Usage monitoring method and system
A monitoring system and monitoring key technology, applied in the field of communications, can solve the problems of no effective solution for group users, inability to guarantee the effect of service experience, and unsuitable for unified management of group users' subscription usage.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
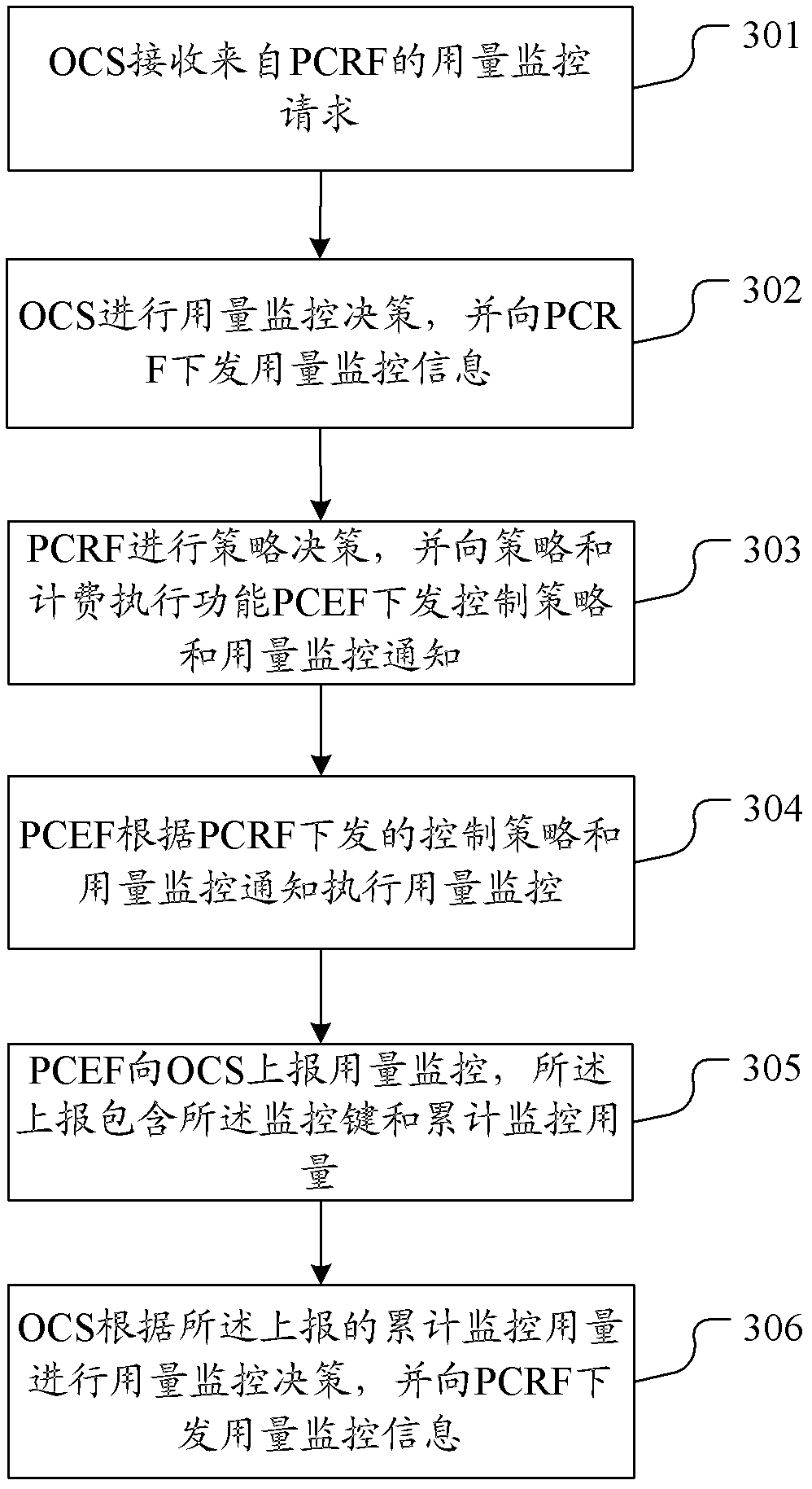
[0157] This embodiment provides an implementation process in which the PCRF sends a usage monitoring request to the OCS for the users in the group and the OCS sends usage monitoring information to the users in the group. The OCS stores group user subscription information, including information such as user group identifiers, user identifiers in the group, and group user subscription usage. Assuming that user-1 and user-2 under the same user group are attached to the network respectively, according to the existing network implementation mechanism, respectively select PCEF-1 and PCRF-1 as user-1 access services, and select PCEF-2 and PCRF-2 Access service for User-2. The user subscription information in the SPR includes an indication of whether usage monitoring needs to be started for the user. Figure 5 It is a schematic flow chart of the dosage monitoring method described in Embodiment 1 of the present invention, as Figure 5 As shown, the process includes:
[0158] Step 50...
