Security network authentication system and method
A network authentication and security technology, applied in the field of secure network authentication system, to achieve the effect of reliable authentication method
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
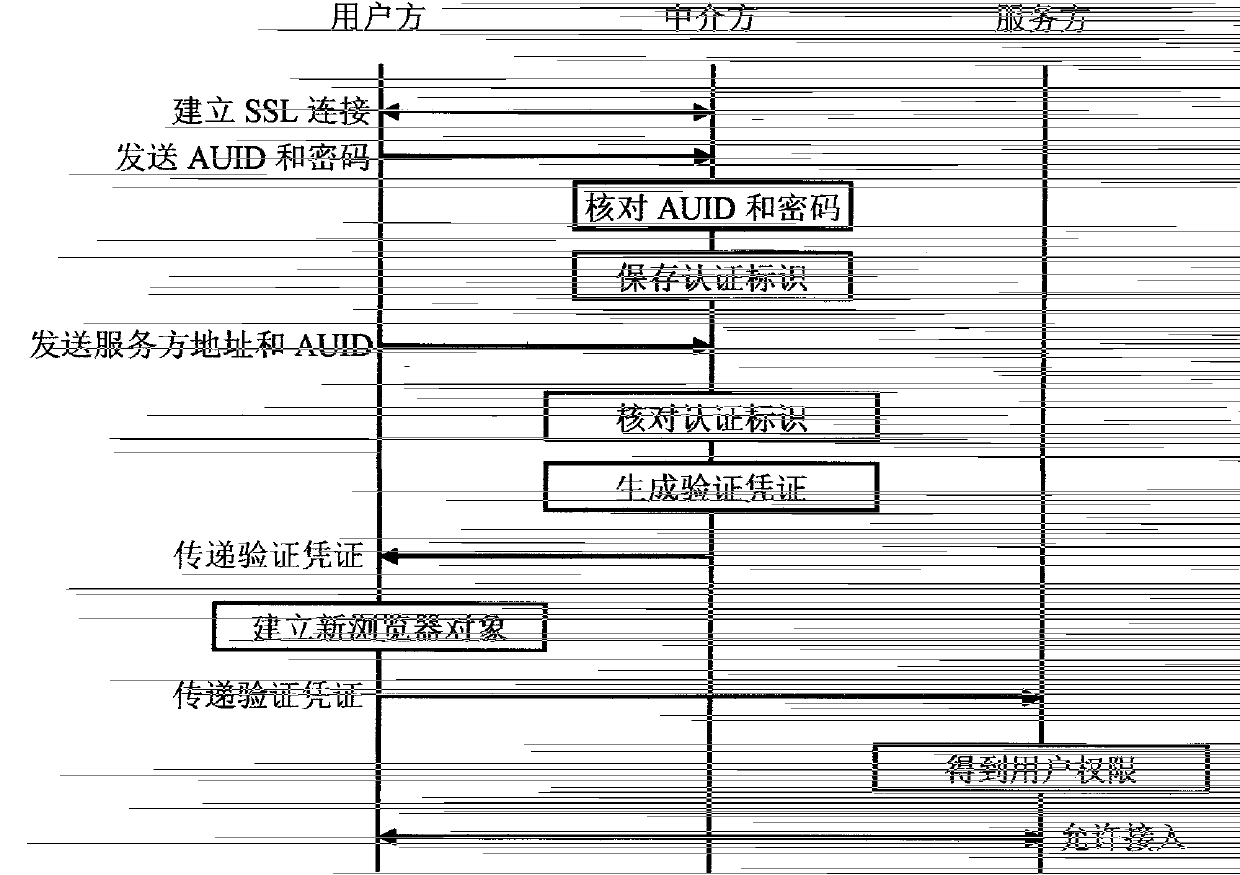
[0057] In this embodiment, the intermediary party has a digital certificate issued by an authoritative organization, and the service party can use the digital certificate to verify the digital signature of the intermediary party. A dedicated program downloaded from the other party.
[0058]The specific steps of this embodiment are: the user runs the authentication program on the terminal, the authentication program automatically establishes an SSL connection with the intermediary, the user enters the AUID and password in the authentication program to log in, and the authentication program sends the user's AUID to the intermediary and password, the intermediary checks the user name and password, if they are correct, proceed to the following steps; otherwise, the intermediary saves the user's AUID, the SSL ID and the current system time correspondingly (the DES of the SSL stored by the user) The key is the authentication ID), when the user needs to access a resource of a server,...
