Method for cross-over analysis of user behavior
A user and behavior technology, applied in marketing, special data processing applications, website content management, etc., can solve problems such as insufficient utilization of resources, insufficient range of user behavior data collection, small sample size, etc., and achieve accurate and rich analysis results , good psychological activities and user needs, and improve the effect of user experience
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
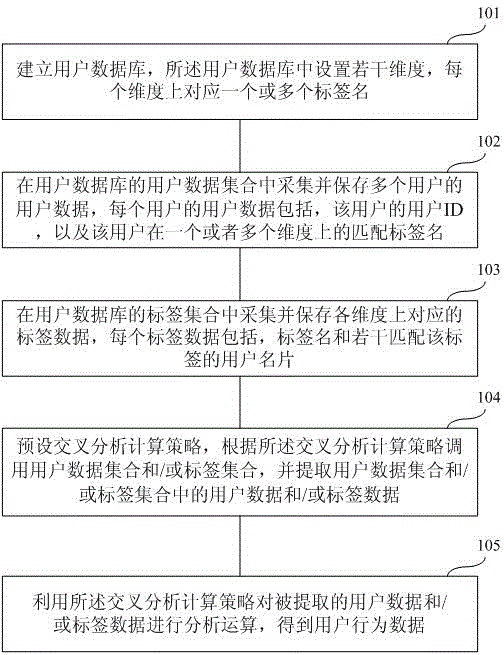
[0035] The above-mentioned cross-analysis based on user behavior is a highly open analysis method. Before analyzing user data, it is not even necessary to set an expected result. In fact, combining data to analyze user behavior is precisely to try to discover some intuitively undetectable, potential user behavior rules from a statistical point of view, so as to further speculate on the psychological needs of users. Finally, the psychological needs of users are transmitted to the product design. Thus, the design and improvement of products have a clear pertinence to the psychological needs of users. It is an effective means to improve product user experience.
[0036] According to this process, this application conducts a more in-depth and comprehensive analysis of user data. That is to set multiple dimensions for users, and collect user behavior data on a large scale; and then perform various open analysis operations on large-scale user data on each dimension. Refer to t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com