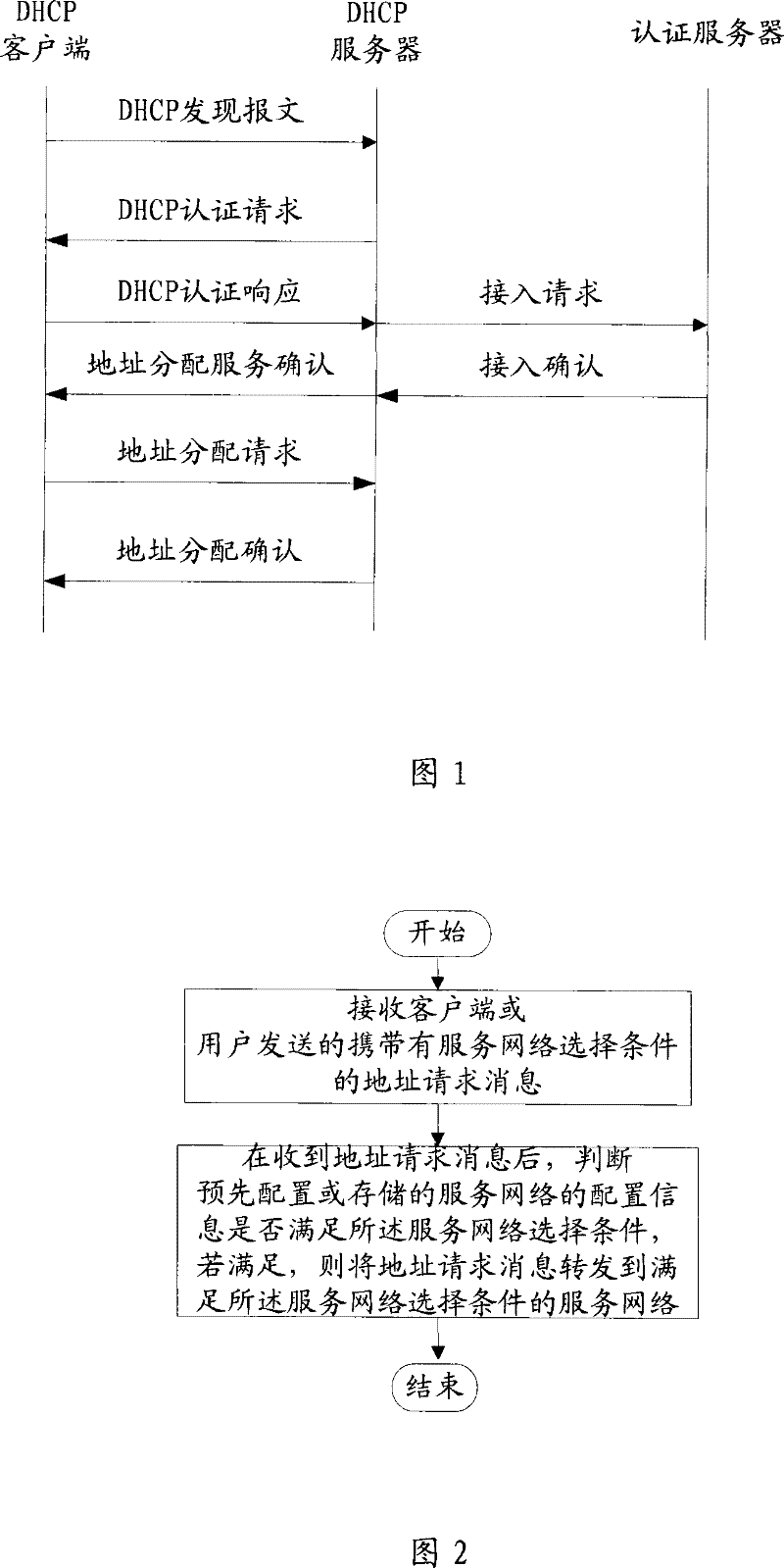
[0088] Such as Figure 4 As shown, in this embodiment, the client or user connects to multiple authenticators / agents through the access aggregation network, and each authenticator / agent is connected to the service network to which it belongs through its own IP network, that is, the operator network SP . Wherein, the clients or users may be various wired and wireless terminals, and have a DHCP client or user function. The authenticator / agent can have a DHCP relay agent function (DHCP Proxy or DHCP Relay), and can also have an authenticator (Authenticator) / AAA client or user function, and configuration information of the operator network to which it belongs is configured. The configuration information of the service network in each authenticator / proxy can be configured dynamically or statically. If dynamic configuration is adopted, the DIAMETER protocol or other protocols can be used, and the operator's policy server or other control equipment can dynamically configure the aut...
