Information divulgement prevention method based on credible program
A program and trusted technology, applied in the field of information leakage prevention based on trusted programs, can solve data leakage and other problems
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0014] The present invention will be described in detail below in conjunction with the accompanying drawings. As a part of this specification, the principle of the present invention will be described through embodiments. Other aspects, features and advantages of the present invention will become clear at a glance through the detailed description.
[0015] Such as figure 1 , 2 As shown, a method for preventing information leakage based on a trusted program, wherein the method steps include:
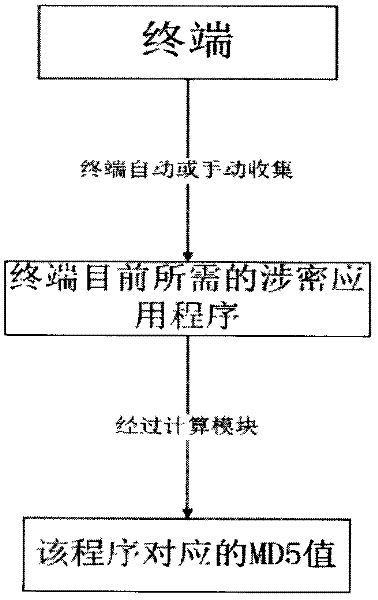
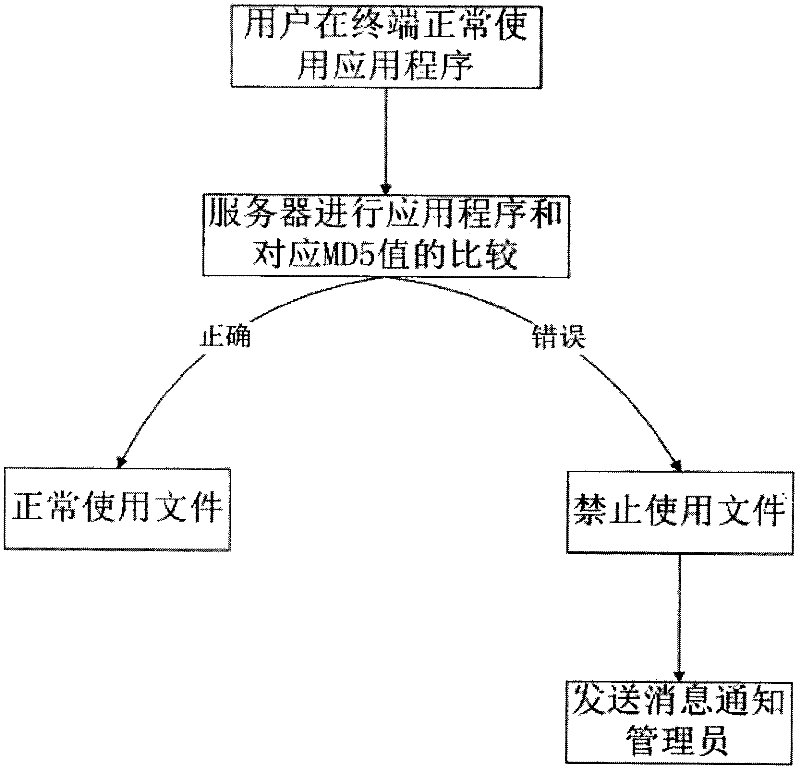
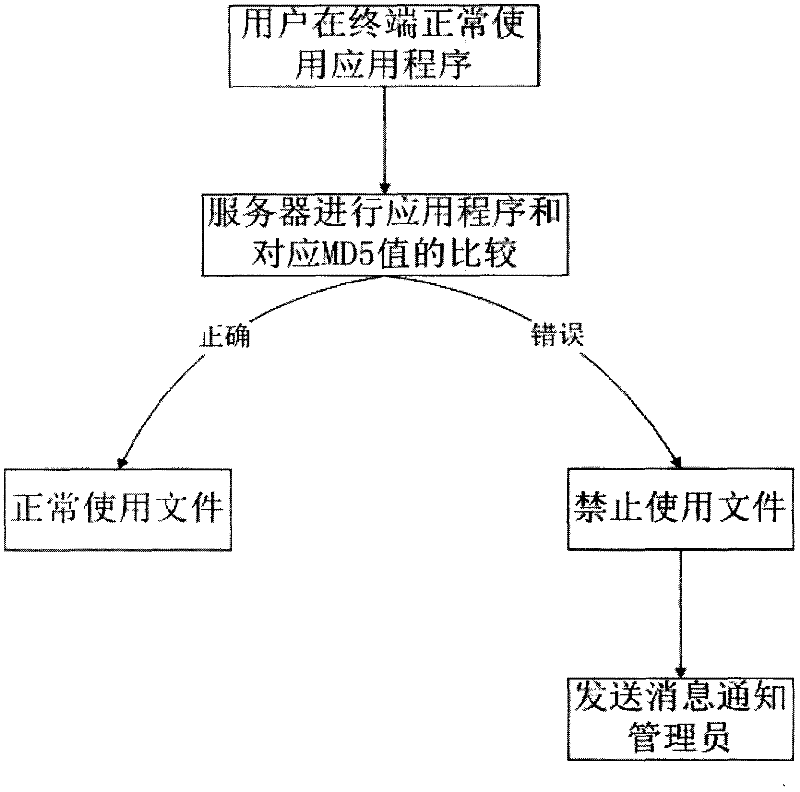
[0016] First, the clients on the terminals of each enterprise and institution collect the secret-related applications that each enterprise and institution needs to use manually or automatically, and perform MD5 on the secret-related applications organized by each terminal The calculations are uploaded to the server for storage; each enterprise and institution establishes a server to store data, and when each enterprise and institution uses its own terminal, if an untrusted program is used...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com