VPN access method
An access method and access request technology, applied in the field of network security, can solve the problems of large demand for hardware and low management efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
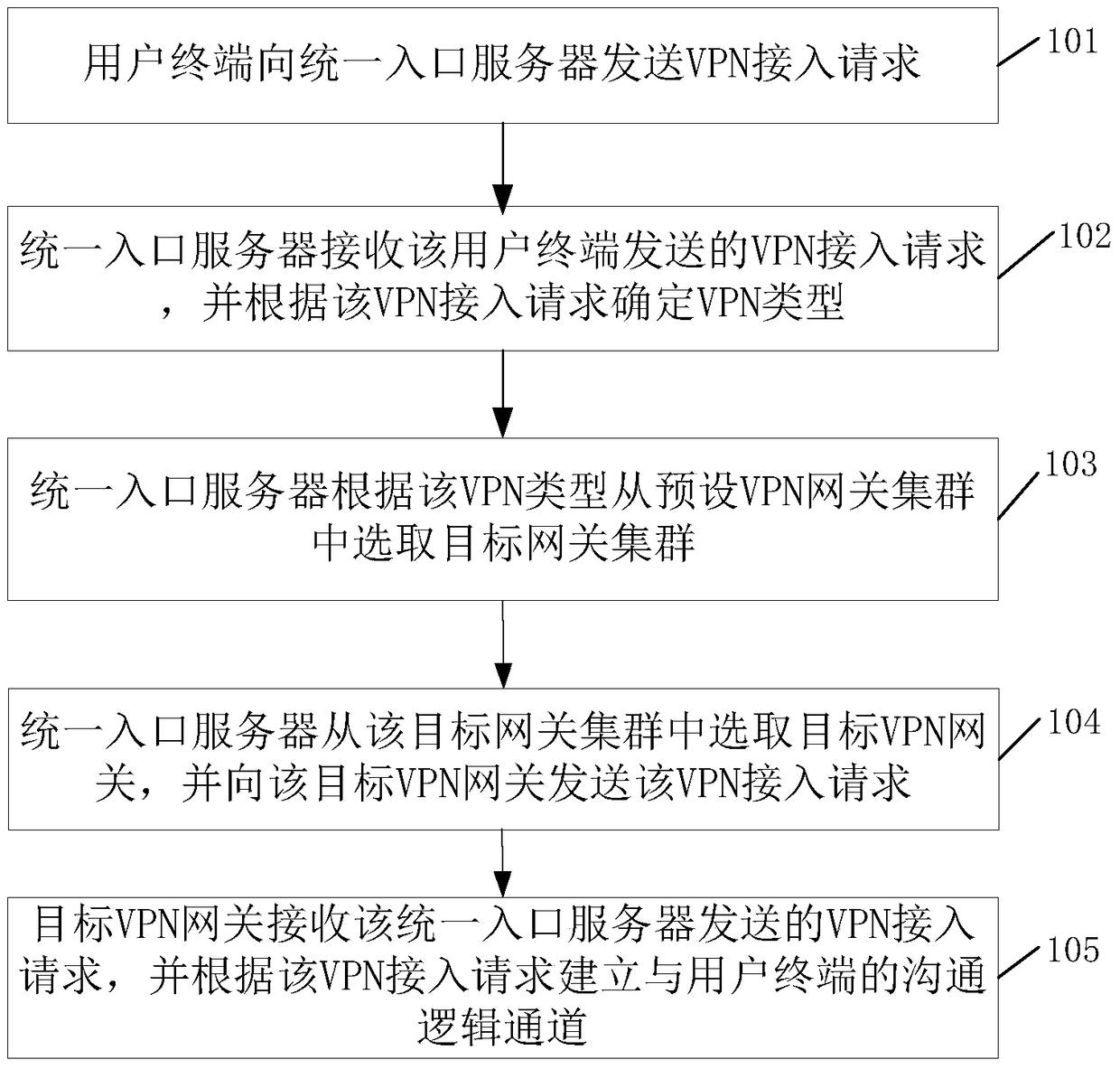
[0021] Such as figure 1 As shown, this embodiment provides a VPN access method, including:
[0022] Step 101, the user terminal sends a VPN access request to the unified portal server.
[0023] In this embodiment, the unified entry server in step 101 can uniformly receive VPN access requests sent by all user terminals, that is, all user terminals send VPN access requests to the unified entry server when they need to access the VPN. The VPN access request carries the VPN gateway type to be accessed, and the gateway type includes a Secure Socket Layer Virtual Private Network (Security Socket Layer Virtual Private Network, SSL VPN) or an Internet Protocol Security Virtual Private Network (Internet Protocol Security Virtual Private Network). Network, IPSec VPN).