Embodiment 2
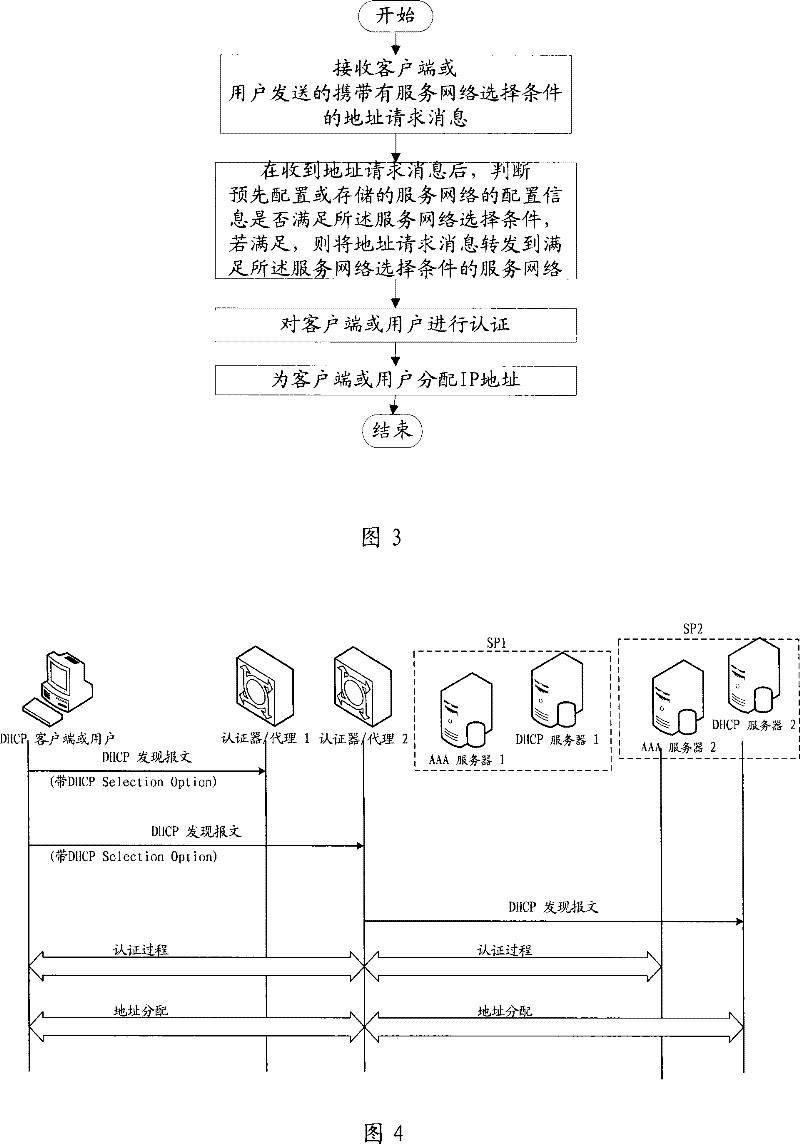
[0116] In this example, if Figure 5 As shown, a DHCP client or user is connected to an authenticator / agent through an access aggregation network, and multiple operator network SPs share an authenticator / agent. Authenticator / Proxy is connected to multiple operator network SPs through IP network. The DHCP client or user can be various wired and wireless terminals, and has the function of DHCP client or user. The authenticator / agent has the function of DHCP relay agent (DHCP Proxy or DHCP Relay), and can also have the function of authenticator (Authenticator) / AAA client or user, and is configured with the configuration information of each operator network connected to it, such as NAI, capabilities and other information. Likewise, network identification parameters in each authenticator / proxy can be configured dynamically or statically. The configuration method is the same as that described in Embodiment 1.
