A method for assigning privileges in linux system based on capability mechanism
A privilege and capability technology, applied in the field of Linux system privilege allocation based on the capability mechanism, can solve the problems of insufficient fine-grainedness, complicated allocation and use of the capability mechanism, etc., and achieve the effect of easy management.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
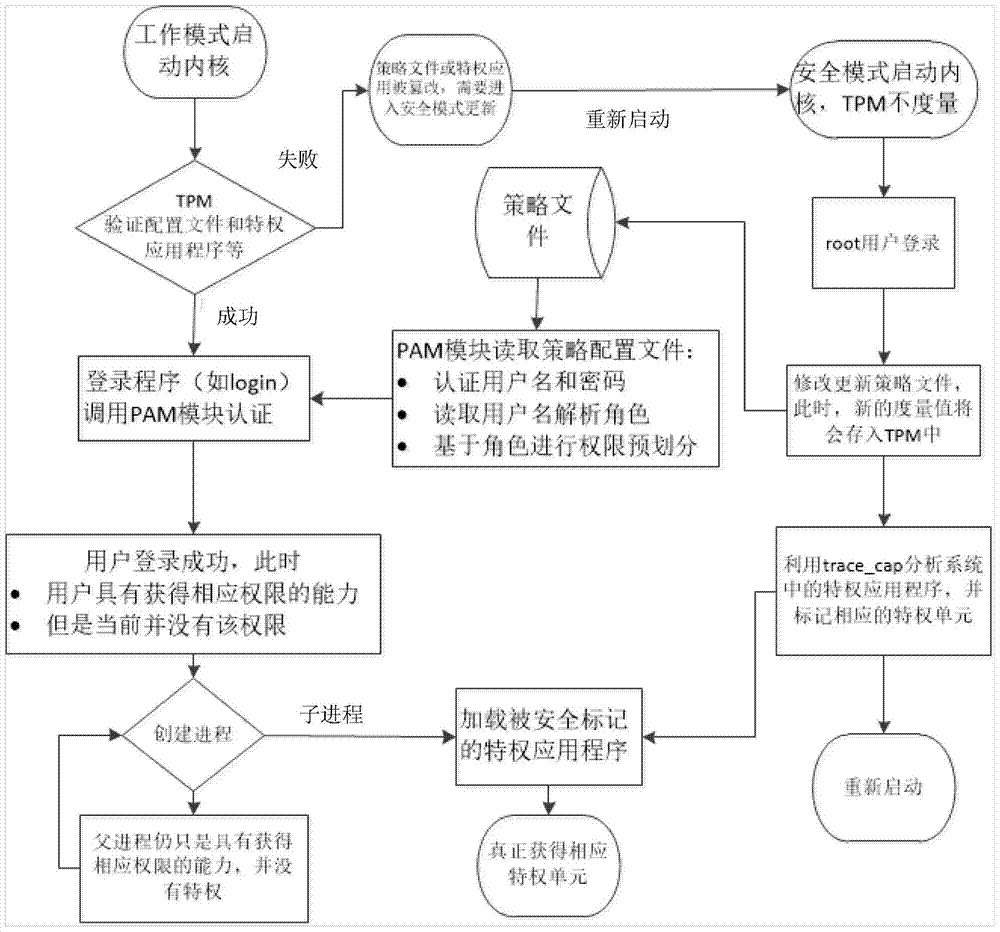
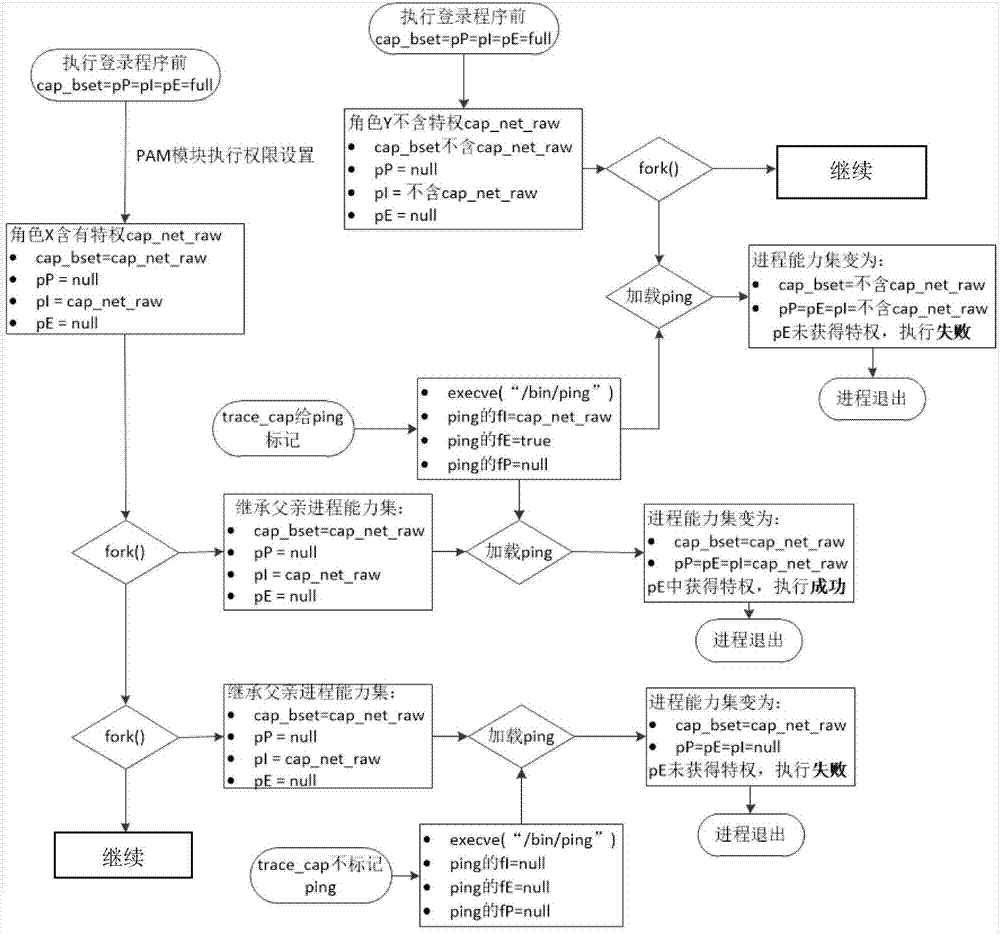
[0034] The construction of the system of the present invention is divided into two modes: working mode and security mode. In working mode, the TPM measures the configuration files and privileged applications when the system starts. After the measurement is successful, the logged-in user can automatically assume the corresponding role and obtain the corresponding capabilities when executing the corresponding privileged programs, but the user is not allowed to modify the configuration files and privileged applications. Moreover, users cannot change their own capabilities during their existence, so as to limit user rights; in safe mode, TPM does not measure when the system starts. This mode is mainly used to create or update configuration files, and to label privileged applications (that is, to add corresponding file capabilities to privileged applications), etc. See system architecture figure 1 , the implementation steps are described in detail below:
[0035] In safe mode:
...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap