Method and system for monitoring of certificate information security
An information security and supervision system technology, applied in the field of credential information security supervision methods and systems, can solve problems such as easy copying, forgery or misappropriation, easy misappropriation, insecurity, etc., and achieve enhanced anti-counterfeiting effect, good anti-counterfeiting effect, and improved safety effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
specific Embodiment
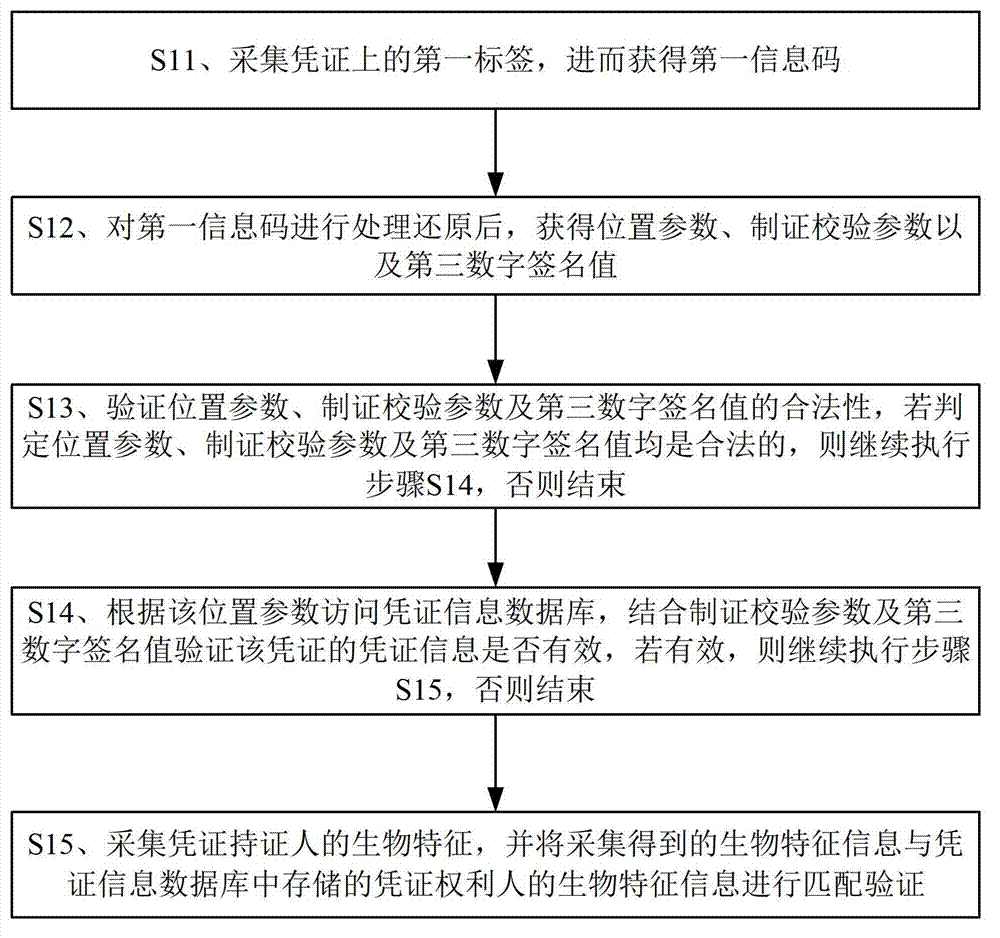
[0099] In combination with the above embodiment of the credential information security supervision system, a specific embodiment of the credential information security supervision method of the present invention is as follows:
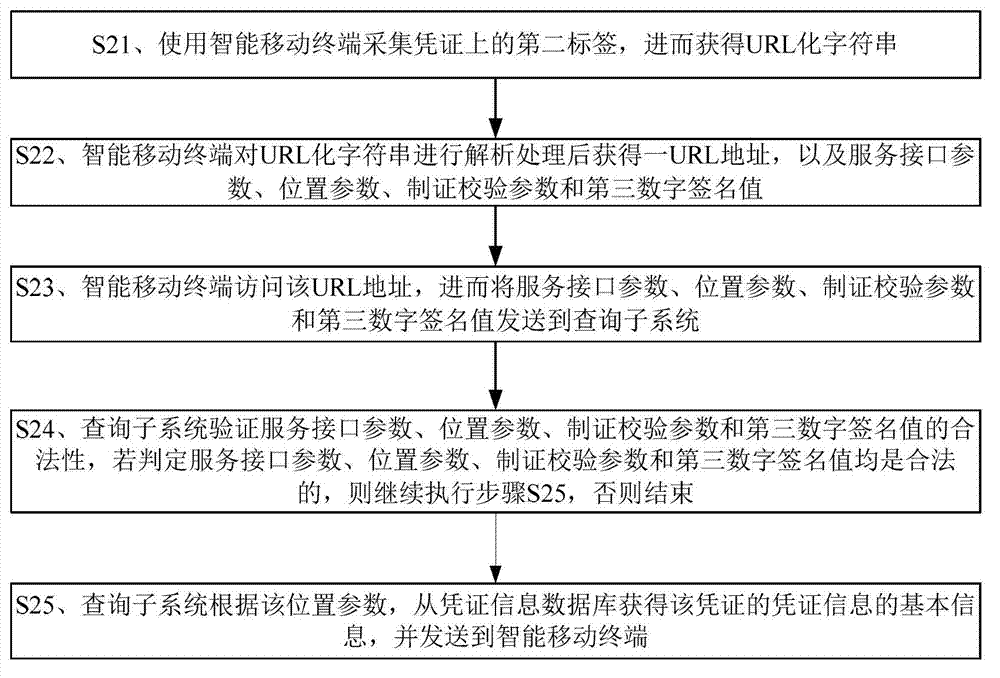
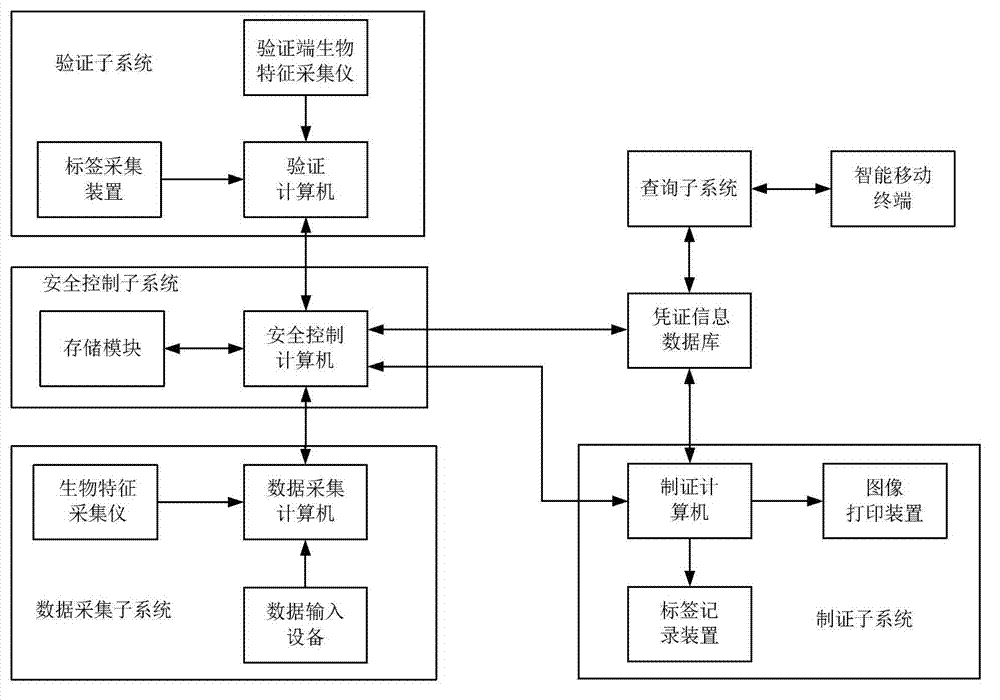
[0100] The credential information security supervision method includes a data collection step, a registration step, a certificate making step, a verification step and an authority authentication step, and after the certificate making step, an inquiry step is also included, and the data collection step includes:
[0101] S01. Collect the identity information and biometric information of the certificate obligee.
[0102] S02. After the identity information, biometric information and collection verification parameters are extracted and processed using a hash algorithm, the first private key is used to encrypt to generate a first digital signature value, and the collection verification parameters, identity information, biometric information and The first d...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com