Embodiment 2
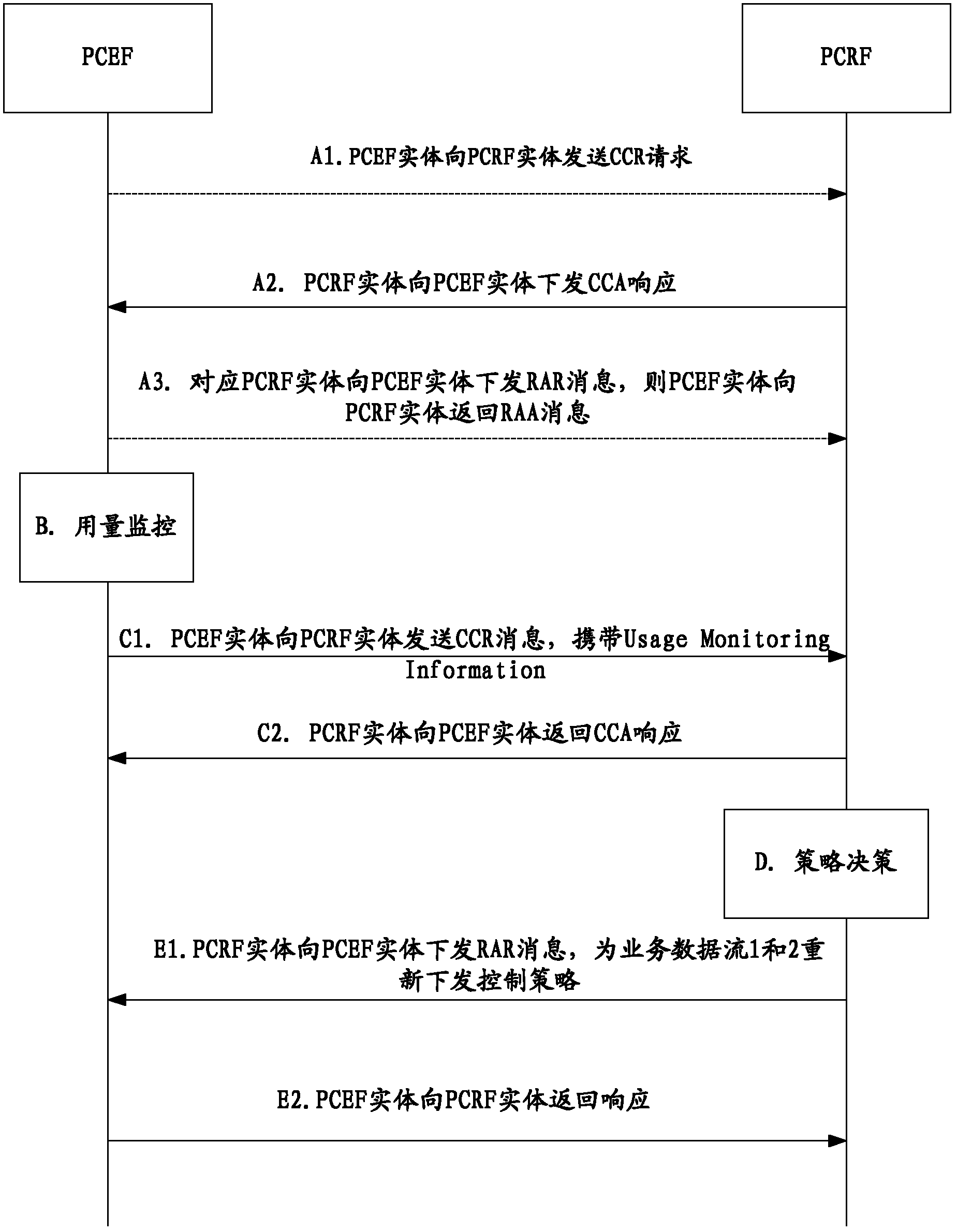
[0175] This embodiment presents the process of performing usage monitoring for the user UE-1 in the group in Embodiment 1, performing usage monitoring reporting, and PCRF executing a policy decision based on the reporting result. In this embodiment, the usage monitoring and reporting for UE-1 is taken as an example, and the usage monitoring and reporting process for user UE-2 in the group is similar to that of UE-1. Figure 6 It is a schematic flow chart of the dosage monitoring and reporting described in Embodiment 2 of the present invention, such as Figure 6 As shown, the process includes:
[0176] Step 601. UE-1 starts a service, and PCEF-1 starts usage monitoring for UE-1.
[0177]Step 602. If PCRF-1 requires PCEF-1 to report the cumulative monitoring usage for monitoring key-1 (even if the cumulative usage monitored on PCEF-1 has not yet reached the monitoring threshold threshold-1), then PCRF-1 sends PCEF-1 issued an instruction to report the monitoring usage.
[017...
Embodiment 3
[0190] This embodiment provides a process of performing usage monitoring and reporting for the user UE-1 in the group in Embodiment 1. In this embodiment, the usage monitoring and reporting of UE-1 is taken as an example, and the usage monitoring and reporting process of user UE-2 in the group is similar to that of UE-1. Figure 7 It is a schematic diagram of the usage monitoring and reporting process described in Embodiment 3 of the present invention, such as Figure 7 As shown, the process includes:
[0191] Step 701. UE-1 starts a service, and PCEF-1 starts usage monitoring for UE-1.
[0192] Step 702. If PCRF-1 requires PCEF-1 to report the cumulative monitoring usage for monitoring key-1 (even if the cumulative monitoring usage on PCEF-1 has not yet reached the monitoring threshold threshold-1), then PCRF-1 sends PCEF-1 issued an instruction to report the monitoring usage.
[0193] Step 703. If PCEF-1 receives an instruction from PCRF-1 to report monitoring usage, or w...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com