Method and system for monitoring group user usage
A group user and user technology, applied in the field of group user usage monitoring method and system, can solve the problem of group user usage monitoring that cannot share subscription usage, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
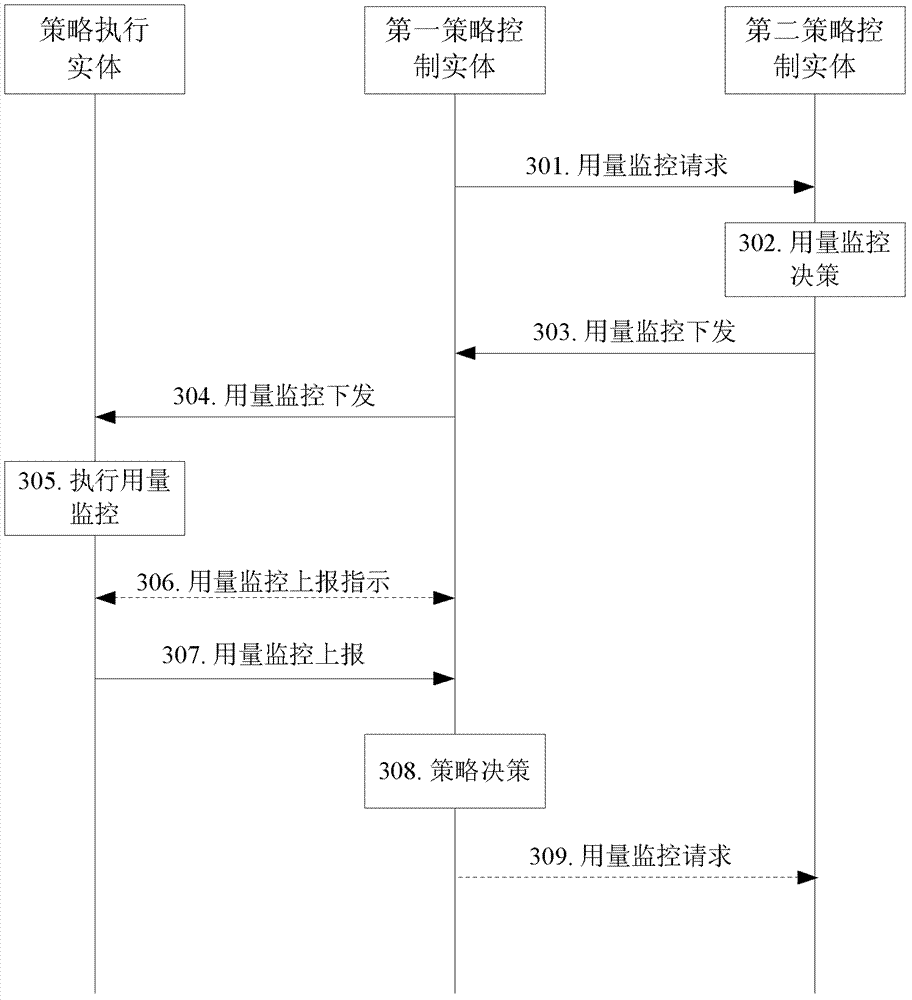
[0098] image 3 A schematic flowchart showing a method for monitoring group user usage according to an embodiment of the present invention, as shown in image 3 As shown, the process of this embodiment mainly includes the following implementation steps:
[0099] Step 301, the first policy control entity sends a usage monitoring request to the second policy control entity;
[0100] Specifically, when the first policy control entity obtains an instruction to perform usage monitoring for the user, it sends a usage monitoring request to the second policy control entity.
[0101] The first policy control entity discovers the second policy control entity through the DRA, and the DRA discovers the second policy control entity according to the user group identifier.
[0102] In step 302, the second policy control entity makes a usage monitoring decision based on the subscription amount of the user group, and assigns a monitoring key (monitoring key) and a monitoring threshold (thres...
