Data processing system of voice communication
A data processing system and voice call technology, applied in the electronic field, can solve problems such as voice call security risks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
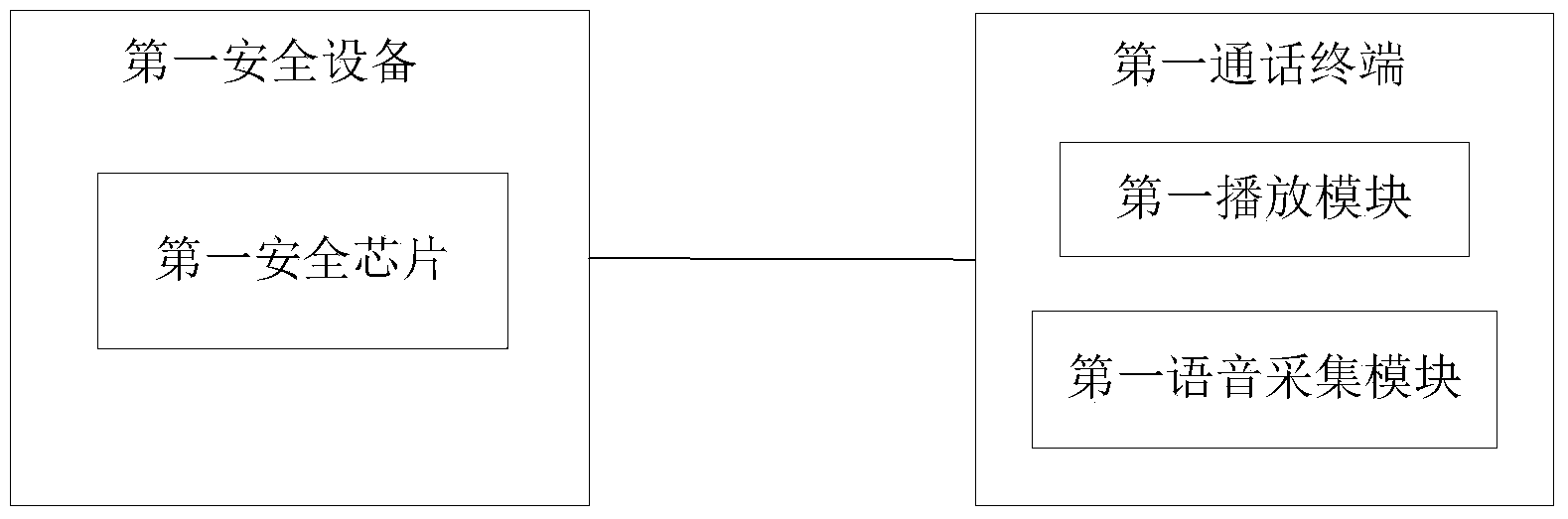
[0039] The data processing system for voice calls provided by Embodiment 1 of the present invention includes:
[0040] The first security chip is configured to generate first negotiation information, and send the first negotiation information to the first call terminal through the first communication interface, and receive second negotiation information sent by the first call terminal through the first communication interface; Calculate the first negotiation information and the second negotiation information to obtain the first call key; wherein, the first security chip is located in the first security device, and the first security device is connected to the first call terminal and is independent of the first call terminal , the second negotiation information is generated by the second security device of the second call terminal, and the first call key is used to encrypt and decrypt the voice call of the user of the first call terminal;
[0041] The first output module is use...
Embodiment 2
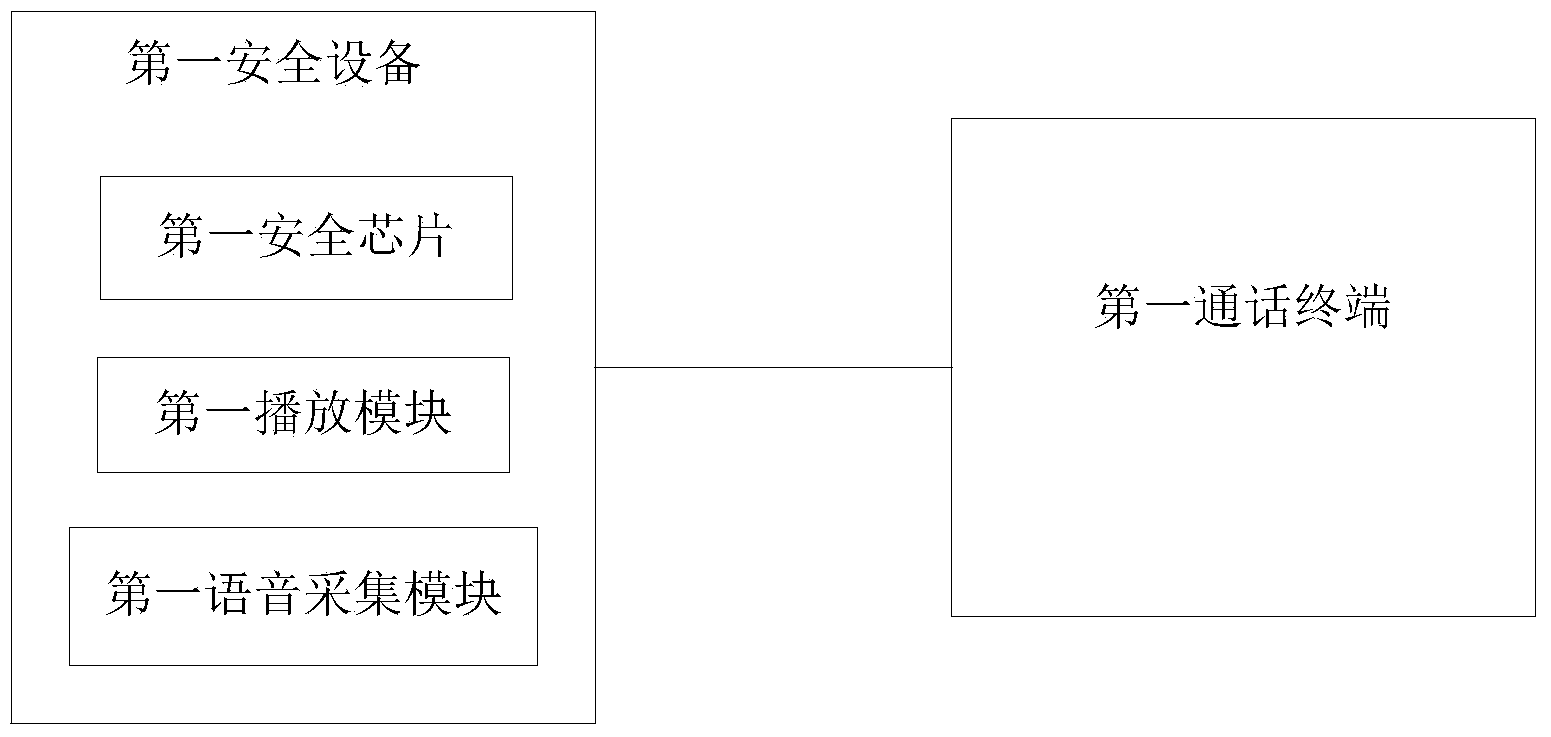
[0065] The difference between the system provided by the second embodiment of the present invention and the first embodiment above is that the receiving timing of the first confirmation instruction is different. In the first embodiment, the first security chip starts to use the first call key to pair the first If the voice call of the user of the call terminal is encrypted and