Embodiment 2
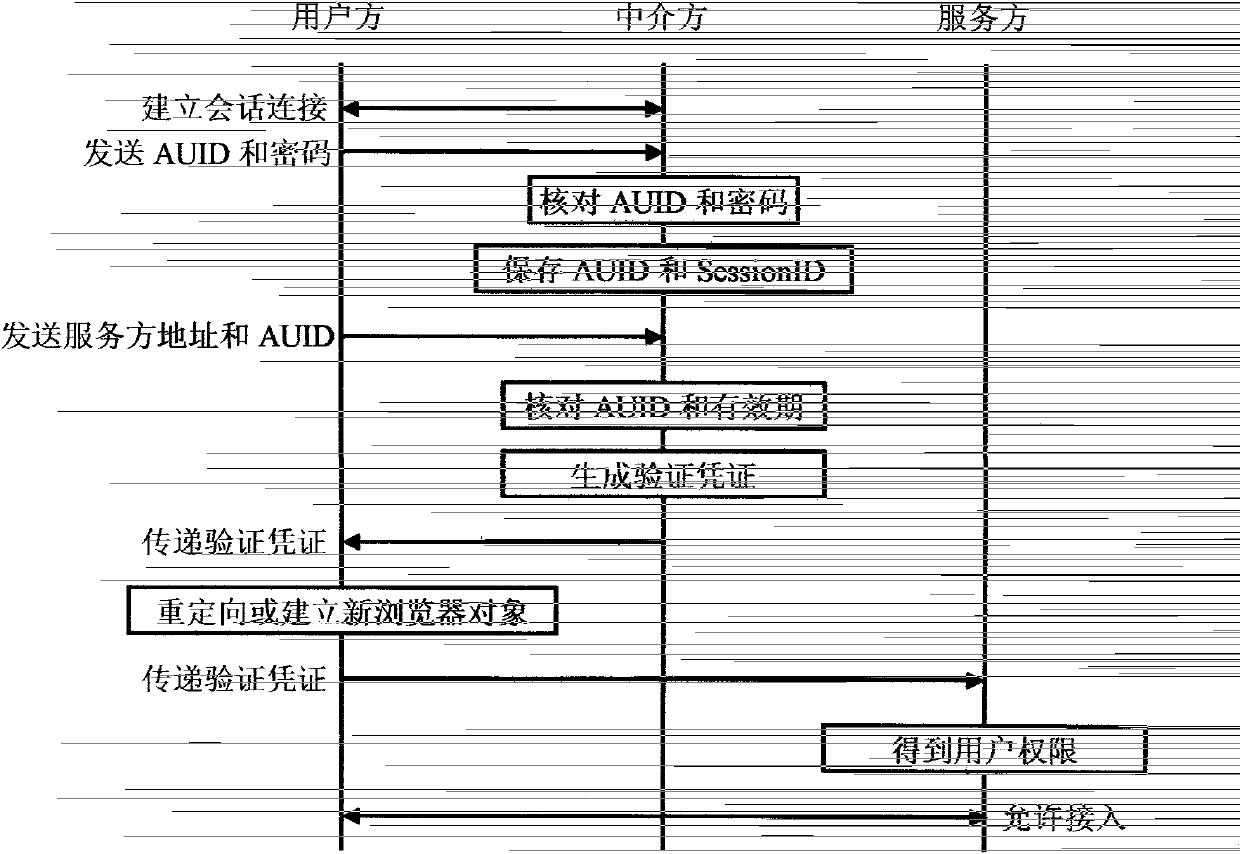
[0061] In this embodiment, the intermediary party has a digital certificate issued by an authority, and the service party can use the digital certificate to verify the digital signature of the intermediary party. The user side is authenticated by the intermediary party in the form of user name and login password. The authentication program is a browser.
[0062] The specific steps of this embodiment are: the user runs a browser object on the terminal and inputs the address of the intermediary (the browser object is used as an authentication program), and the intermediary establishes a session based on an SSL connection with the browser, wherein the intermediary generates A 1024-bit random sequence is used as the SessionID of the session established with the user's browser. The user enters the AUID and password on the interface launched by the intermediary to log in. The intermediary checks the AUID and password. If they are correct, proceed to the following steps; otherwise, sto...
