Wireless metropolitan area network (MAN) safe access method
A wireless metropolitan area network and secure access technology, applied in the field of wireless communication systems, can solve the problems of not providing SS authentication, not being able to realize large-scale deployment of WMAN-SA, not fully explaining the specific methods of WMAN-SA, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
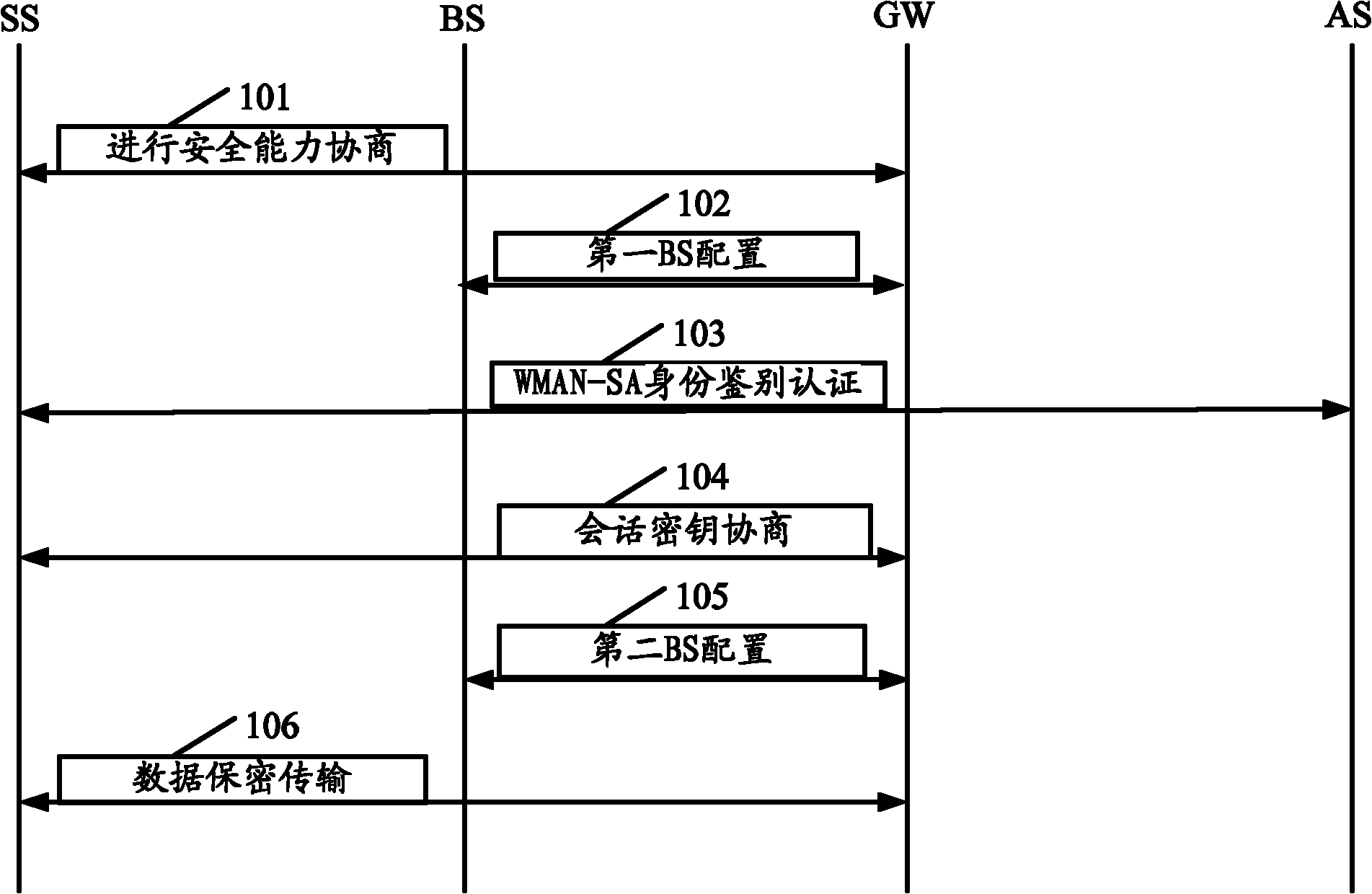
[0019] The current typical wireless metropolitan area network technology is based on the IEEE802.16 standard. The present invention will be described by taking IEEE802.16 as an example. The modules involved in the present invention include: SS (SubscriberStation, subscriber station), BS (Base Station, base station), GW (Gateway, gateway), AS (Authentication Server, authentication server). The present invention relates to security capability negotiation, BS configuration, authentication The steps of authentication, key negotiation and confidential transmission of business data are classified into two processes: management control process and confidential transmission process;
[0020] For convenience, refer to figure 1 , the management control process includes steps 101 to 105; the details are as follows:
[0021] 101. Conduct security capability negotiation;
[0022] The GW and the SS perform security capability negotiation; first, the SS forwards a security capability nego...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com