decrypted, the first security chip in the second embodiment obtains the first confirmation instruction after starting to encrypt and decrypt the voice call of the user of the first call terminal, and uses the first call encryption The key continues to perform encryption and decryption operations on the voice call of the user of the first call terminal.
[0066] The system provided by Embodiment 2 of the present invention is described in detail as follows:
[0067] The voice call data processing system provided by Embodiment 2 of the present invention includes:
[0068] The first security chip is configu...
Embodiment 3
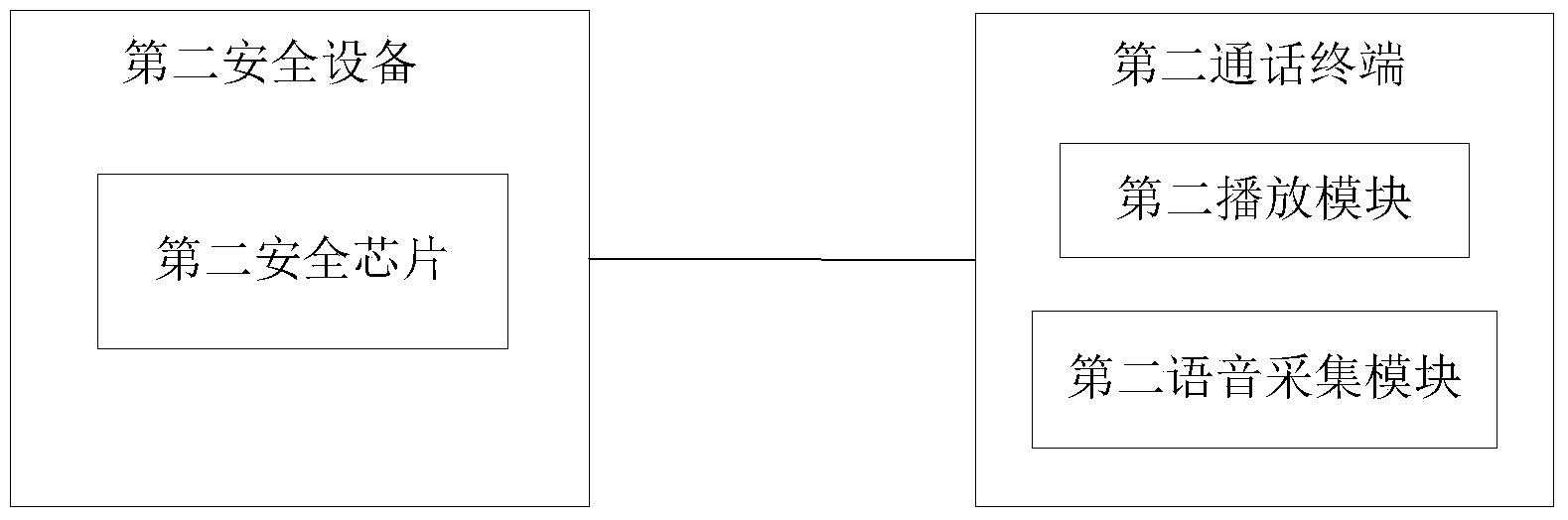
[0161] Embodiment 3 of the present invention provides a data processing system for voice calls, and the system includes:
[0162]The second security chip is configured to receive the first negotiation information sent by the second call terminal through the second communication interface, and generate second negotiation information, and send the second negotiation information to the second call terminal through the second communication interface; The first negotiation information and the second negotiation information are calculated to obtain the second call key; wherein, the second security chip is located in the second security device, and the second security device is connected to the second call terminal and is independent of the second call terminal , the first negotiation information is generated by the first security device of the first call terminal that conducts a voice call with the second call terminal, and the second call key is used to encrypt and decrypt the voice...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com