[0117] The operator's networks SP1 and SP2 respectively include an A...
Embodiment 3
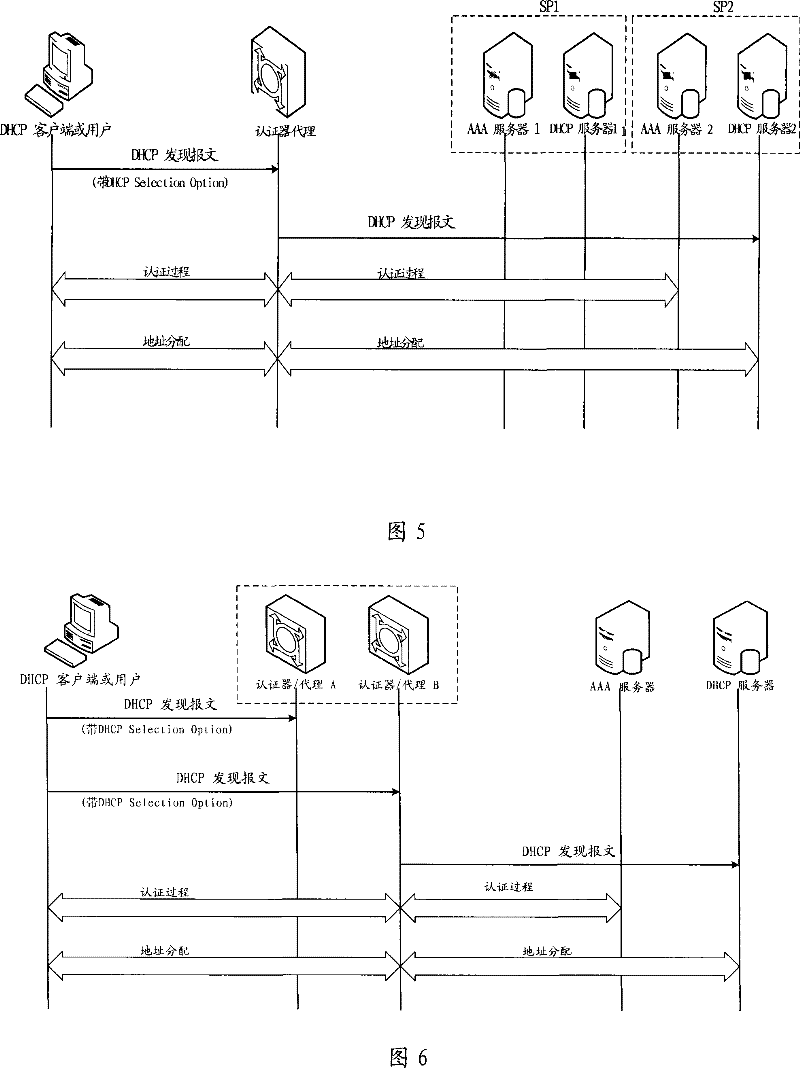
[0127] In Embodiments 1 and 2, the authenticator / proxy may actually consist of multiple sub-authenticator / proxy devices. Such as Figure 6 As shown, authenticator / proxy 1 is composed of sub-authenticator / proxy A and sub-authenticator / proxy B.
[0128] When sub-authenticator / agent A and sub-authenticator / agent B are both valid, or in the case of load sharing or master-standby relationship, when the authenticator / agent receives a DHCPDiscover message with a DHCP Selection Option message, except As described in Embodiment 1 or 2, the authenticator / agent can judge and select the operator network according to the parameters in the DHCPSelection Option, and the authenticator / agent can also further according to its own current load and network resources. Status, traffic sharing policy, client or user sharing policy, etc. determine which sub-authenticator / proxy will forward the packet and process subsequent client or user data. At the same time, the sub-authenticators / agents can mak...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com