Intelligent information equipment and operation system thereof
A technology for operating systems and information equipment, applied in the protection of internal/peripheral computer components, instruments, digital data authentication, etc., to achieve the effect of improving security flexibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
[0043] This implementation provides an operating system suitable for intelligent information devices. The operating system can be an improvement on operating systems such as the Windows operating system or the Linux operating system. In other words, the operating system can be a Windows operating system , can also be an operating system such as Linux.
[0044] In addition to processing such as file management and user interface of the existing operating system (for example), the operating system of this embodiment also performs the following access operations for the mountable device to be accessed.
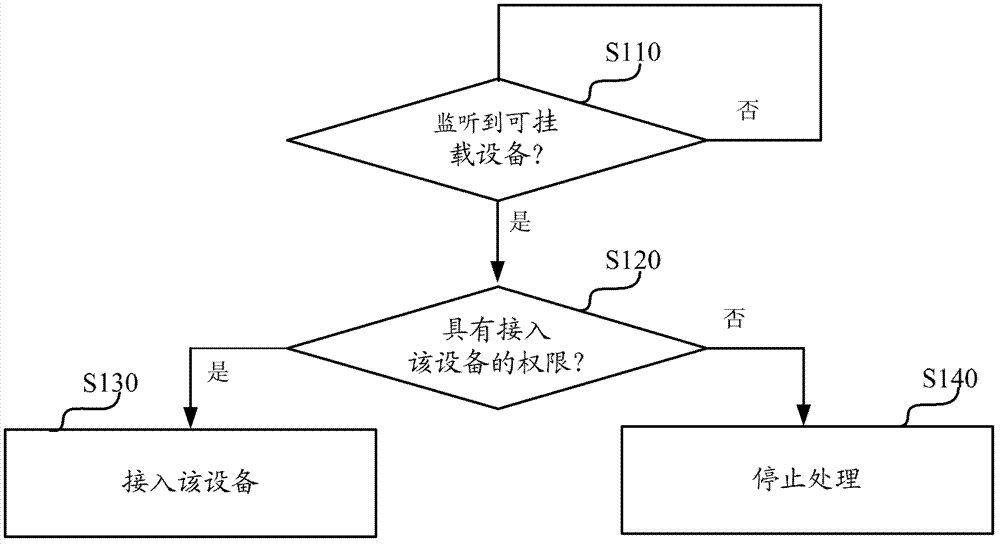
[0045] Step S110, monitor the mountable devices to be connected, such as USB flash drives, CDs, cameras, and printers (to be connected), and enter step S120 when the mountable devices to be connected are detected.
[0046] Step S120, based on the preset configuration information, it is judged whether the current user has the right to access the mountable device to be accessed.
...
no. 2 example
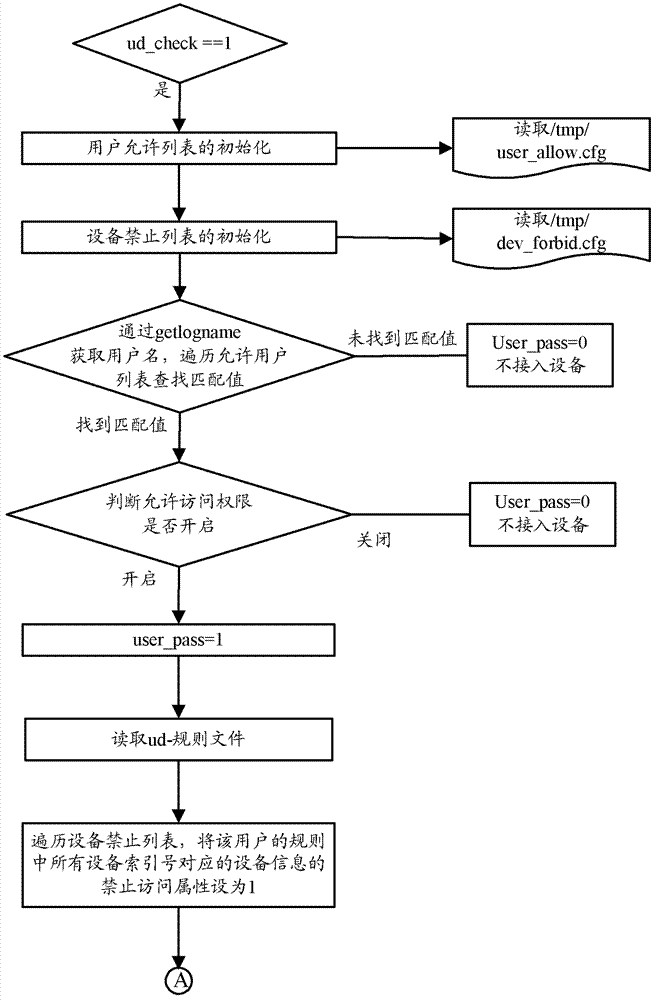
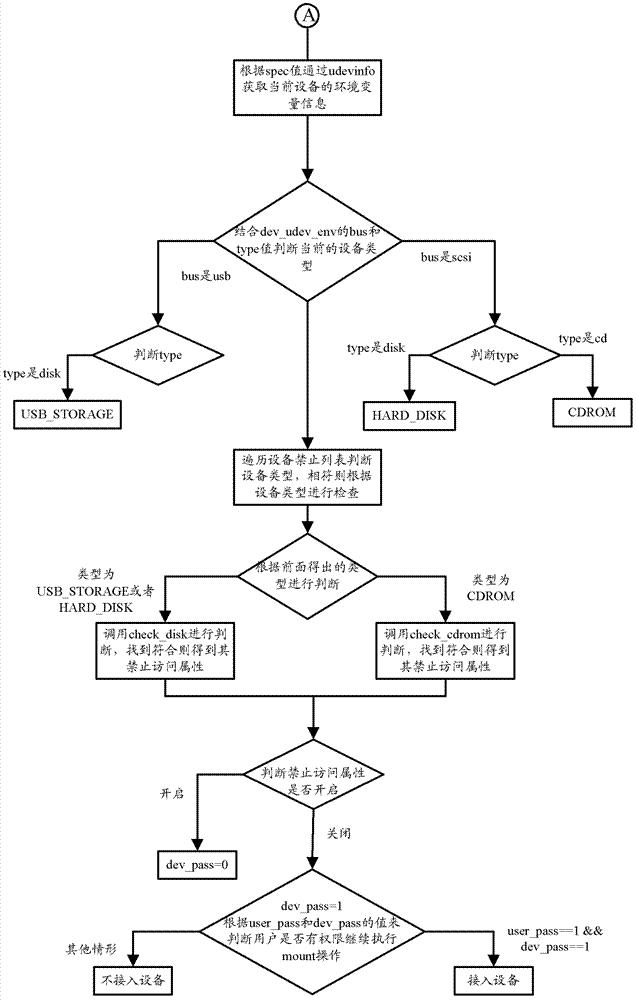
[0057] Figure 2a and Figure 2b Together, it shows a schematic flow chart of implementing the processing (hereinafter referred to as ud authentication processing) performed by the operating system when accessing a mountable device according to the second embodiment of the present invention by modifying the mount command. This embodiment will be described in detail below in conjunction with the figures.
[0058] Udev sends the information to HAL after listening to the uevent event of the device. HAL will start a hald and hald-runner service program to monitor the DBus connection information. Finally, the corresponding addon program will be called according to the specific device.
[0059] In this embodiment, the ud authentication mechanism according to this embodiment is realized by modifying the mount command through FIG. 2 . The main process is to first judge whether to perform ud authentication, and if so, initialize the user permission list and perform user authenticat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com