Embodiment 3
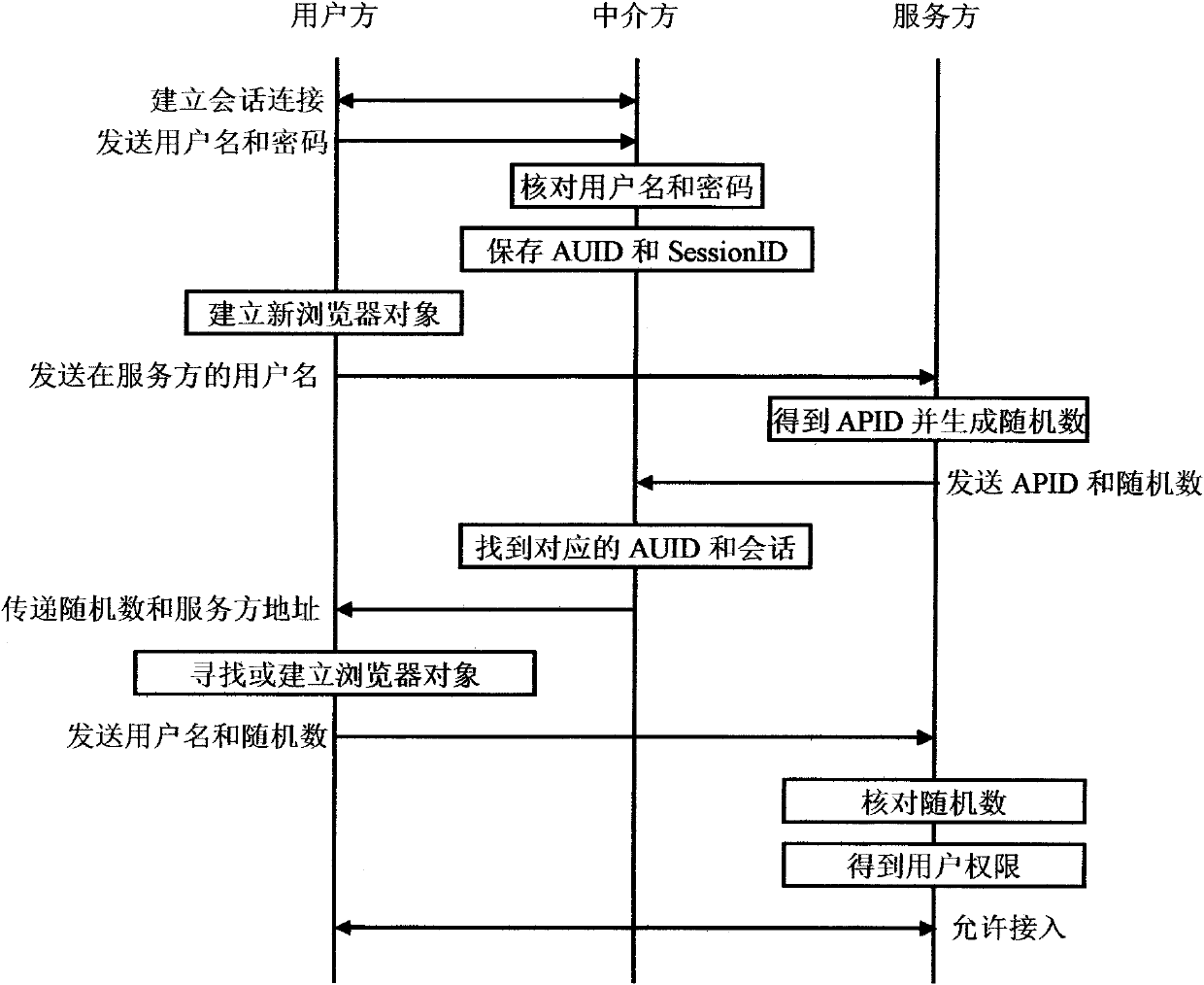
[0064] In this embodiment, the service party knows the fixed IP address of the intermediary in advance, and the user is authenticated by the intermediary with a user name and a login password. The authentication program is a special program downloaded by the user from the intermediary.
[0065] The specific steps of this embodiment are: the user runs the authentication program on the terminal, the authentication program establishes a session with the intermediary and the SessionID is a 1024-bit random sequence generated by the intermediary, the user enters the user name and password in the authentication program to log in, the The authentication program sends the user's user name and password to the intermediary. The intermediary checks the user name and password. If it is correct, proceed to the following steps; The AUID of the user, the SessionID of the session established by the user authentication program, and the current system time are saved correspondingly. When the user...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com