Embodiment 2
[0111] In this embodiment, it is assumed that the user group includes UE-1 and UE-2. According to the existing UE attachment process, when UE-1 attaches to the network, select PCEF-1 and PCRF-1 (namely the first policy control entity) for its access service; when UE-2 attaches to the network, select PCEF -2 and PCRF-2 serve for its access. The SPR-1 is used to store the subscription information of the UE-1, which includes an indication that the UE-1 needs to monitor the usage of group users. SPR-2 is used to save the subscription information of UE-2, which includes an indication that UE-2 needs to monitor the usage of group users. PCRF-3 is a policy control entity (that is, a second policy control entity) that specifically provides usage monitoring for group users. When a group user is attached to the network, the network device requests PCRF-3 for usage monitoring according to the usage monitoring instruction, and the process of delivering usage monitoring by PCRF-3 is as f...
Embodiment 3
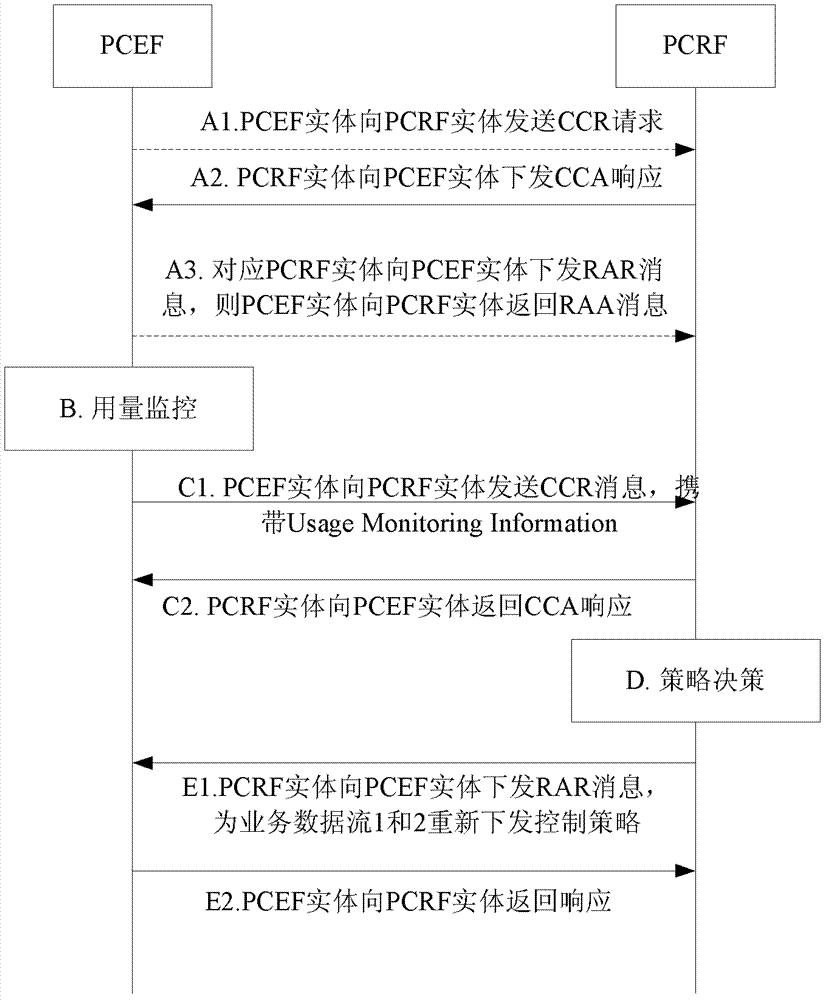
[0124] The second embodiment above provides the process of UE-1 and UE-2 in the user group attaching to the network. In this embodiment, after the UE attaches to the network, it conducts services. The PCEF monitors the usage of the UE and reports the usage monitoring, and the PCRF implements a policy adjustment process according to the usage monitoring and reporting results. For the sake of brevity, this embodiment only provides the process of implementing usage monitoring on UE-1. For the process of implementing usage monitoring for UE-2, refer to the process of implementing usage monitoring for UE-1. The process of reporting usage monitoring and adjusting policies based on usage monitoring results in this embodiment is as follows: Figure 5 As shown, the process description is as follows:
[0125] Step 501. UE-1 launches services, and PCEF-1 implements usage monitoring on UE-1.
[0126] Step 502. PCEF-1 receives an instruction from PCRF-1 to report usage monitoring.
[...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com