[0024] In this embodiment, the user terminal needs to access each type of VPN, and different clients may be used for each type of VPN, which is not limited here.
[0025] Step 102, the unified portal server receives t...
Embodiment 2
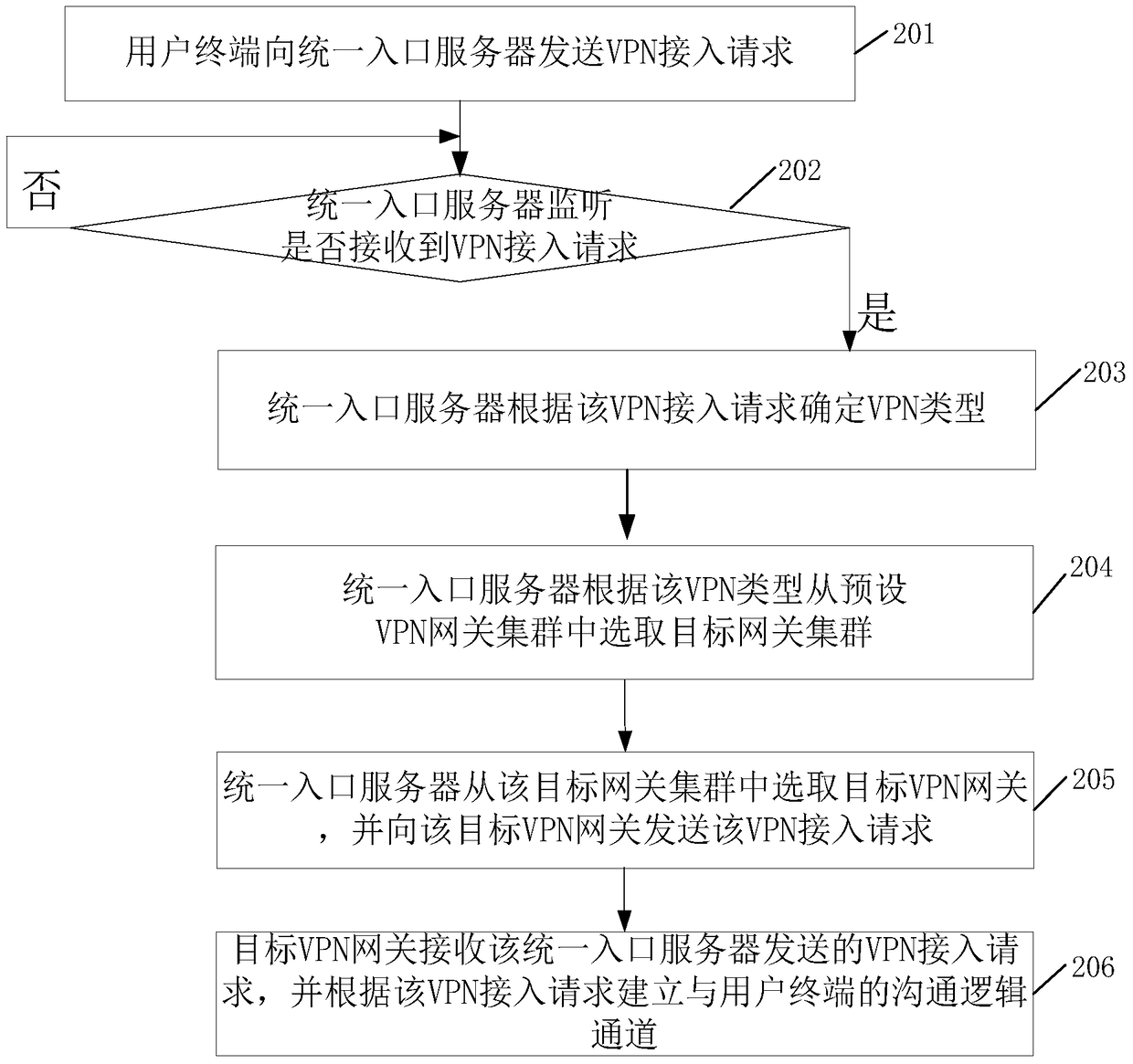
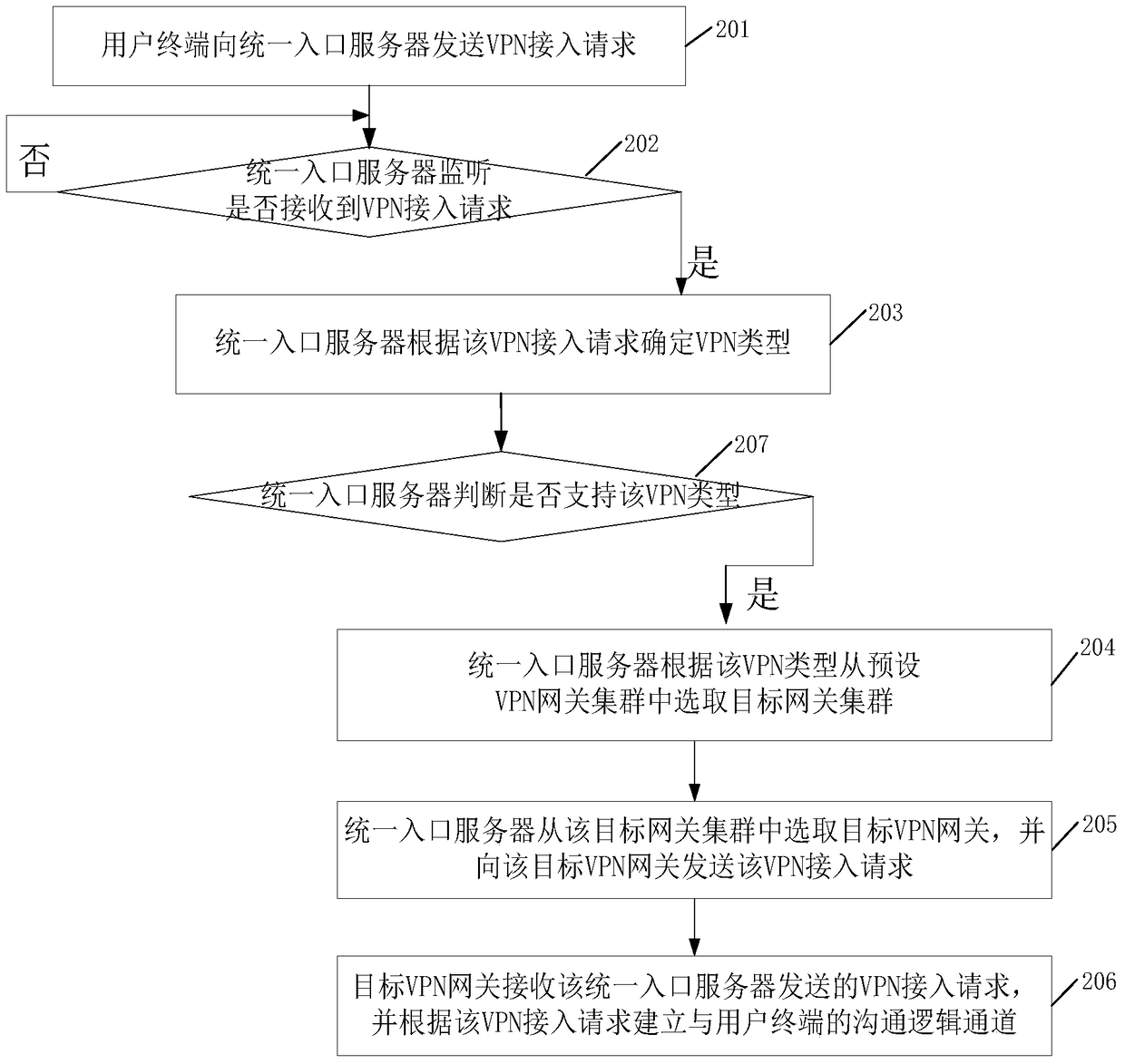
[0035] Such as figure 2 As shown, this embodiment provides a VPN access method, including:
[0036] Step 201, the user terminal sends a VPN access request to the unified portal server. The process is related to figure 1 The shown step 101 is similar and will not be repeated here.
[0037] In step 202, the unified portal server monitors whether a VPN access request is received.
[0038] In this embodiment, when the monitoring result of step 202 is yes, step 203 is performed; otherwise, step 202 is repeatedly performed.
[0039] Step 203, the unified portal server determines the VPN type according to the VPN access request.
[0040] From step 204 to step 206, the unified portal server selects a target VPN gateway according to the VPN type, and sends a VPN access request to it, and the target VPN gateway establishes a communication logical channel with the user terminal according to the request. The above process and figure 1 Steps 103 to 105 shown are similar and will not...
Embodiment 3
[0049] Such as Figure 5 As shown, the embodiment of the present invention provides a VPN access method, which is the same as figure 1 Similar to shown, except that, for identity verification purposes, also include:
[0050] Step 106, the user terminal receives the authentication information input by the user, and sends the authentication information to the target VPN gateway through the logical communication channel.
[0051] Step 107, the target VPN gateway receives the authentication information sent by the user terminal, and performs identity authentication according to the authentication information.
[0052] The present invention has the following beneficial effects: the unified entrance server receives the VPN access request sent by the user terminal, and after determining the VPN type, sends the VPN access request to the corresponding target VPN gateway, so that the target VPN gateway establishes communication logic with the user terminal channel to realize VPN acces...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com